Named ACL configuration is essential when you want more control over network traffic using readable and organized access lists on Cisco routers.
When you're looking at a router configuration and you see something like:
access-list 101 permit tcp 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 eq 443…it’s hard to tell what that rule is for.
That’s the problem with numbered ACLs.
In a real network, you might have dozens of access lists. And when they’re all identified by numbers, it becomes difficult to know which rule does what, especially when you're troubleshooting or reviewing someone else’s configuration.
By using using a name instead of a number gives immediate context to your configuration.
For example:
ip access-list extended ALLOW_HTTPS_TRAFFICJust by reading the name, you immediately know this ACL is designed to allow HTTPS access to the Legal Server even before checking the rule itself.
Back to the Basics
To understand how Named ACLs work, you first need to understand how ACLs are structured.
There are two types of ACLs:
Standard ACLs: which filter traffic based only on the source IP address.
Extended ACLs: which can filter based on source, destination, protocol, and port.
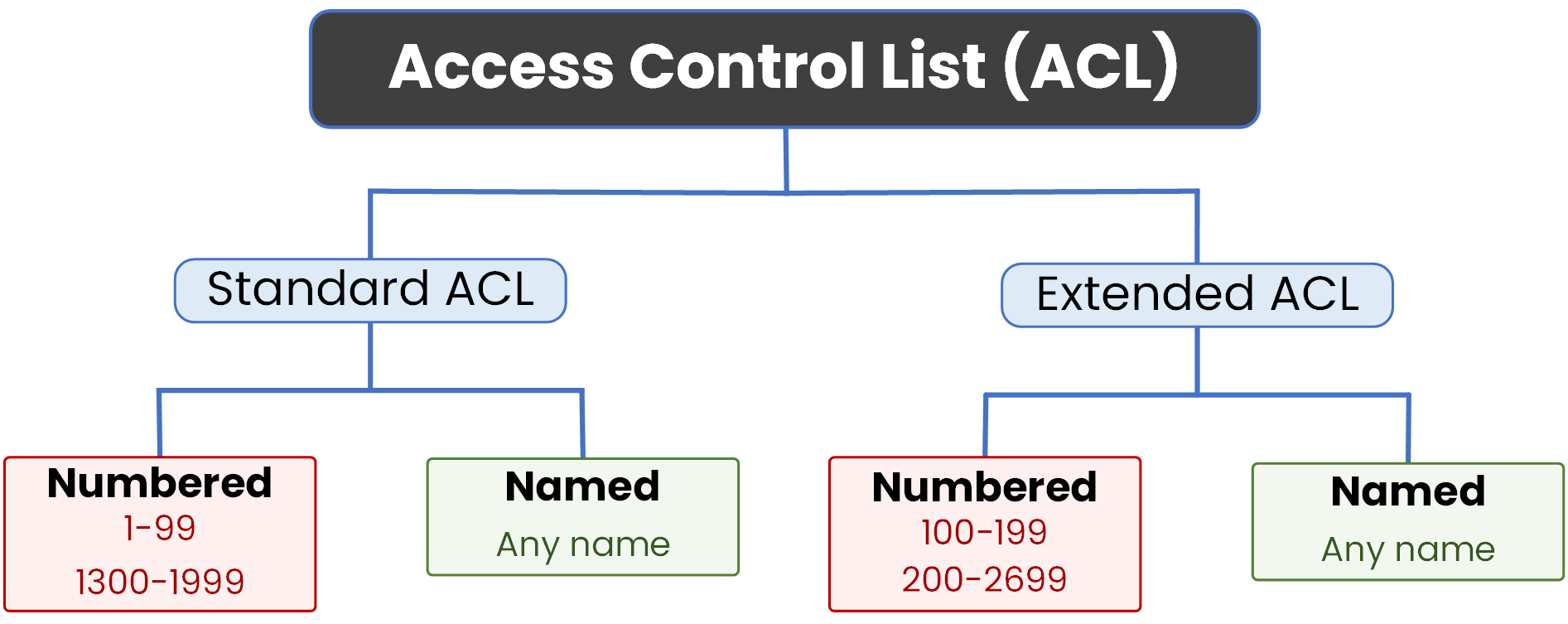
Figure 1 – ACL Types and Naming Options
Each type can be configured in two different ways:
Using a number: like access-list 10
Using a name: like ip access-list standard BLOCK_HR_ACCESS
In this lesson, we'll focus on how to create access lists using names instead of numbers.
Let’s begin with the first case: the Named Standard ACL.
Answer the question below
What does a named ACL use instead of a number?
Let’s now see how to create a standard ACL, but this time using a name instead of a number.
Scenario
You have two departments in your network:
The Legal department uses the 192.168.1.0/24 network
The HR department uses the 192.168.2.0/24 network
A Legal server is located in 192.168.3.0/24
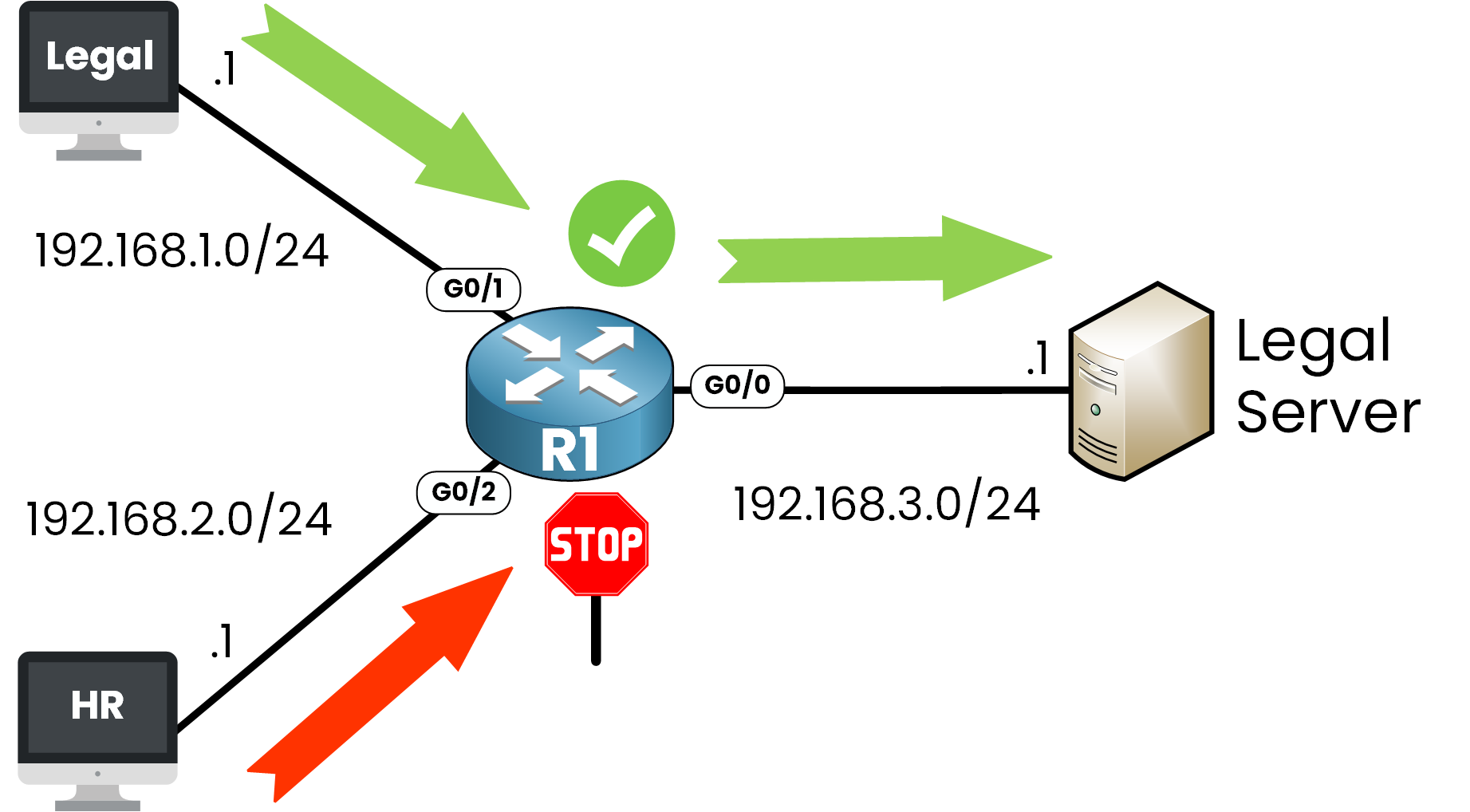
Figure 2 – Named Standard ACL Scenario
The goal is simple:
Allow the Legal department to access the server and deny access to the HR department.This time, instead of using something like access-list 10, we’ll create a Named Standard ACL called ALLOW_LEGAL_DENY_HR so its purpose is immediately clear.
Step 1 — Enter global configuration mode
Start by creating a standard named ACL in configuration mode:
R1# conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)# ip access-list standard ALLOW_LEGAL_DENY_HRThis command creates an ACL in named standard mode. Now we can define the rules inside.
Step 2 — Define the Rules
Allow the Legal department and deny the HR department:
R1(config-std-nacl)# permit 192.168.1.0 0.0.0.255 R1(config-std-nacl)# deny 192.168.2.0 0.0.0.255 R1(config-std-nacl)# exitThis named ACL does the same thing as a traditional numbered ACL, but its name clearly shows the intent.
The permit rule allows access for Legal, while the deny rule blocks HR.Answer the question below
What name is used for the named standard ACL in this example?
Just like numbered ACLs, a named ACL won’t have any effect unless it’s applied to an interface.
Standard ACLs should be placed as close as possible to the destination, since they only filter on the source IP address. Placing them too close to the source could unintentionally block traffic to multiple destinations.
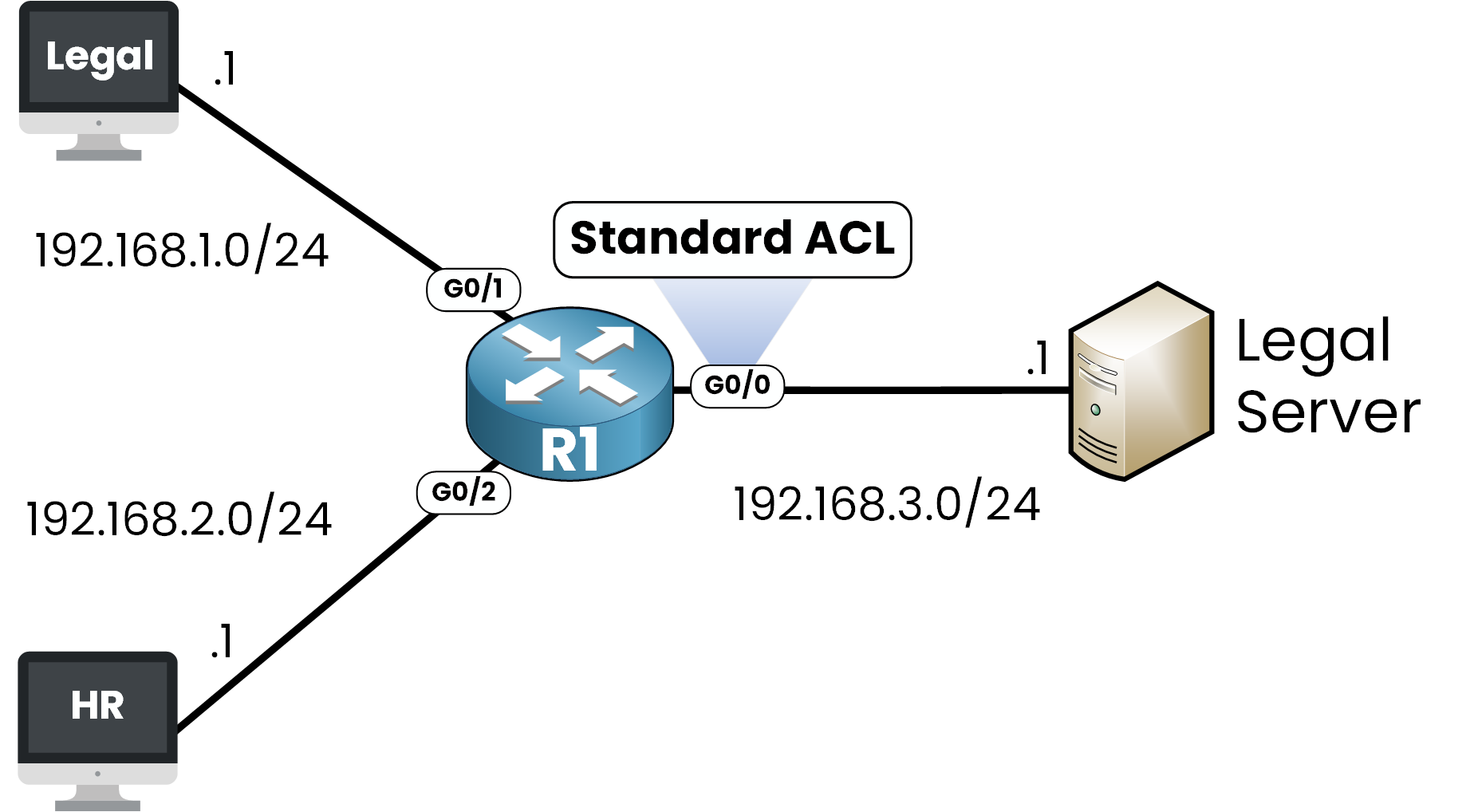
Figure 3 – Named Standard ACL Placement
In our example, the traffic from the Legal and HR departments passes through interface G0/0 before reaching the server.
Step 1 — Enter Interface Configuration Mode
We start by selecting the correct interface:
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Named ACL
Named ACLs let you replace numbered access lists with clear, descriptive names that make configurations easier to read and maintain. In this lesson, you’ll learn how to create named standard and extended ACLs, apply them on Cisco devices, and verify their operation.