Router on a Stick (ROAS) is one of the three methods of Inter-VLAN Routing that we introduced earlier in the InterVLAN Routing course.
To quickly recap, the three approaches are:Legacy Inter-VLAN Routing – using multiple physical router interfaces (rarely used today).
Router-on-a-Stick (ROAS) – using subinterfaces on a single router interface.
Layer 3 Switch (SVIs) – the modern and scalable solution.
In this lesson, we will focus on Router on a Stick, which allows a network administrator to route packets between multiple VLANs using a single router interface divided into subinterfaces.
This is the reference topology we’ll use throughout the course:
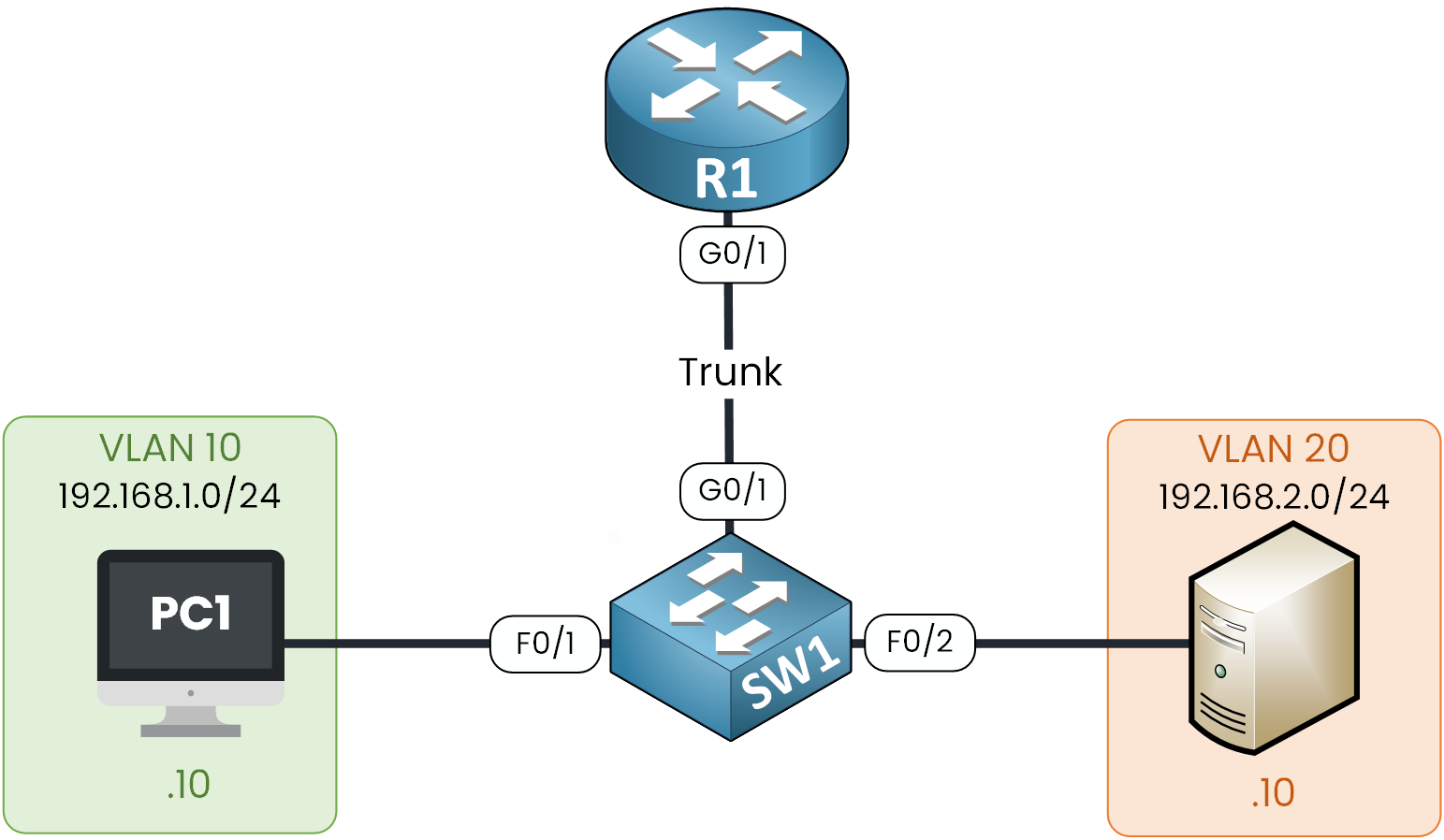
Figure 1 – Router on a Stick Topology
PC1 in VLAN 10 (192.168.1.0/24)
Server in VLAN 20 (192.168.2.0/24)
By configuring Router on a Stick, we enable communication between these two VLANs.
The first concept you need to understand for this method is the subinterface.Answer the question below
A subinterface is a virtual interface created under a single physical router interface.
Each subinterface is associated with a specific VLAN ID using 802.1Q encapsulation.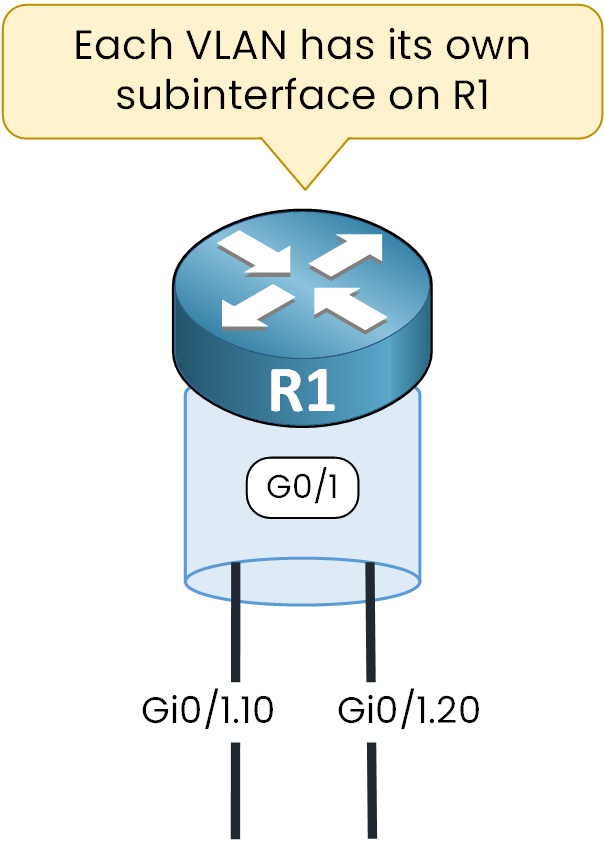
Figure 2 – Subinterfaces on R1
In our example, the physical interface Gi0/1 is divided into two subinterfaces:
Gi0/1.10 → VLAN 10
Gi0/1.20 → VLAN 20
Each VLAN gets its own subinterface, which serves as the default gateway for all devices inside that VLAN.
Because we use one physical interface to support multiple VLANs through subinterfaces, this design is called Router on a Stick (ROAS).
Answer the question below
Which protocol tags VLANs on subinterfaces?
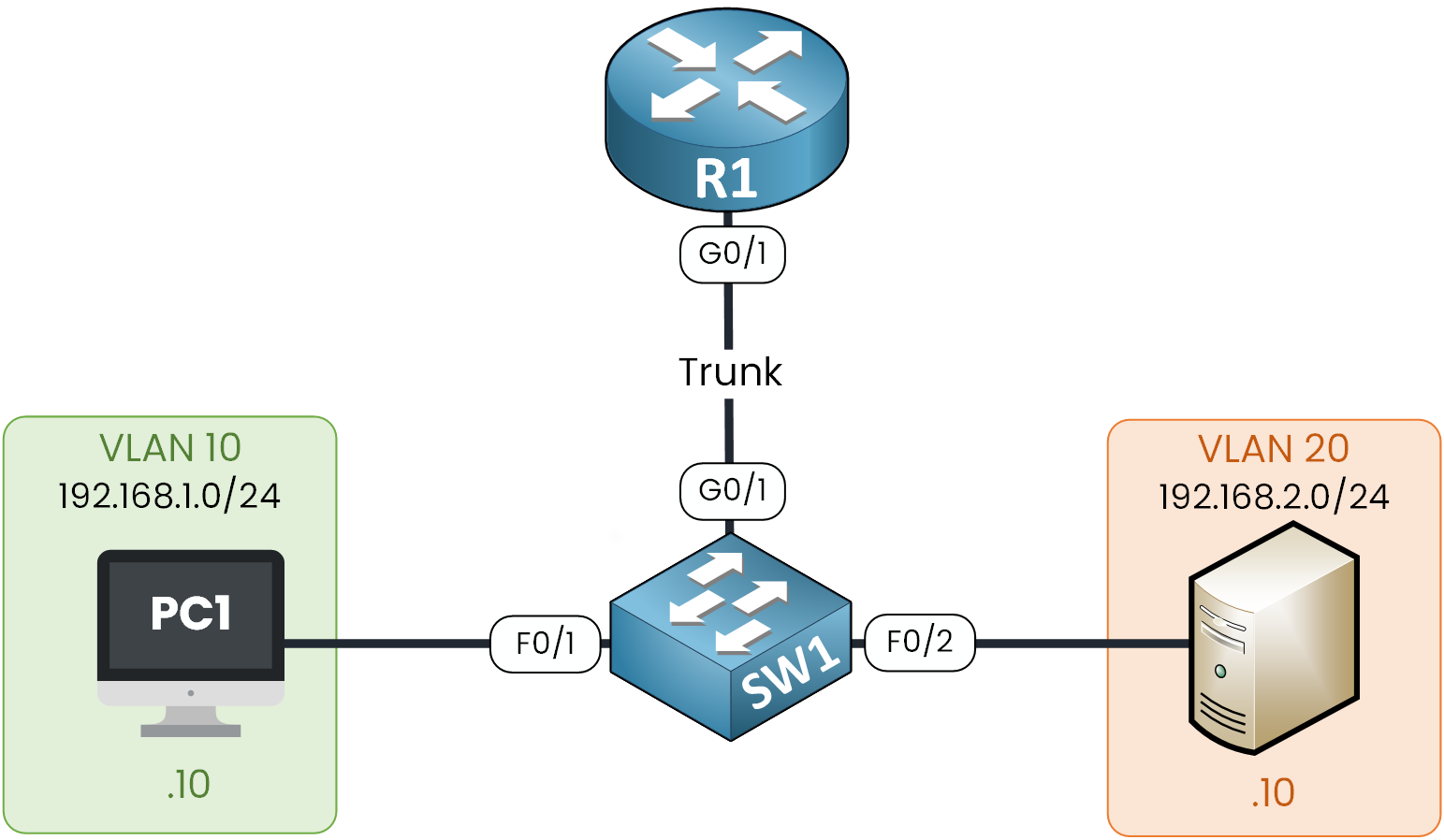
Figure 3 – Router on a Stick Topology
Step 1 — Switch: Define VLANs & Assign Access Ports
First, we need to create the VLANs for the Client (VLAN 10) and the Server (VLAN 20).
SW1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# vlan 10 SW1(config-vlan)# name client SW1(config-vlan)# exit SW1(config)# vlan 20 SW1(config-vlan)# name server SW1(config-vlan)# exitOnce the VLANs are created, we assign the access ports to the right VLANs.
SW1(config)# interface fastEthernet 0/1 SW1(config-if)# switchport mode access SW1(config-if)# switchport access vlan 10 SW1(config-if)# exit SW1(config)# interface fastEthernet 0/2 SW1(config-if)# switchport mode access SW1(config-if)# switchport access vlan 20 SW1(config-if)# exitStep 2 — Switch: Configure the 802.1Q Trunk to the Router
Now, we need to prepare the connection between the switch and the router.
Since the link must carry multiple VLANs, we convert interface Gi0/1 into a trunk port.SW1(config)# interface gigabitEthernet 0/1 SW1(config-if)# no shutdown %LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up SW1(config-if)# switchport mode trunk SW1(config-if)# switchport trunk ? allowed Set allowed VLAN characteristics when interface is in trunking mode native Set trunking native characteristics when interface is in trunking mode SW1(config-if)# switchport trunk allowed vlan 10,20 SW1(config-if)# endHere, we allow only VLAN 10 and VLAN 20 on the trunk to restrict unnecessary traffic.
Note: In real networks, it’s good practice to use a dedicated native VLAN that is not assigned to users. For our lab, leaving the default is fine.
Step 3 — Router: Bring Up the Physical Interface
Next, we move to the router.
We start by enabling the physical interface Gi0/1 , this is the “stick” where we will create subinterfaces.R1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# interface gigabitEthernet 0/1 R1(config-if)# no shutdown %LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up R1(config-if)# endLet’s quickly verify that the interface is up:
R1# show ip int brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 unassigned YES unset administratively down down GigabitEthernet0/1 unassigned YES unset up up GigabitEthernet0/2 unassigned YES unset administratively down downStep 4 — Router: Create Subinterfaces (One per VLAN)
Now that our physical interface is ready, we can create one subinterface for each VLAN.
This step is quite straightforward, so let’s walk through it together.40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Router On a Stick
Router on a Stick is a classic method of inter-VLAN routing that uses subinterfaces on a single router interface to connect multiple VLANs. In this lesson, you will configure ROAS step by step and understand its benefits and limitations.