A trunk link is a Layer 2 connection that carries traffic from multiple VLANs between switches.
Without trunking, each VLAN would be confined to the switch in which it was created.Why Trunking Is Needed
To understand why trunking is important, let’s look at a simple example.
Below, two VLANs are created on two switches.
PC1 and PC3 belong to VLAN 10, but they are connected to different switches.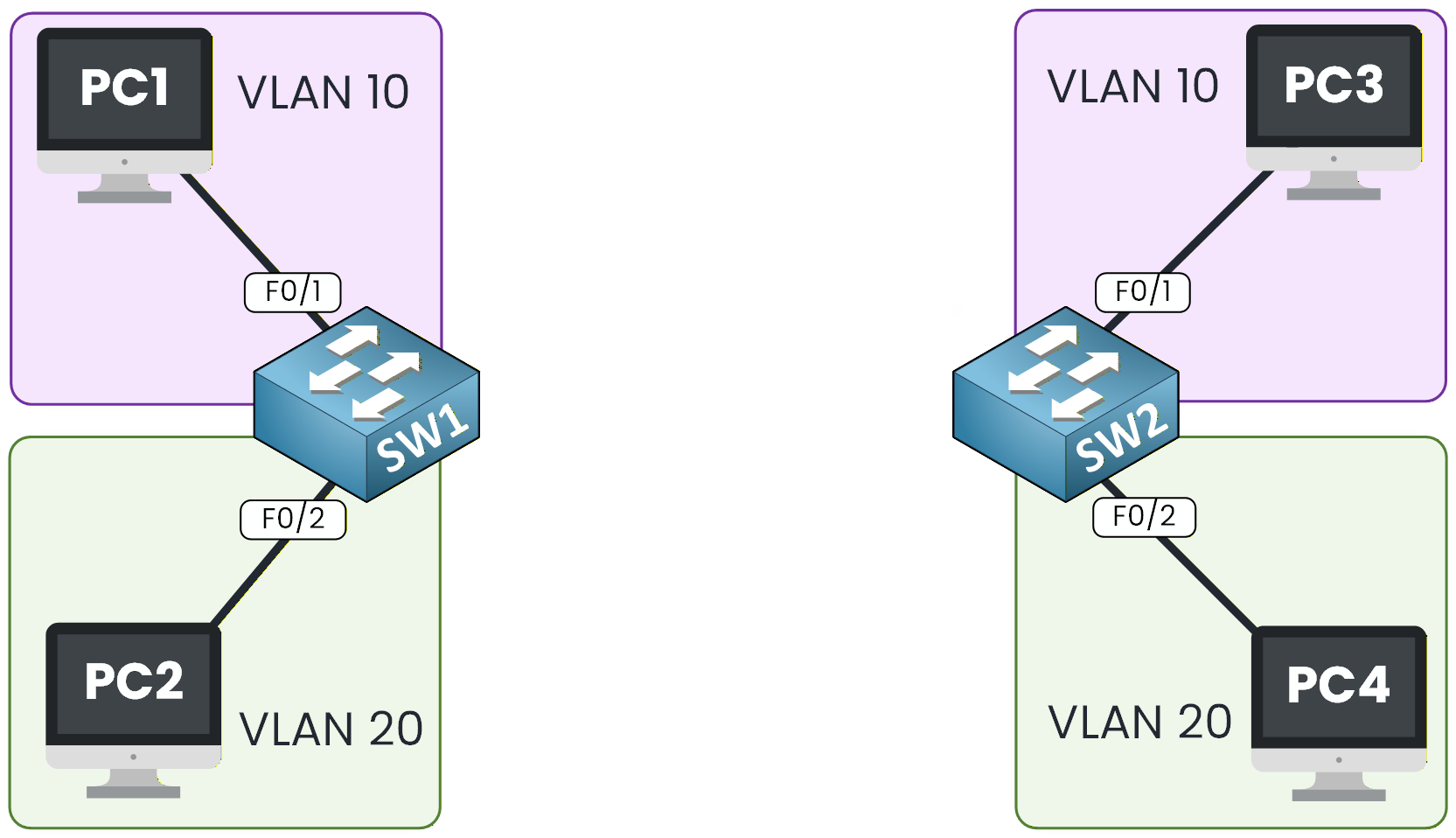
Figure 1 – VLANs on Different Switches
Even though both devices belong to VLAN 10, they still cannot communicate because they are located on separate switches.
To allow communication between these two devices, we need two things:
A physical link connects the switches.
802.1Q trunking is enabled on that link.

Figure 2 – Trunk Link Between Switches
Enabling trunking allows VLAN 10 and VLAN 20 traffic to pass through the inter-switch link.
This means that each VLAN can now extend beyond a single switch. For example, VLAN 10 on SW1 can reach VLAN 10 on SW2.How the Trunk Link Connects VLANs
Let’s walk through an example to see this in action.
PC1 send traffic to PC3.
SW1 receives the frame on interface F0/1, which is an access port in VLAN 10.
Since PC3 is connected to another switch, SW1 forwards the frame to SW2 over the trunk link.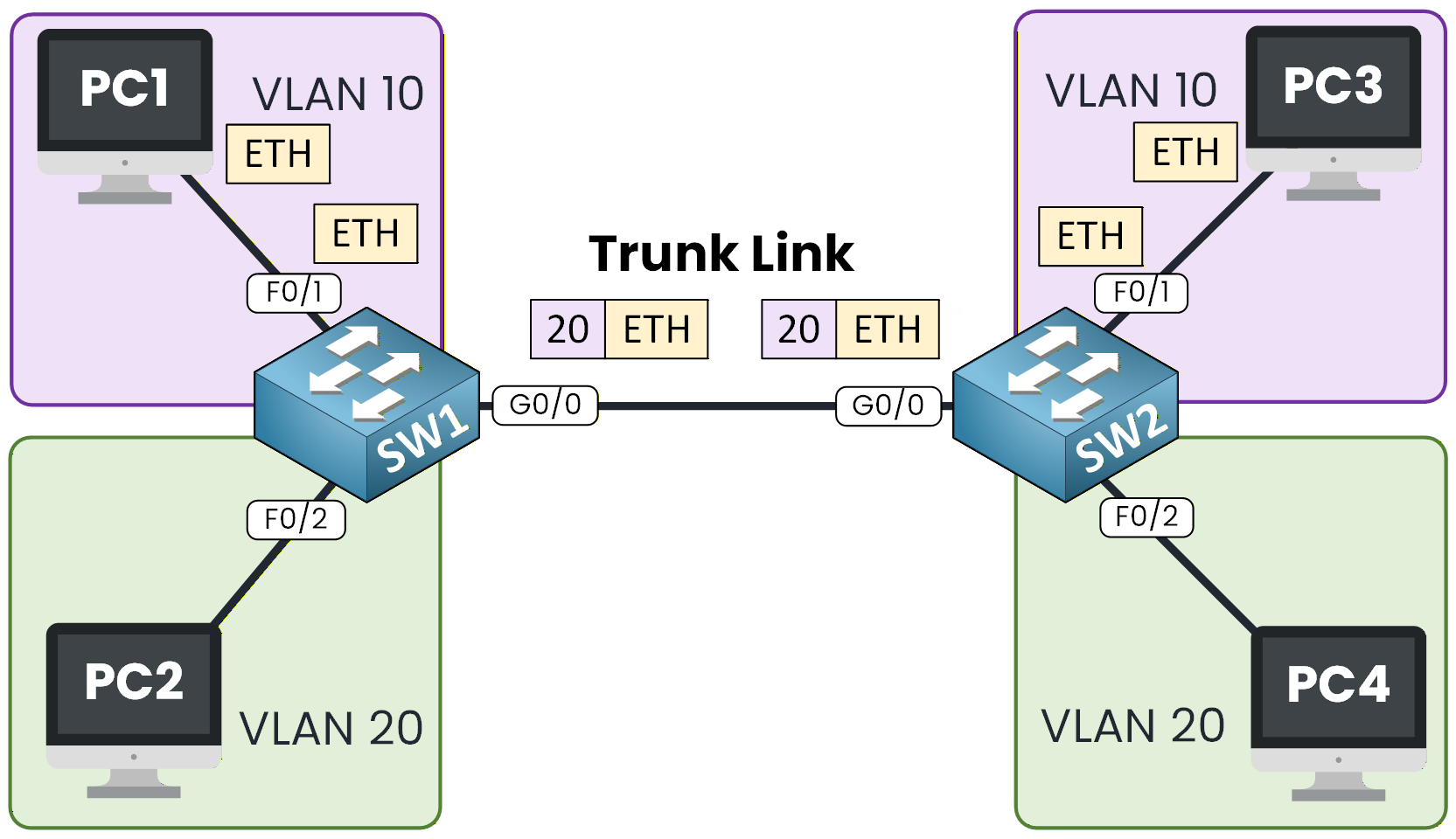
Figure 3 – VLAN Tagging with 802.1Q Trunking
SW2 receives the frame, identifies it as part of VLAN 10, and forwards it to PC3.
From the user’s perspective, both PCs appear to be on the same local network, even though they are on different switches.The purpose of trunking is to extend VLANs across multiple switches while keeping the traffic of each VLAN logically separate.
Now that we understand what trunking involves, the next step is to examine how VLAN information is added to, transported through and removed from frames as they cross the trunk.Answer the question below
What type of link carries multiple VLANs between SW1 and SW2?
In this example, I have kept VLAN 10 and our switch.
As you can see, PC1 wants to send data to PC3. To do this, PC1 sends the traffic via SW1.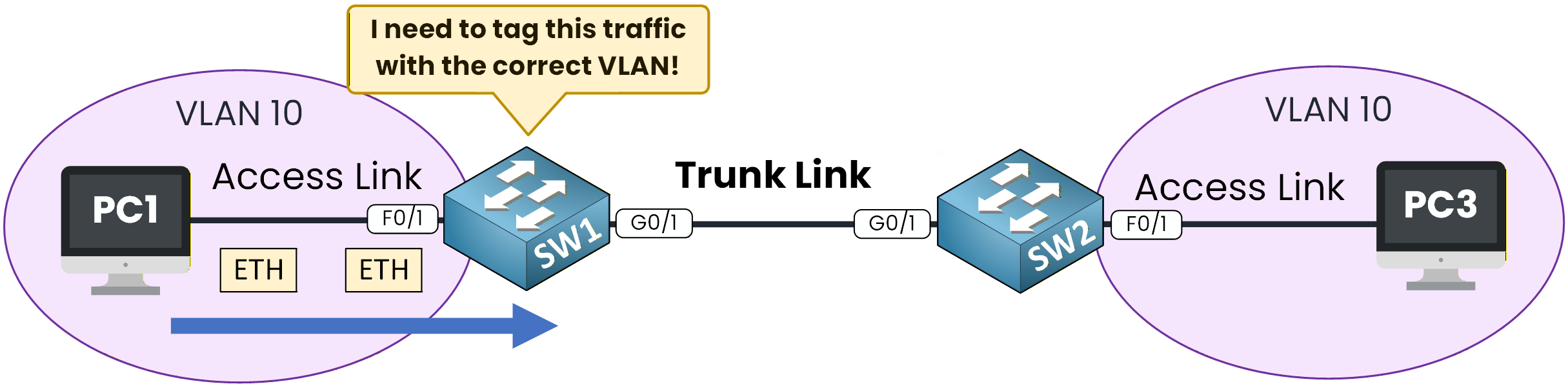
Figure 4 – VLAN Tagging Process on a Trunk Link
Let's take a look step by step.
Step 1 – Frame Ingress on SW1
PC1 belongs to VLAN 10. When PC1 sends a frame, it arrives at SW1’s F0/1 access port, which is also assigned to VLAN 10.
Once inside the switch, the frame is associated with VLAN 10. The Ethernet frame does not yet have a VLAN tag.Step 2 – Tagging for the Trunk
As the destination (PC3) is on a different switch, SW1 must send the frame via the trunk link to SW2.
Before doing so, SW1 adds an 802.1Q header to the frame, a 4-byte field inserted just after the source MAC address.
This header identifies the VLAN to which the frame belongs. This enable multiple VLANs to safely share a single physical link.
Figure 5 – 802.1Q Frame Structure with VLAN Tag
The IEEE 802.1Q protocol defines this tagging method. It’s a vendor-neutral standard that replaced Cisco’s older ISL protocol.
The 802.1Q header includes:
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
802.1Q Trunking
A trunk link is a connection that carries traffic from multiple VLANs between switches. In this lesson, you’ll learn how 802.1Q tagging makes this possible.