The OSI Model, created in the 1980s, is a framework that explains how devices communicate across a network, step by step through seven layers.
Its strength is in its layered structure. This divides communication into seven layers, each with its own responsibilities.
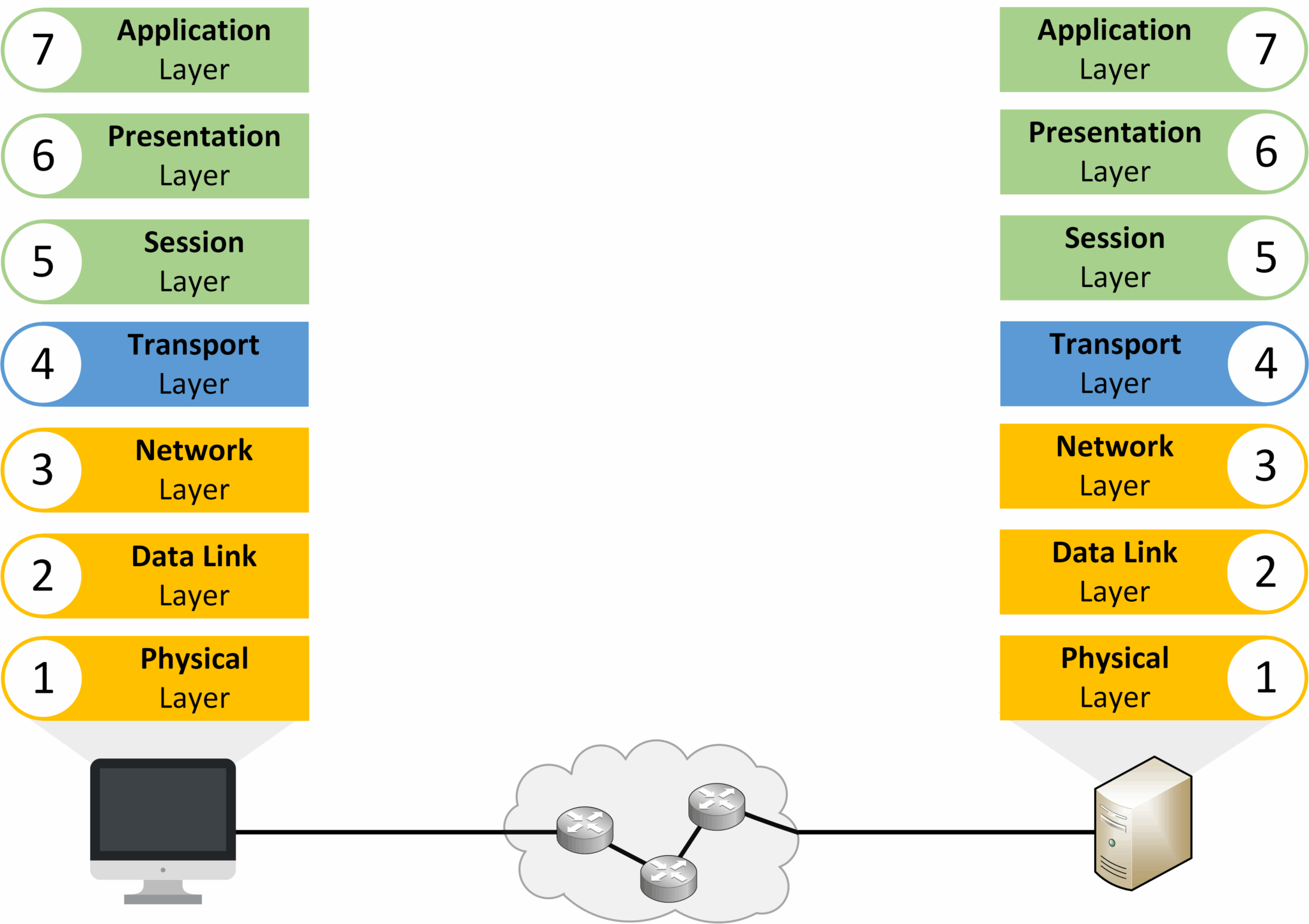
Figure 1 – OSI Model
The OSI model helps us understand network communication and troubleshoot issues. But it serves as a theoretical reference above all else. The TCP/IP model is the standard in networking. It outlines the protocols for transferring data between devices.
Answer the question below
The OSI model is built on seven layers, each with a specific role in communication.
To understand how data moves through the network, you need to know two key processes: encapsulation and decapsulation.Encapsulation
When you send data (for example, a file or a message), it travels down through the OSI layers on your device.
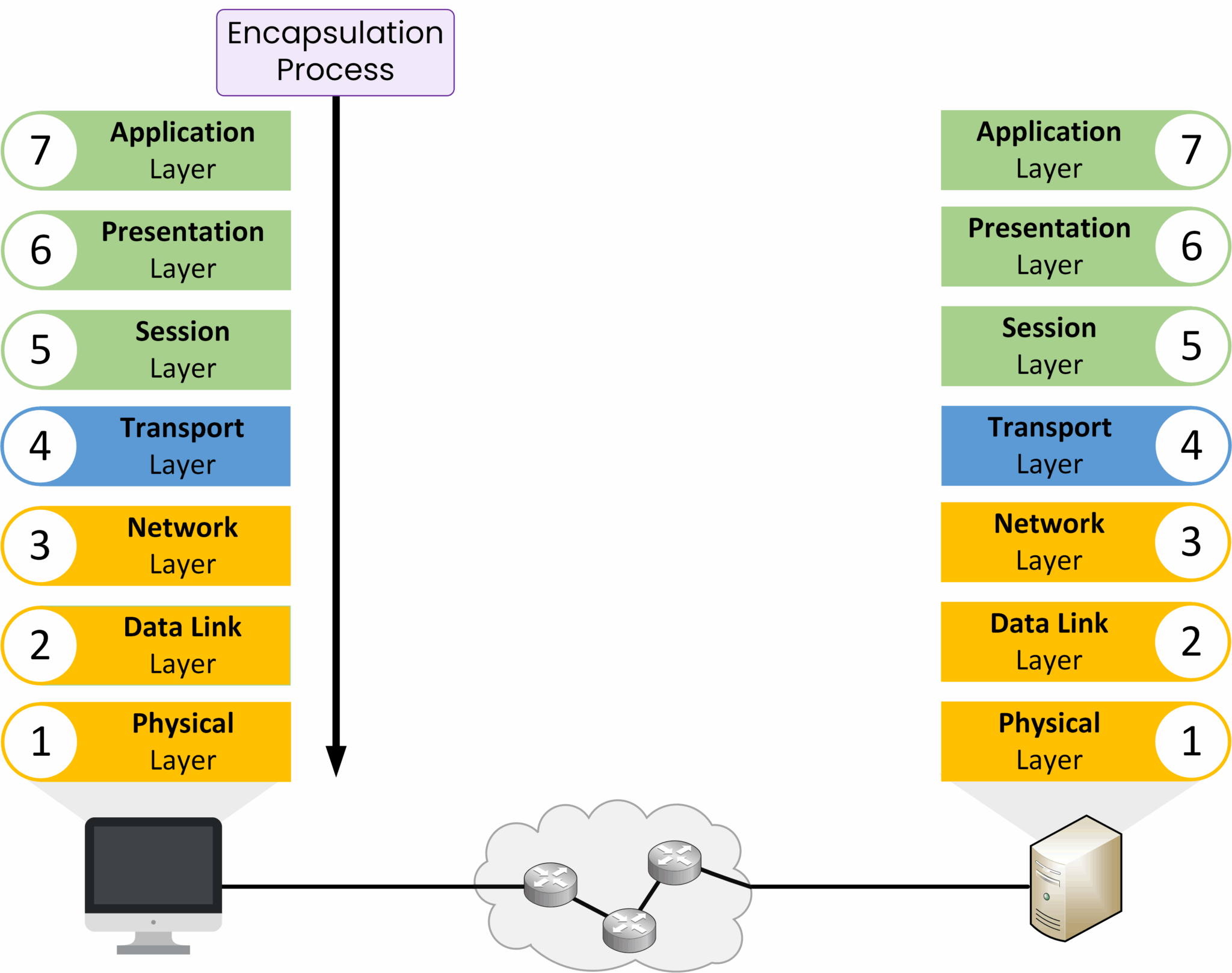
Figure 2 – Encapsulation Process in the OSI Model
At each layer, extra information is added such as addresses, port numbers, and delivery details. This ensures that the data can reach the correct destination.
Decapsulation
When the data arrives at its destination, the process is reversed. The data moves up the OSI layers, and each layer removes and interprets the information that was added by its counterpart on the sender’s side.
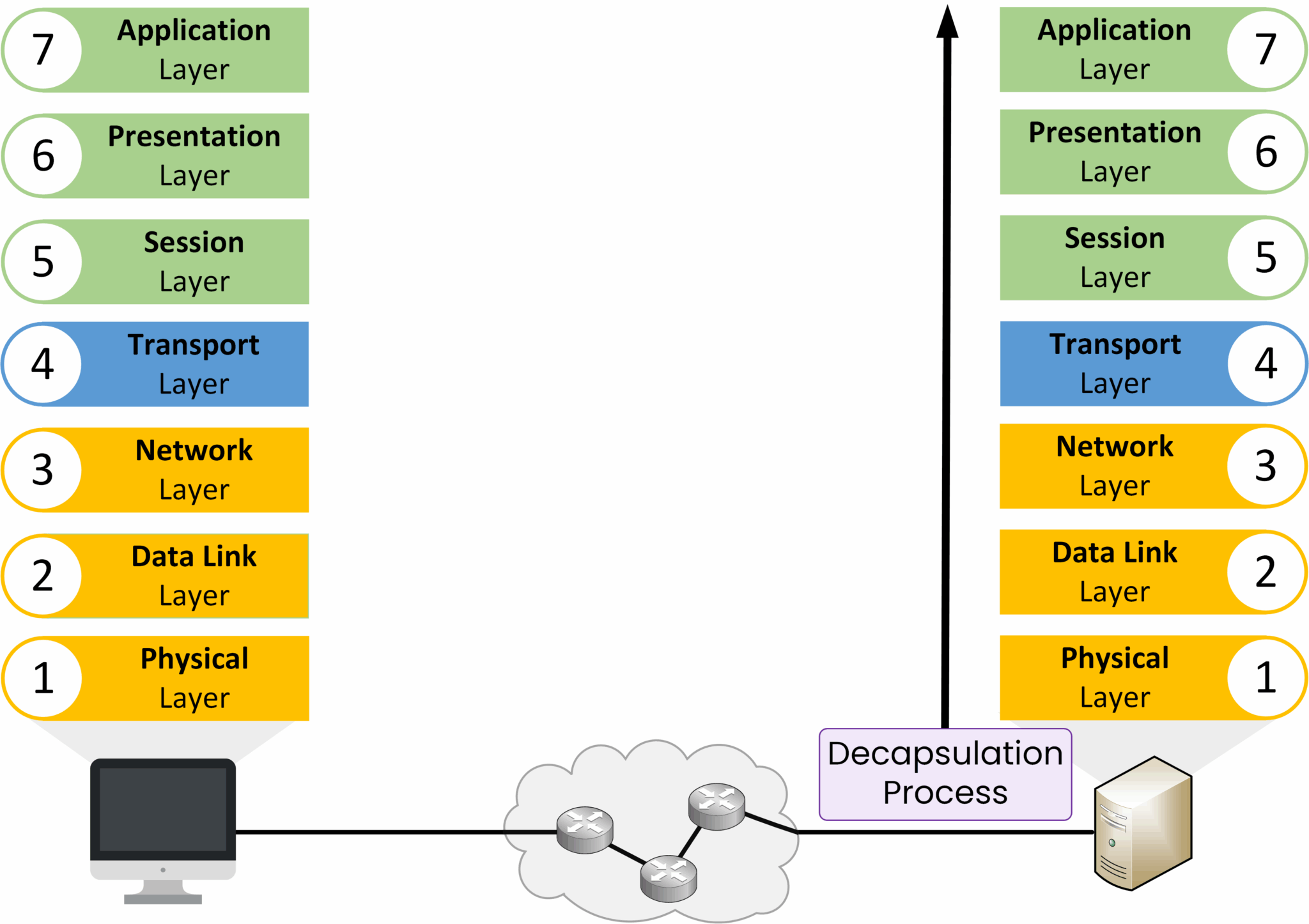
Figure 3 – Decapsulation Process in the OSI Model
Why It Matters
Encapsulation ensures the data contains all the information needed to reach its destination.
Decapsulation ensures the receiving device can interpret the data correctly and deliver it to the right application.
Now that you understand encapsulation and decapsulation, let’s look at the seven OSI layers and the role each one plays in communication.
Answer the question below
What process adds headers and trailers as data moves down the layers?
Seven layers make up the OSI model, and each has a specific function. Let’s look at them from the top (closest to the user) down to the bottom (closest to the physical network).
Layer 7 – Application
The Application Layer is where you interact with the network. You use applications like web browsers, email clients, and messaging apps. When you visit
https://pingmynetwork.com, this layer starts the request with the correct protocol.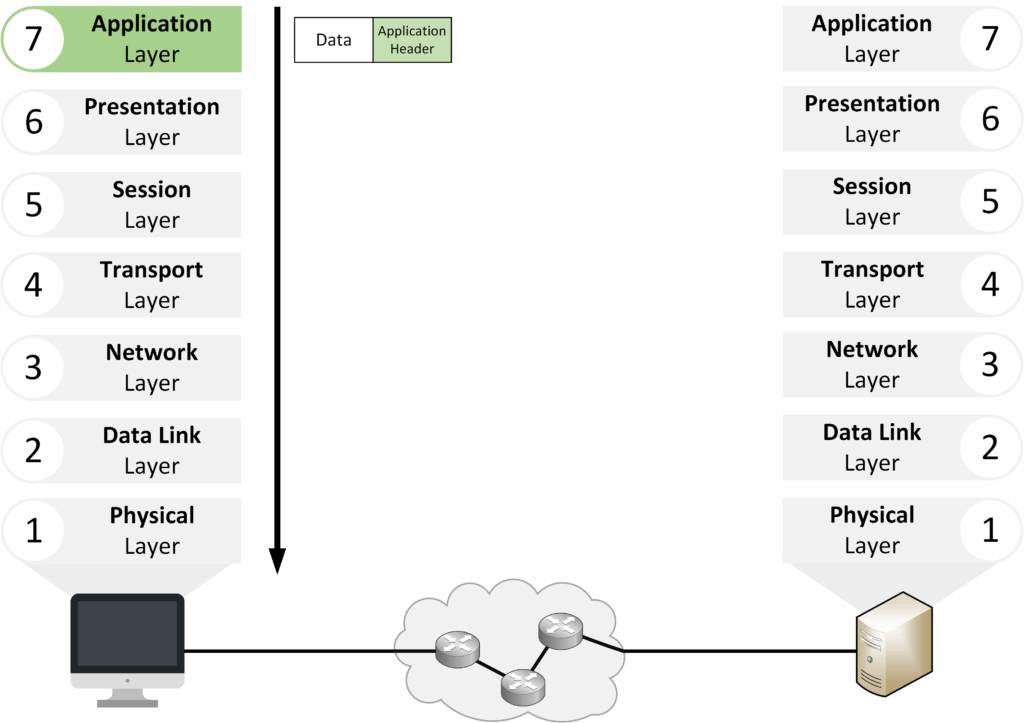
Figure 4 – OSI Layer 7: Application Layer
Key points:
Closest to the end user.
Manages application-level protocols such as HTTPS, HTTP, FTP, and SMTP.
Layer 6 – Presentation
The Presentation Layer formats the data in a way that the receiving application can use. It converts data from the application format to the network format. It can also handle encryption.
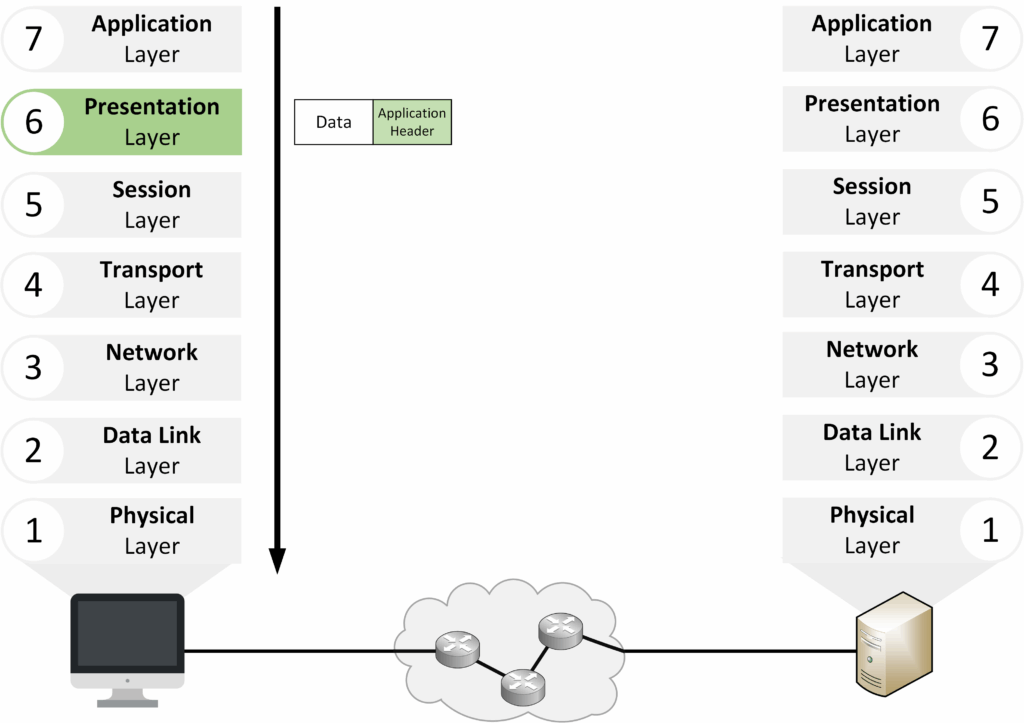
Figure 5 – OSI Layer 6: Presentation Layer
Key points:
Translates and formats data for the application.
Encrypts and decrypts data for secure communication (e.g., TLS/SSL for HTTPS).
Example: Encrypting a message before sending it, then decrypting it upon receipt.
Layer 5 – Session
The Session Layer handles starting, maintaining, and closing communication sessions between devices.
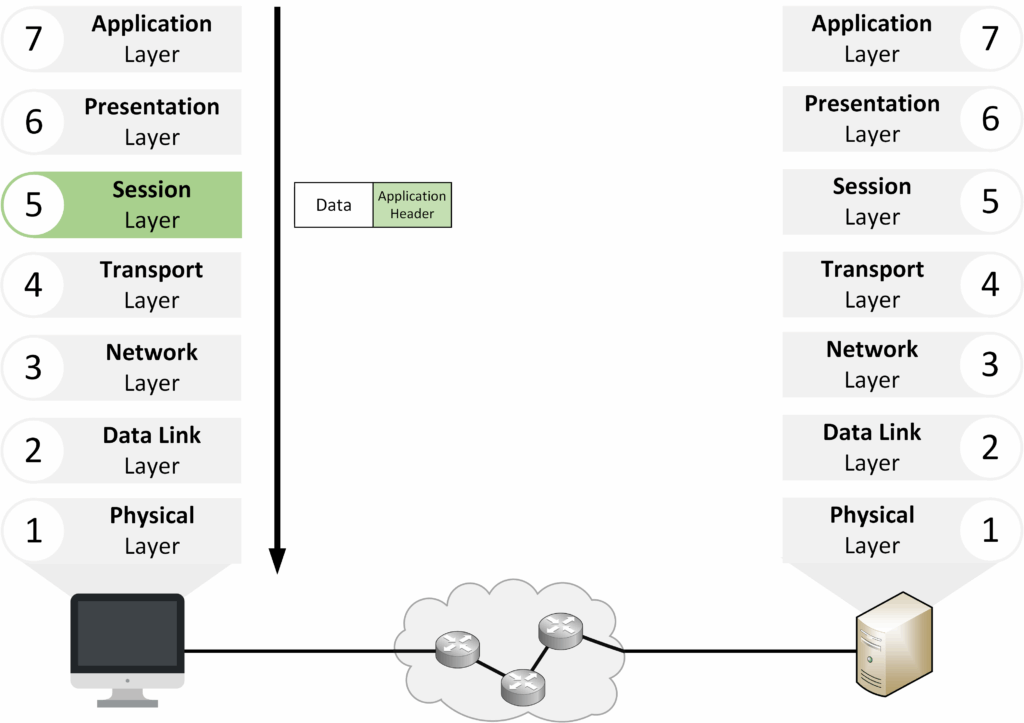
Figure 6 – OSI Layer 5: Session Layer
Key points:
Establishes, maintains, and terminates communication sessions.
Allows many applications to run and communicate at the same time.
Upper Layers Overview
The Upper Layers consist of Layers 7, 6, and 5. They focus on preparing data for transmission.
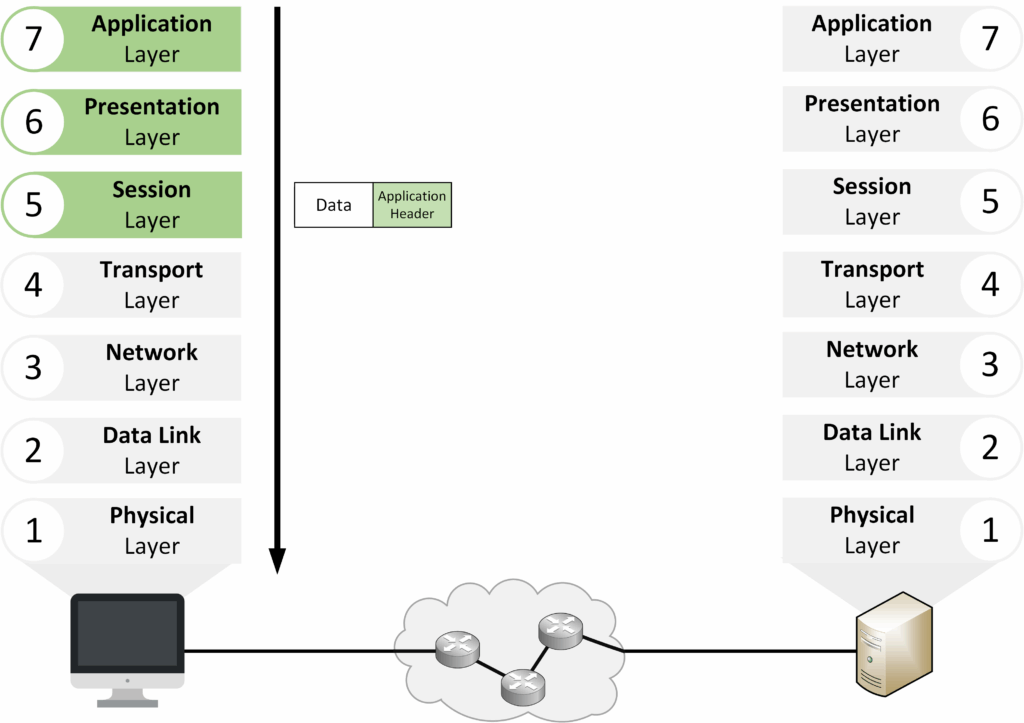
Figure 7 – OSI Upper Layers (Layers 7, 6, 5)
The lower layers (4–1) are responsible for actually delivering the data across the network.
Layer 4 – Transport
The Transport Layer provides end-to-end communication between devices. It splits large streams into smaller segments and uses TCP or UDP to manage delivery.
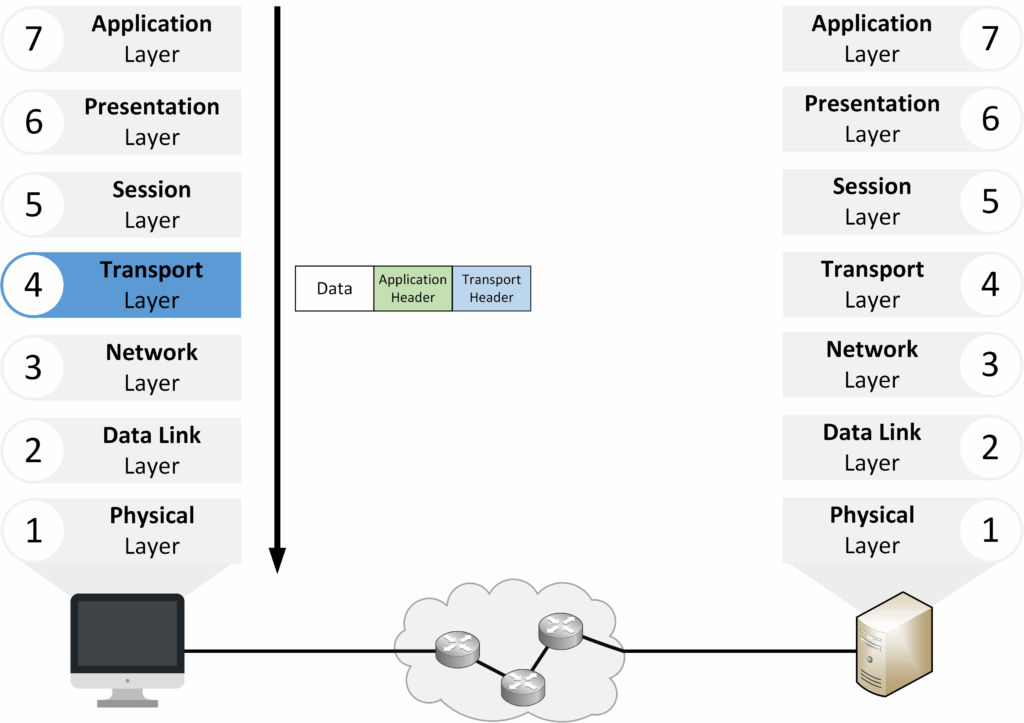
Figure 8 – OSI Layer 4: Transport Layer
Key points:
Segmentation: breaks data into smaller units.
TCP: reliable, ordered delivery.
UDP: faster, connectionless delivery.
Port numbers: identify services (TCP 443 for HTTPS).
Example: When streaming a video, TCP guarantees ordered delivery, while UDP prioritizes speed even if some segments are lost.
Layer 3 – Network
The Network Layer handles logical addressing and routing, ensuring data can move across different networks.
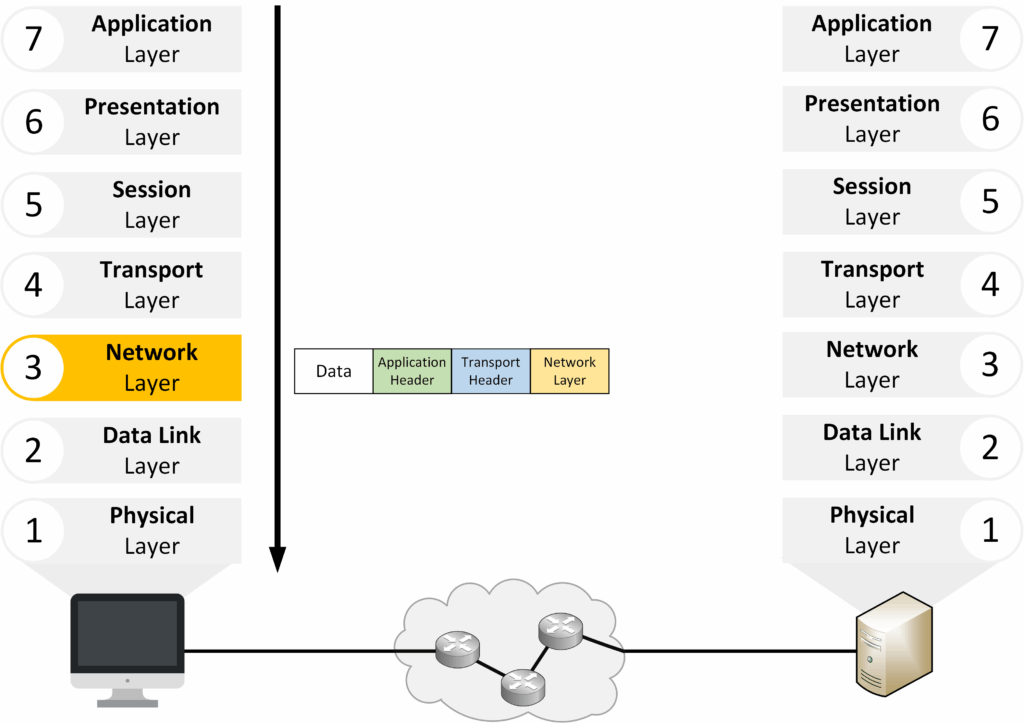
Figure 9 – OSI Layer 3: Network Layer
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
OSI Model
The OSI Model breaks network communication into seven layers, making it easier to understand and troubleshoot. In this lesson, you’ll see how data moves through each layer and why this model still matters today.