In Quality of Service (QoS), two common techniques are used to control how much bandwidth traffic flows can consume: Shaping and Policing.
Both rely on a Committed Information Rate (CIR), which defines the maximum bandwidth that can be transmitted over an interface.
The difference lies in how each technique handles traffic that exceeds this CIR.Answer the question below
Shaping is a rate-limiting technique that buffers excess traffic instead of discarding it.
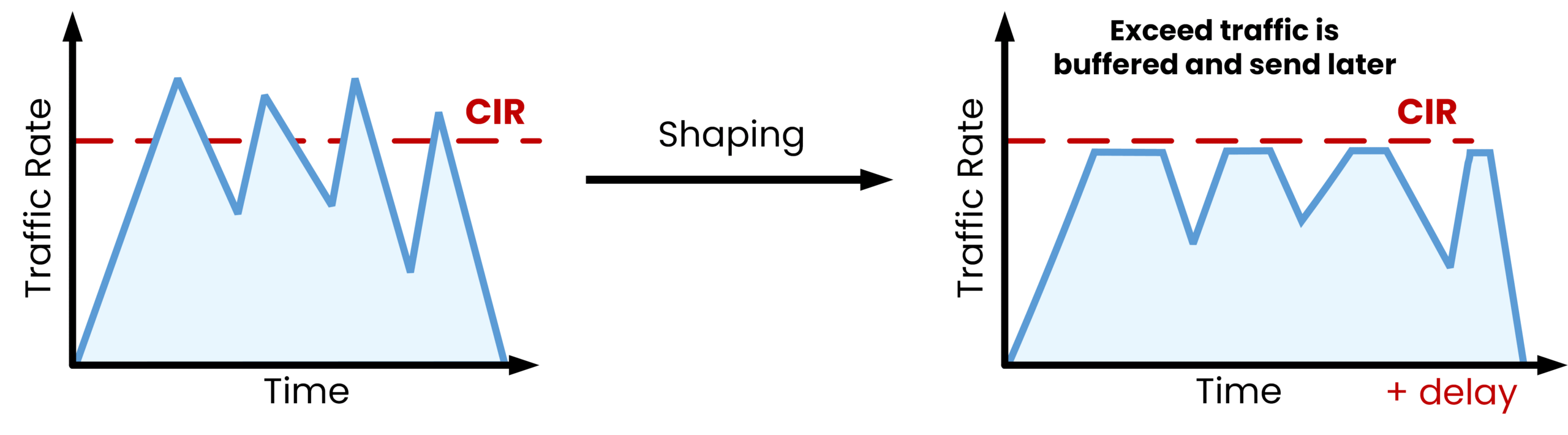
Figure 1 – Shaping in Quality of Service
In the figure, traffic that goes above the red CIR line is not dropped. Instead, it is placed in a shaping buffer and sent later at a controlled rate.
This configured rate limit is often defined by a service agreement.
For example, if an Internet Service Provider (ISP) sets a maximum of 400 Mbps, then 400 Mbps becomes the CIR.By queuing traffic bursts and transmitting them gradually, shaping prevents packet loss, ensures compliance with the agreed bandwidth, and smooths out irregular traffic patterns.
Answer the question below
What does shaping do with excess traffic?
Policing also enforces the CIR but works in a different way.
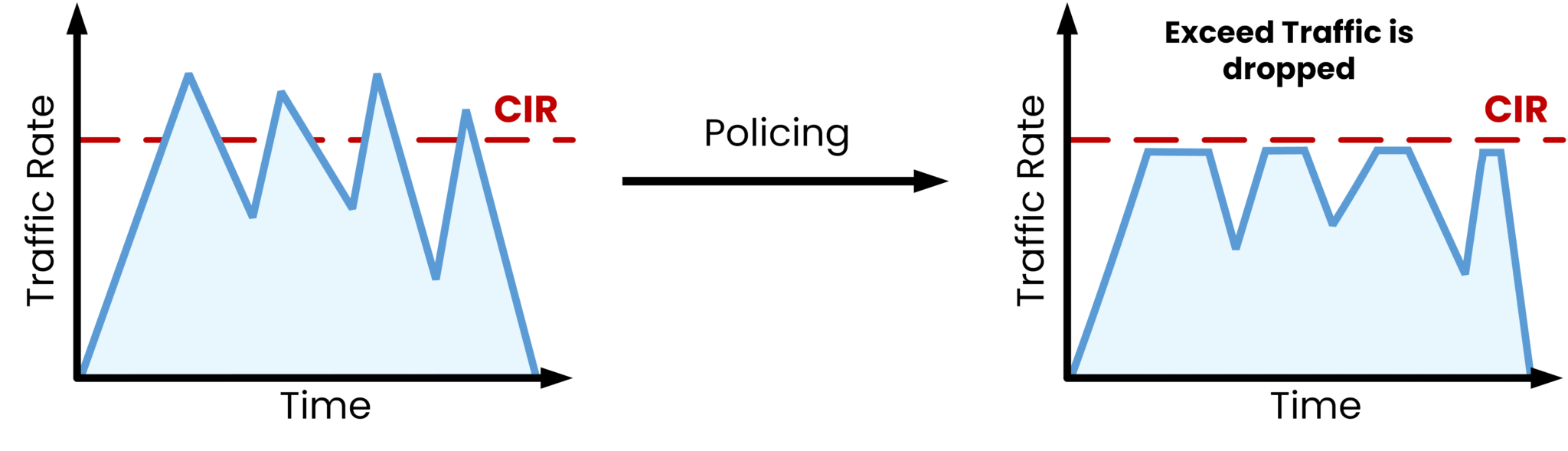
Figure 2 - Policing in Quality of Service
When traffic exceeds the red CIR line, policing does not buffer it. Instead, it immediately applies one of two actions:
Dropping packets: Excess traffic is discarded.
Re-marking packets: Excess traffic is marked with a lower priority so that it may still be delivered, but as less important traffic.
Unlike shaping, policing does not provide flexibility for bursts. It is a stricter approach, commonly used in service provider environments to ensure traffic strictly conforms to contractual limits.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Shaping and Policing
Shaping and Policing are two QoS techniques that control bandwidth usage based on a committed information rate. This lesson shows how each method behaves in real networks and why their differences matter for performance and design.