When managing a network, one of your key responsibilities is deciding what traffic should be allowed and what should be blocked. That’s exactly what Access Control Lists (ACLs) are designed for.
An ACL is a set of rules that filters traffic based on specific conditions. These rules are applied on Cisco routers or Layer 3 switches to permit or deny packets, helping you control how devices communicate across different parts of your network.ACLs and OSI Layers
There are two main types of ACLs, each operating at different layers of the OSI model, as shown in Figure 1.
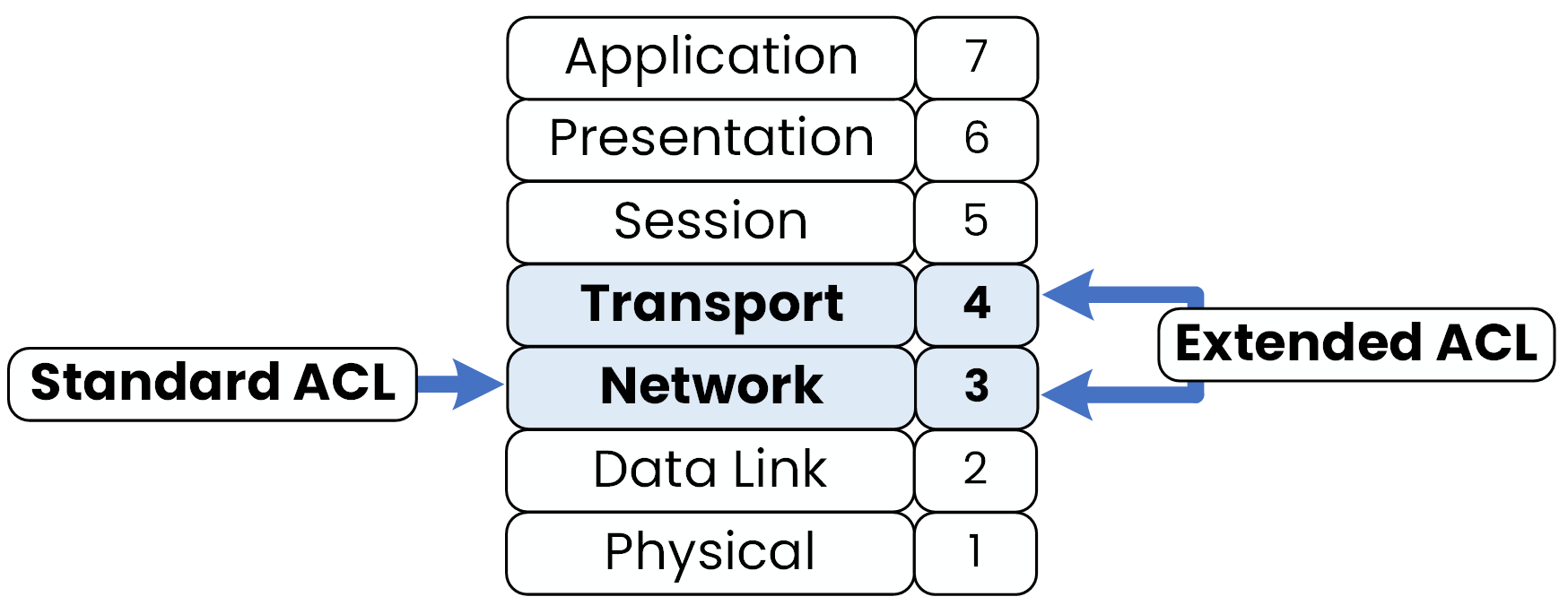
Figure 1 – ACLs and OSI Layers
Standard ACLs operate at Layer 3 (Network Layer) and filter traffic based only on the source IP address.
Extended ACLs operate at both Layer 3 and Layer 4 (Network and Transport Layers), allowing filtering based on source and destination IP, protocols, and even port numbers.
Real-World Example — Inside a Company Network
Imagine you’re the network administrator of a mid-size company. Each department has its own VLAN connected to a core router:
VLAN 10 — Legal Department: 192.168.1.0/24
VLAN 20 — HR Department: 192.168.2.0/24
VLAN 30 — Server VLAN: 192.168.3.0/24
The Legal department needs access to the Legal Server in VLAN 30, but HR must not reach it for confidentiality reasons. ACLs are the perfect solution to enforce this rule directly on the router.
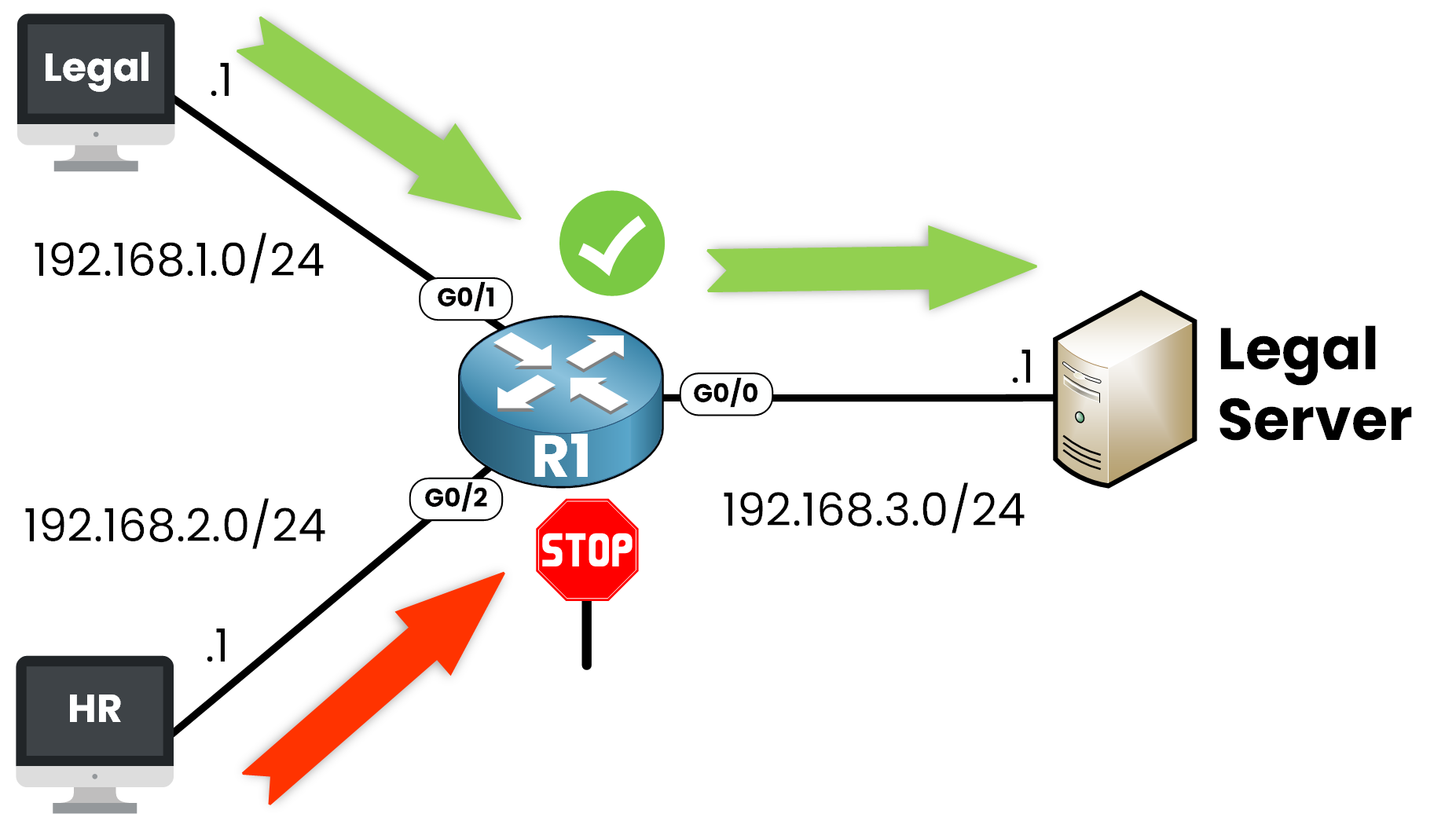
Figure 2 – Standard ACL Example
As shown in Figure 2, the router sits between departments and the server VLAN, making it the ideal point to control traffic flow.
Configuration Example
Here’s how a basic Standard ACL would look:
R1# conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)# ip access-list standard 10 R1(config-std-nacl)# permit 192.168.1.0 0.0.0.255 R1(config-std-nacl)# deny 192.168.2.0 0.0.0.255What’s Happening Here?
10 is the ACL ID number.
The Legal network (192.168.1.0/24) is allowed to access the server VLAN.
The HR network (192.168.2.0/24) is explicitly denied.
This configuration enforces department-based access control, a common best practice in enterprise environments to ensure network segmentation and data protection.
Key Takeway
ACLs give you the power to define who can talk to whom on the network.
They act as gatekeepers, ensuring that each department or service communicates only where it should.Now that you’ve seen how ACLs are used in a real company network, let’s look at how these rules are structured, starting with the Access Control Entries (ACEs) that make up every ACL.
Answer the question below
ACLs can be applied on routers and on which other device?
Each rule in an ACL is called an Access Control Entry (ACE).
You can think of an ACL as a list, and each ACE is one line in that list, an individual rule that tells the router whether to permit or deny specific traffic.Example Breakdown
Let’s take the same example from earlier to understand how ACEs work.
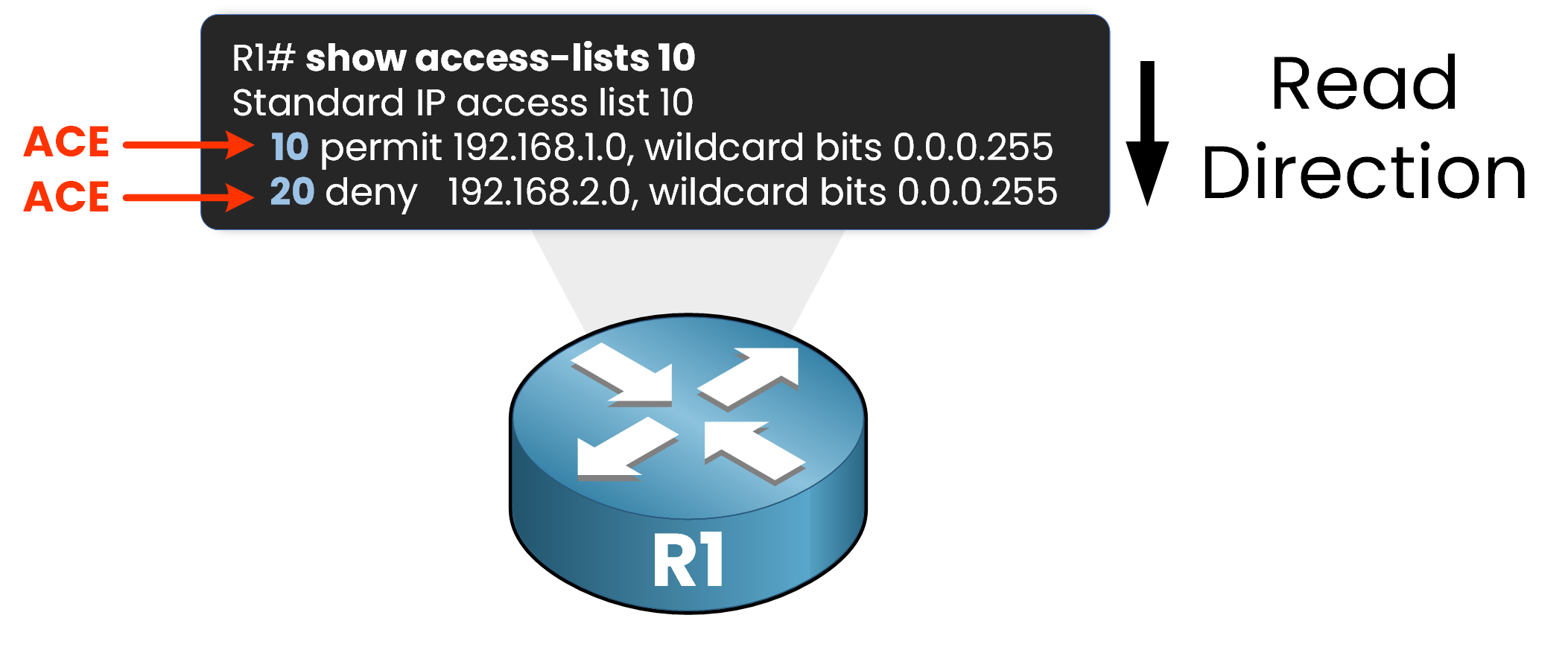
Figure 3 – Access Control Entries (ACEs)
In this access list, we have two ACEs that define our filtering rules:
ACE 10: Permits traffic from the 192.168.1.0/24 network.
ACE 20: Denies traffic from the 192.168.2.0/24 network.
When the router processes packets, it evaluates them line by line against each ACE in order.
What About That Mask?
You might have noticed something unusual in the syntax:
the mask used in an ACE doesn’t look like a typical subnet mask.
That’s because ACLs use wildcard masks, not subnet masks.
Wildcard masks define which bits of an IP address must match and which bits can vary, giving you more flexibility when matching traffic.What Is a Wildcard Mask?
A wildcard mask is the inverse of a subnet mask.
Where a subnet mask uses 1s to mark network bits, a wildcard mask uses 0s to mark the bits that must match exactly.Subnet Mask
Wildcard Mask
Matches
255.255.255.0
0.0.0.255
All IPs in 192.168.1.0/24
255.255.255.255
0.0.0.0
One specific IP address
Table 1 – Subnet Mask vs Wildcard Mask
Applying It to Our Example
Let’s look at our earlier ACL line:
permit 192.168.1.0 0.0.0.255This means:
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally