In this lab, you will configure Standard ACLs, Extended ACLs, and Named ACLs in a simple network made of one router, two switches, two PCs, and one server.
This is your first hands-on ACL configuration.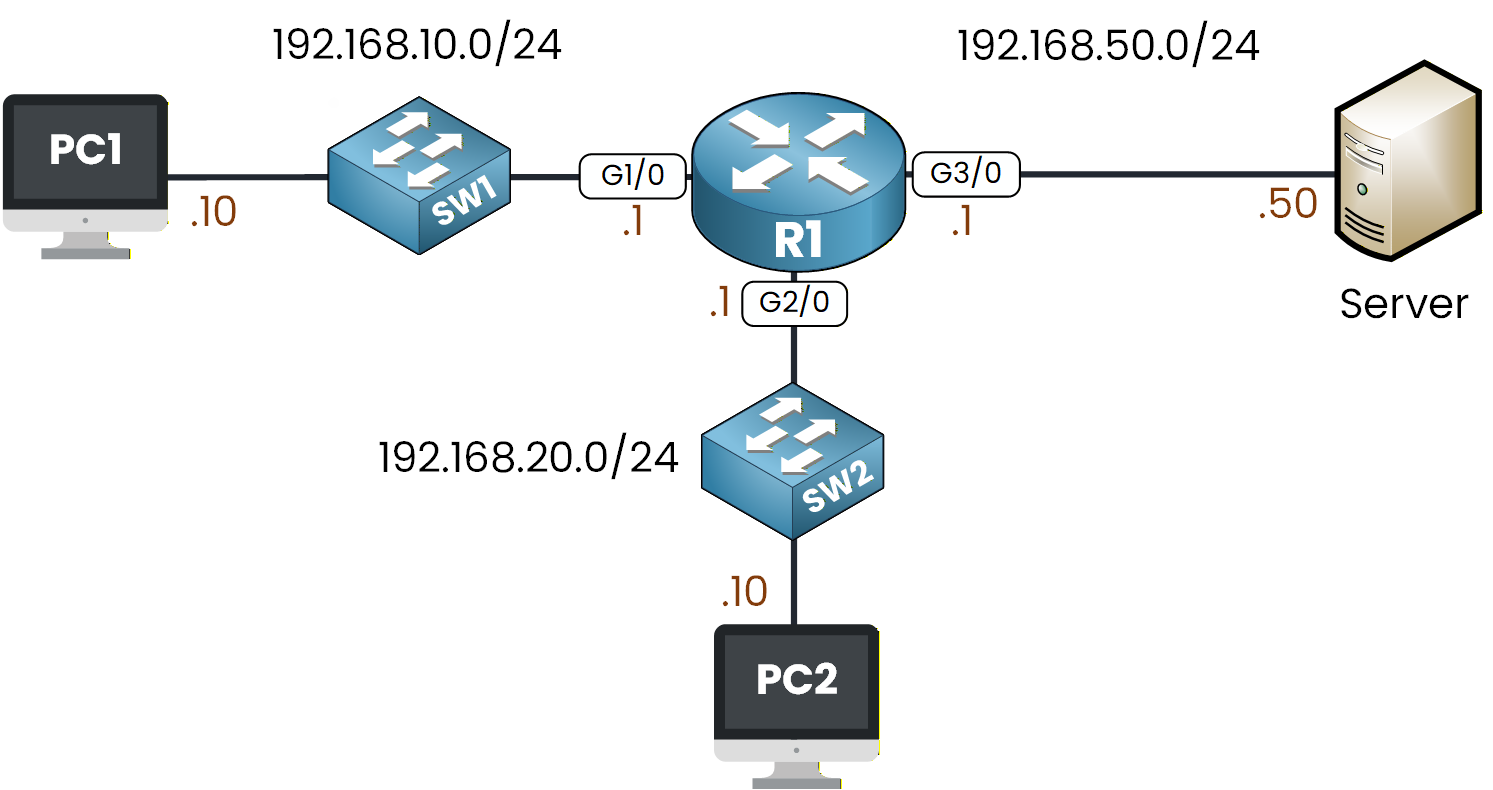
Figure 1 - ACL Configuration Lab Topology
You already learned the ACL core concepts and configuration commands in the previous lessons.
In this lab, we will apply everything in practice to see how ACLs behave on a real router.If you need a quick refresh on ACL, you can revisit these lessons:
Your objective here is to apply different types of ACLs to control traffic between the PCs and the server.
You will create filters based on source addresses, destination addresses, and specific protocols.We will walk through everything step by step directly inside Packet Tracer.
How to Begin
Before starting, download the lab file using the button at the top of the page.
The topology is already configured with all IP addresses, VLANs, and default gateways so you can focus entirely on ACLs.Lab Overview
Here is the structure we will follow throughout this lab:
Step 1 – Configure a Standard ACL
Step 2 – Configure an Extended ACL
Step 3 – Configure a Named ACL
Let’s get started.
Answer the question below
Before applying any filtering, take a moment to review the topology with me.
You can see that PC1 and PC2 are in two different subnets, and both can reach the Server through R1.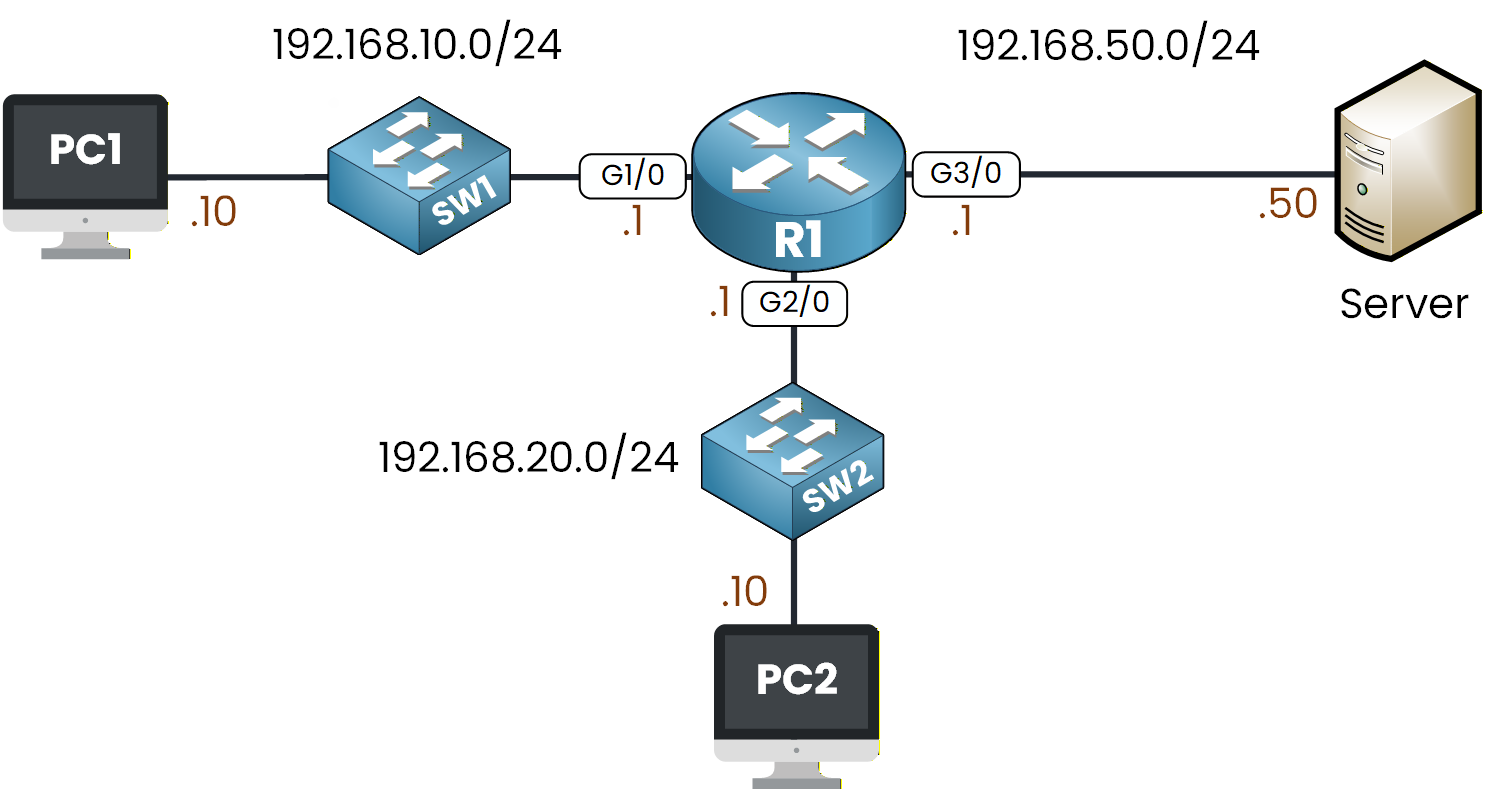
Figure 2 - ACL Configuration Lab Topology
Your objective here is simple:
I want you to block PC2's IP address from reaching the Server while still allowing PC1.
Since a Standard ACL filters traffic only based on the source IP address, we will use an Standard ACL to match PC2’s address to implement this rule.
Create the Standard ACL
Let’s begin the configuration on R1.
R1# conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)# ip access-list standard ? <1-99> Standard IP access-list number WORD Access-list name R1(config)# ip access-list standard 10For this example, we use the access-list number 10.
We start by defining the first condition, which is the deny statement.R1(config-std-nacl)# ? <1-2147483647> Sequence Number default Set a command to its defaults deny Specify packets to reject exit Exit from access-list configuration mode no Negate a command or set its defaults permit Specify packets to forward remark Access list entry commentLet’s deny PC2’s IP address.
R1(config-std-nacl)# deny host 192.168.20.10Now that PC2 is blocked, we allow all remaining traffic so the network continues to work normally.
R1(config-std-nacl)# permit ? A.B.C.D Address to match any Any source host host A single host address R1(config-std-nacl)# permit any R1(config-std-nacl)# endYour Standard ACL is now defined. You can confirm it with:
R1# show ip access-lists Standard IP access list 10 10 deny host 192.168.20.10 20 permit anyAt this stage, R1 knows what traffic to block, but nothing is enforced yet.
An ACL only becomes active once you apply it to an interface.Apply the Standard ACL
Standard ACLs should be placed as close to the destination as possible.
In this lab, the destination is the Server network 192.168.50.0/24, reachable through interface G3/0.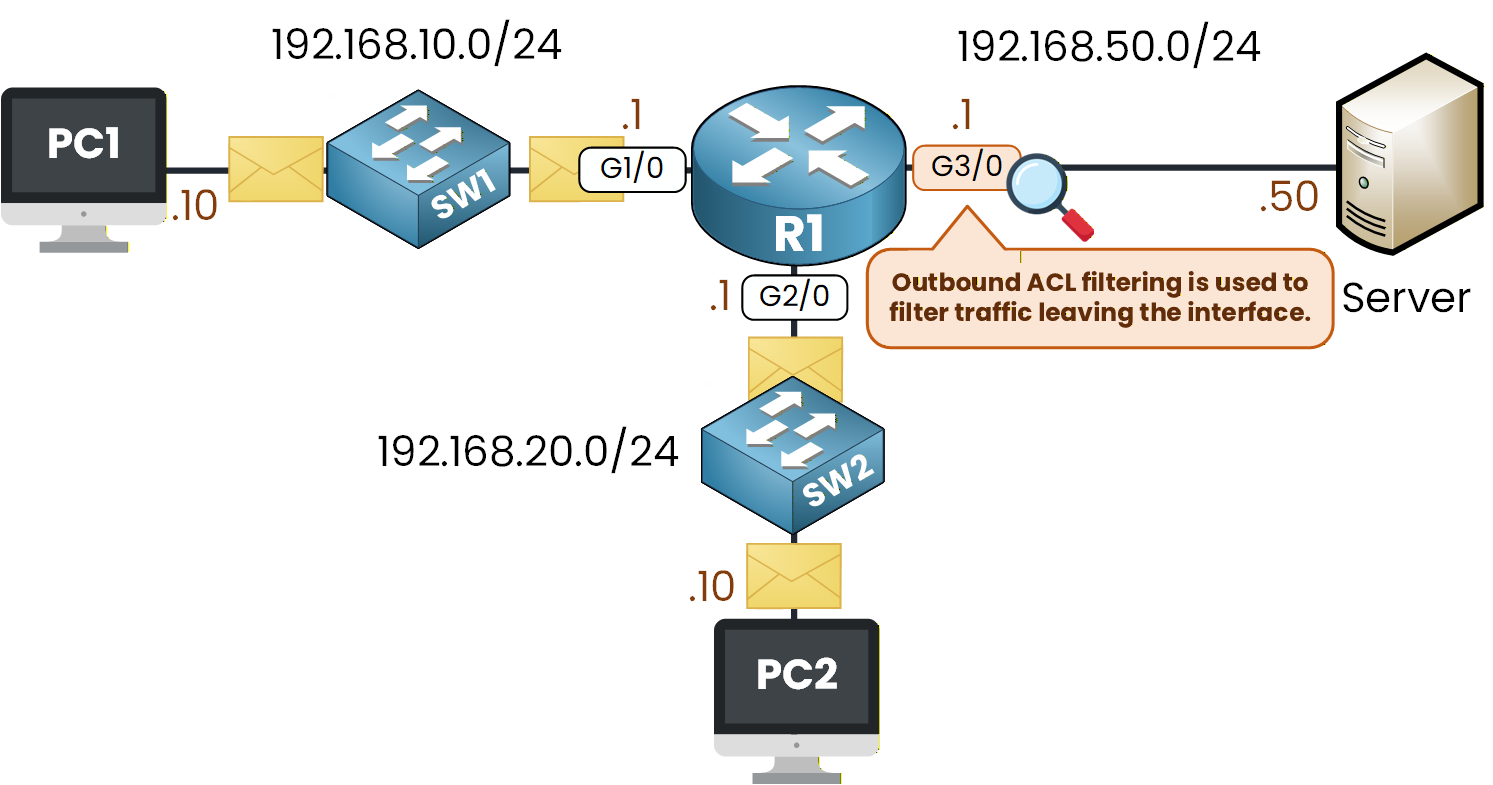
Figure 3 - Outbound ACL Filtering Behavior
We apply the ACL outbound on that interface.
R1(config)# int g3/0 R1(config-if)# ip ? access-group Specify access control for packets address Set the IP address of an interface authentication authentication subcommands R1(config-if)# ip access-group ? <1-199> IP access list (standard or extended) WORD Access-list nameHere, we attach ACL 10 and then we choose the direction:
R1(config-if)# ip access-group 10 ? in inbound packets out outbound packetsThis gives us the final command:
R1(config)# interface g3/0 R1(config-if)# ip access-group 10 out R1(config-if)# endYour filtering rule is now active.
Verify the ACL Is Applied
Before testing traffic, let’s make sure the ACL is correctly attached to the interface.
R1# show ip interface g3/0 GigabitEthernet3/0 is up, line protocol is up (connected) Internet address is 192.168.50.1/24 Broadcast address is 255.255.255.255 Address determined by setup command MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Outgoing access list is 10 Inbound access list is not setLook for the line: Outgoing access list is 10.
If you see it, your ACL is exactly where it should be.
If not, simply go back and reapply it on the correct interface.Test the ACL
Now let’s check if your filtering works as expected.
First, from PC1:
C:\> ping 192.168.50.50 Pinging 192.168.50.50 with 32 bytes of data: Reply from 192.168.50.50: bytes=32 time<1ms TTL=127 Reply from 192.168.50.50: bytes=32 time<1ms TTL=127 Reply from 192.168.50.50: bytes=32 time<1ms TTL=127PC1 should reach the Server normally.
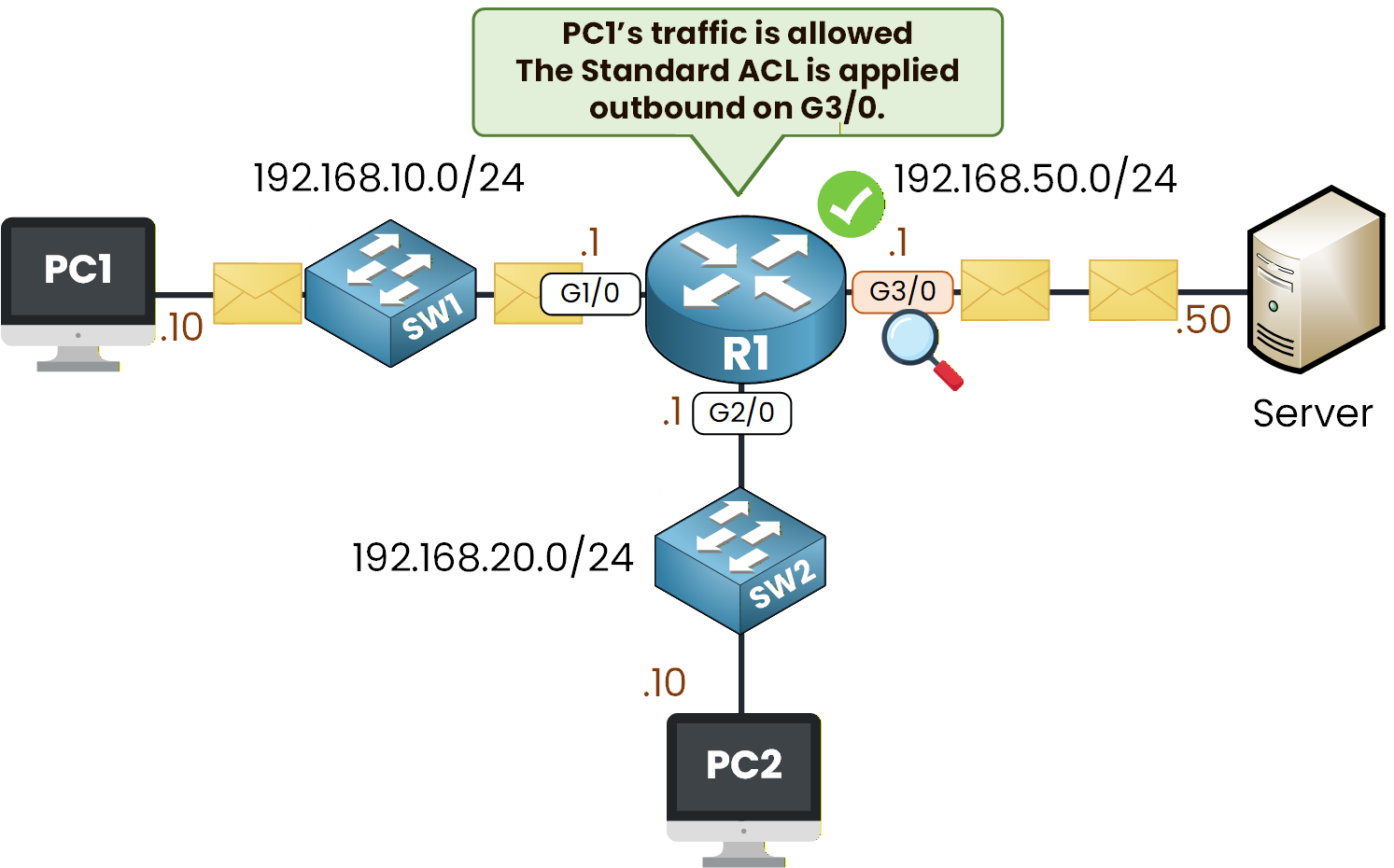
Figure 4 - Outbound ACL Filtering Behavior on PC1 Traffic
From PC2, try the same command:
C:\> ping 192.168.50.50 Pinging 192.168.50.50 with 32 bytes of data: Reply from 192.168.20.1: Destination host unreachable.This one should be blocked.
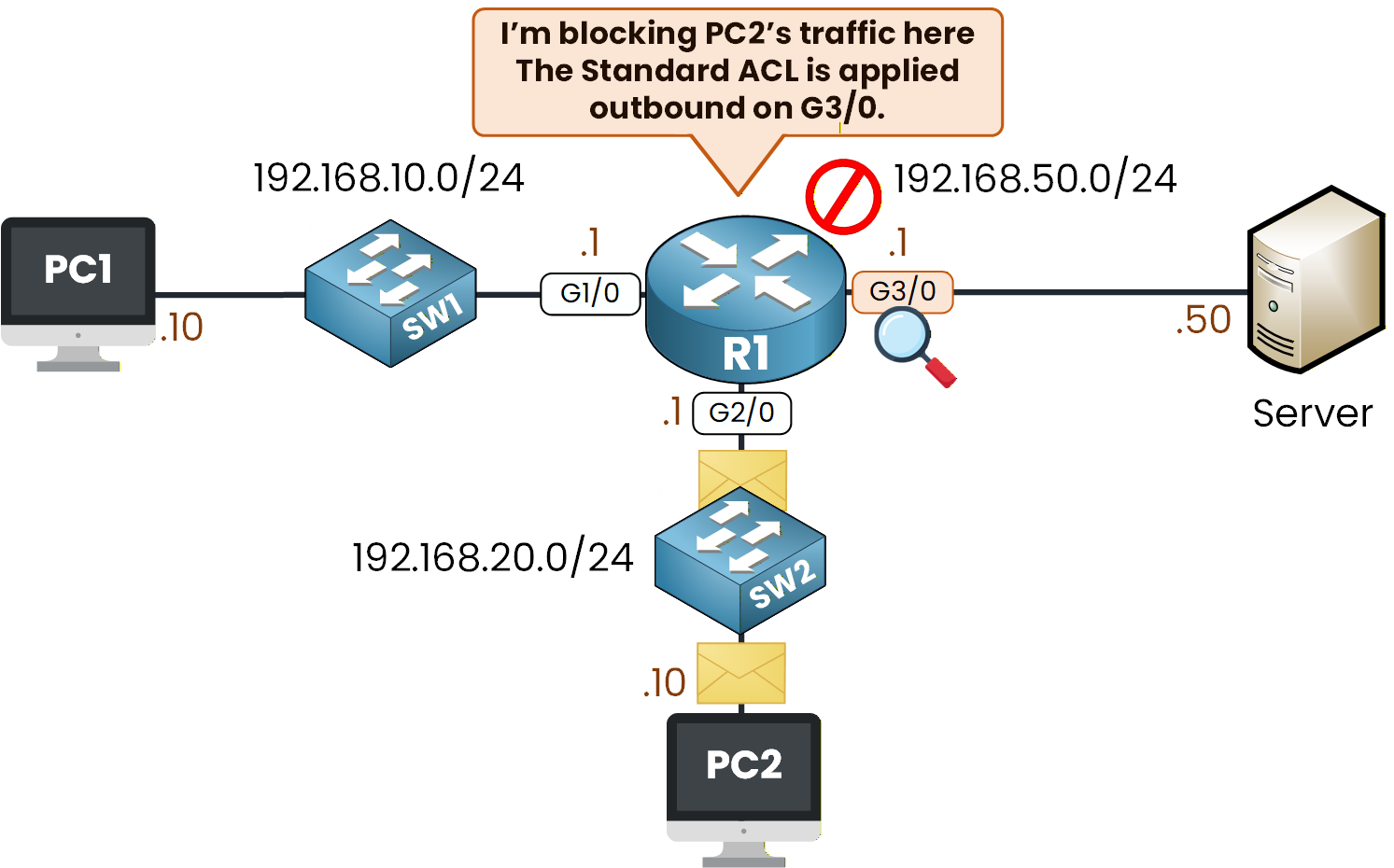
Figure 5 - Outbound ACL Filtering Behavior on PC2 Traffic
If you observe these two behaviors, your Standard ACL is correctly configured and applied.
Now, let's move on to step two.Answer the question below
On which interface is the ACL applied?
Before starting this step, remove the Standard ACL from the interface.
If it stays applied on R1, it will continue blocking traffic toward the Server and you won’t see the correct behavior for the Extended ACL.Detach the ACL from interface g3/0:
R1(config)# interface g3/0 R1(config-if)# no ip access-group 10 out R1(config-if)# exitThe interface is now clean and ready for the next configuration.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally