Imagine you’ve just joined a mid-sized company as the new network administrator.
Your first task involves VLAN configuration to place the Sales and Tech teams into separate broadcast domains.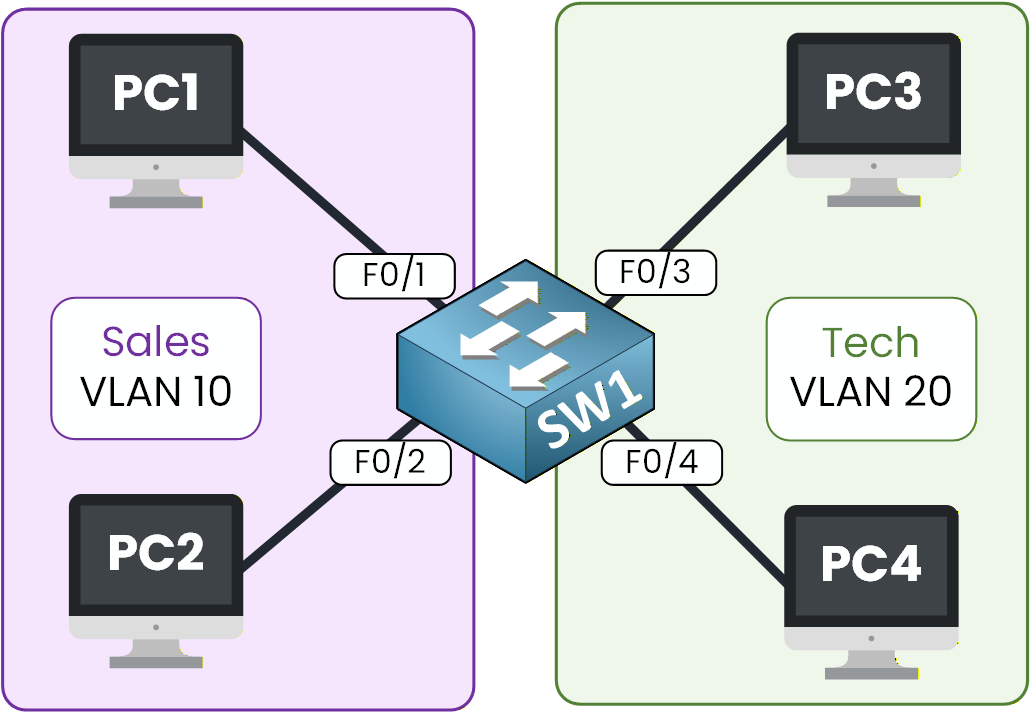
Figure 1 – Topology used to configure VLANs
Your goal in this lab is to fix that by creating:
VLAN 10 for Sales
VLAN 20 for Tech
Let’s get started!
How to Begin
Download the lab file at the top of the page and open it in Packet Tracer.
The topology is ready and waiting for you; we will only focus on the VLAN configuration.Lab Overview
Here’s the structure we’ll follow throughout this lab:
Step 1 – Create the VLANs
Step 2 – Place Devices in Their VLANs
Step 3 – Test Your VLAN Segmentation
Step 4 – Maintain and Reset VLANs
Let’s Get Started
Open the Packet Tracer file and follow each step with me.
You don’t need to know the commands yet, we’ll learn them together, and you’ll apply them directly in Packet Tracer as we progress.Let’s go!
Answer the question below
Let’s now move from theory to practice.
In this first step, your goal is to create the two VLANs we will use throughout the lab:VLAN 10 for the Sales team
VLAN 20 for the Tech team
Each VLAN will act as a separate broadcast domain.
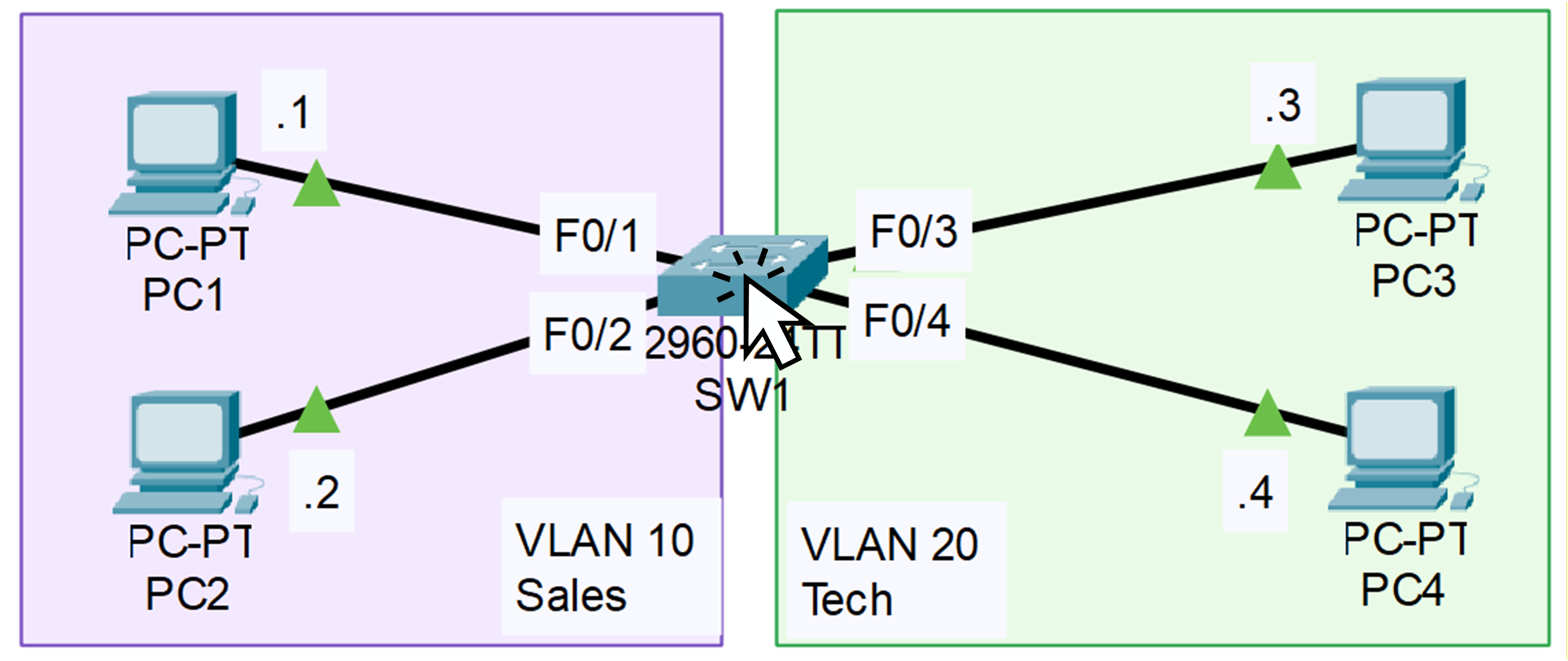
Figure 2 – VLAN Topology on Packet Tracer
Before we start creating anything, click on SW1 in Packet Tracer so we can look at its current VLAN configuration.
Check Existing VLANs
To see all VLANs configured on the switch, enter the following command:
SW1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeAs you can see, the switch currently has VLAN 1, which is the default VLAN, and all interfaces are assigned to it.
You can also see VLANs 1002 to 1005. These VLANs are created automatically on Cisco switches and correspond to very old technologies.
We don’t need them for this lab, so you can safely ignore them.Right now, everything is in VLAN 1, meaning Sales and Tech traffic is mixed together.
Let’s change that by creating the two VLANs we need.Entering Configuration Mode
To create the VLANs, we first need to enter global configuration mode.
This mode allows you to modify the switch’s behavior, including VLANs, interfaces, and many other features.SW1# configure terminalThis command moves you out of
user EXEC modeand into the configuration environment, where you can start applying changes to the switch.Create VLAN 10 (Sales)
Let’s begin by creating the first VLAN for the Sales team.
SW1(config)# vlan 10 SW1(config-vlan)# name ? WORD The ascii name for the VLAN SW1(config-vlan)# name Sales SW1(config-vlan)# exitYou’ve now added VLAN 10 to the switch’s VLAN database.
At this moment, it exists on the switch, but no interfaces are assigned to it yet, so it doesn’t impact traffic.Create VLAN 20 (Tech)
Now repeat the same process for the Tech department:
SW1(config)# vlan 20 SW1(config-vlan)# name Tech SW1(config-vlan)# exitJust like VLAN 10, VLAN 20 is now created inside the switch’s VLAN database.
However, since no ports belong to it yet, nothing has changed on the network.Verifying VLAN Creation
Before we continue, let’s make sure both VLANs were successfully created.
Use the command below to display all VLANs on the switch:SW1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 10 Sales active 20 Tech active 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeUnderstanding the Output
You can now see that VLAN 10 and VLAN 20 both exist on the switch.
However, all switchports are still assigned to VLAN 1, which is the default VLAN for every interface.This means that, for the moment, traffic from Sales and Tech is still mixed together.
There is no separation between the two groups yet, and that’s expected, VLANs only become effective once you assign interfaces to them.Quick Recap
So far, you’ve learned how to:
Enter configuration mode on a Cisco switch
Create VLANs and name them properly
Verify their presence using
show vlan brief
In the next section, we’ll assign specific switch ports to each VLAN so that the Sales and Tech devices become properly separated into their own broadcast domains.
Answer the question below
How many VLANs did you create?
Now that your VLANs exist in the switch’s VLAN database, it’s time to assign the correct interfaces to each VLAN.
This is the moment where the logical separation becomes real: by mapping physical ports to specific VLANs, you ensure that the Sales and Tech teams no longer share the same broadcast domain.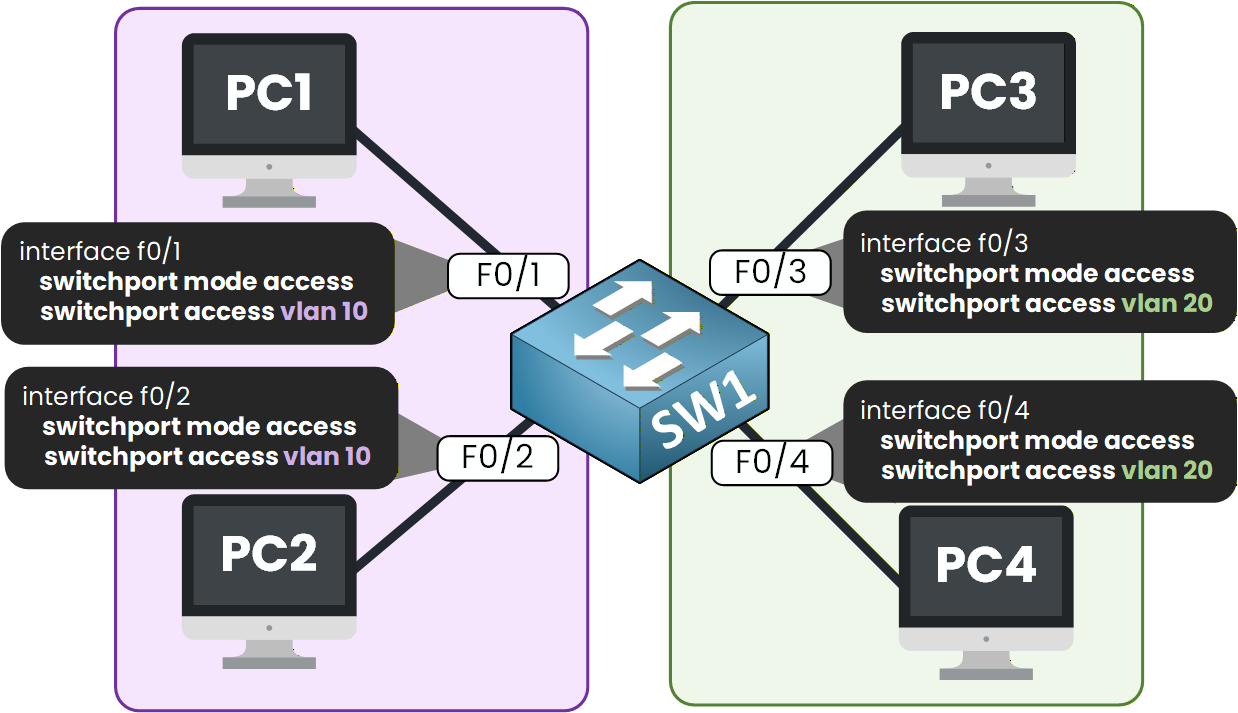
Figure 3 – Access Port Configuration per VLAN
To do this, you’ll use two key commands:
switchport mode accessswitchport access vlan X
Let’s apply them step by step.
Assigning Sales Ports (VLAN 10)
The Sales team devices are connected to interfaces
Fa0/1andFa0/2.
Let’s start with the first port:SW1(config)# interface f0/1 SW1(config-if)# switchport mode access SW1(config-if)# switchport access vlan ? <1-4094> VLAN ID of the VLAN when this port is in access mode SW1(config-if)# switchport access vlan 10 SW1(config-if)# exitThese commands do two things:
switchport mode accessforces the interface into access mode, meaning it will belong to a single VLAN.switchport access vlan 10assigns the port to VLAN 10 (Sales).
Now apply the same configuration to the second Sales interface:
SW1(config)# interface f0/2 SW1(config-if-range)# switchport mode access SW1(config-if-range)# switchport access vlan 10Both Sales devices are now placed inside VLAN 10.
Assigning Tech Ports (VLAN 20)
Let’s now assign the Tech team’s interfaces,
Fa0/3andFa0/4, to VLAN 20.SW1(config)# interface f0/3 SW1(config-if-range)# switchport mode access SW1(config-if-range)# switchport access vlan 20 SW1(config-if-range)# exit SW1(config)# interface f0/4 SW1(config-if-range)# switchport mode access SW1(config-if-range)# switchport access vlan 20The process is exactly the same as before, except the VLAN ID changes to 20.
At this point, both groups are now completely isolated at Layer 2, but we’ll validate this in the next step.Verifying Port Assignments
To make sure every interface has been assigned to the correct VLAN, use:
SW1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 10 Sales active Fa0/1, Fa0/2 20 Tech active Fa0/3, Fa0/4 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeYou can clearly see that each interface now belongs to the correct VLAN.
What to Remember Here
You’ve now connected theory to practice.
VLANs are logical by nature, but they only become effective when you assign real interfaces to them.At this point, the Sales and Tech teams are fully isolated at Layer 2, even though they share the same physical switch.
Answer the question below
Which VLAN is Fa0/1 in?
Now that your VLAN configuration is in place, let’s verify that everything works as expected.
We’ll start by checking communication inside the same VLAN, and then we’ll test communication between different VLANs to confirm that isolation is working.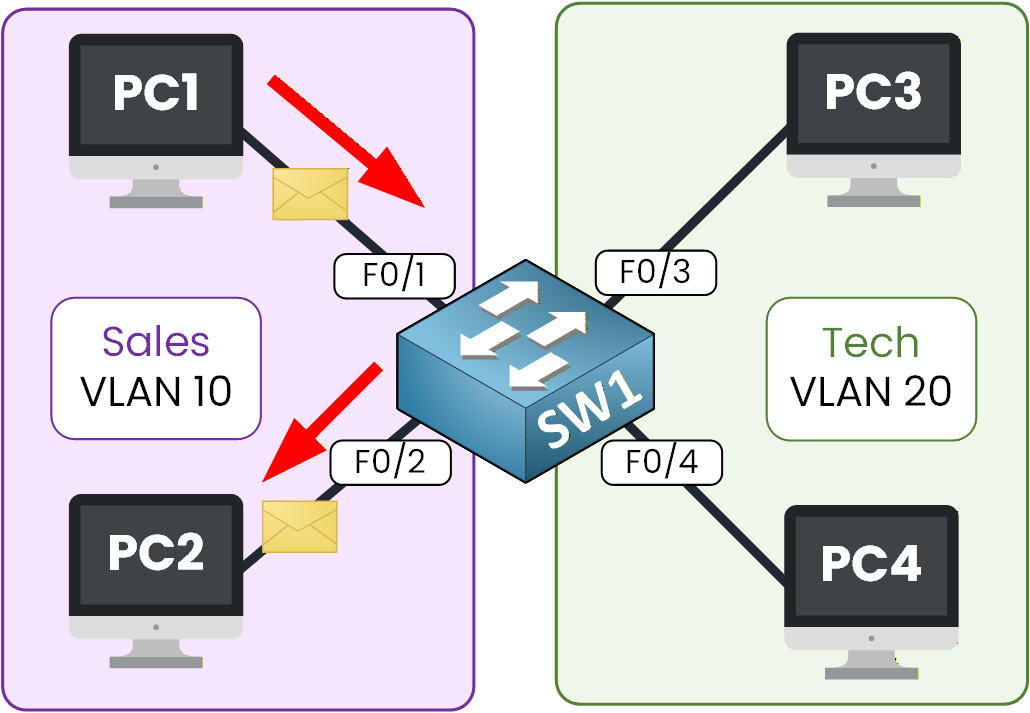
Figure 4 – Communication Inside the Same VLAN
Testing Communication Inside VLAN 10
Let’s begin by checking whether PC1 can communicate with PC2.
Both devices are in VLAN 10, so they should be able to reach each other without any issue.On PC1, open the Command Prompt.
You can find it under the Desktop tab.
Figure 5 – Enter the PC1 command prompt
Here, we will type the
pingcommand.
This command allows us to check whether we can communicate with PC2.
We simply ping the IP address of PC2.In our case, PC2 has the IP address 192.168.1.2.
C:\> ping 192.168.1.2 Pinging 192.168.1.2 with 32 bytes of data: Reply from 192.168.1.2: bytes=32 time=5ms TTL=128 Reply from 192.168.1.2: bytes=32 time=10ms TTL=128 Reply from 192.168.1.2: bytes=32 time=9ms TTL=128 Reply from 192.168.1.2: bytes=32 time<1ms TTL=128 Ping statistics for 192.168.1.2: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 10ms, Average = 6msGreat!
As you can see, we get replies back from PC2.
The communication is occurring normally between PC1 and PC2.Communication from VLAN 10 to VLAN 20
Now let’s try a ping from PC1 (VLAN 10) to PC3 (VLAN 20).
Once again, we use the ping command, this time with PC3’s IP address.C:\> ping 192.168.1.3 Pinging 192.168.1.3 with 32 bytes of data: Request timed out. Request timed out. Request timed out. Request timed out. Ping statistics for 192.168.1.3: Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),As expected, the ping fails.
The switch does not allow a frame coming from VLAN 10 to be forwarded into another VLAN.
The two VLANs are completely isolated.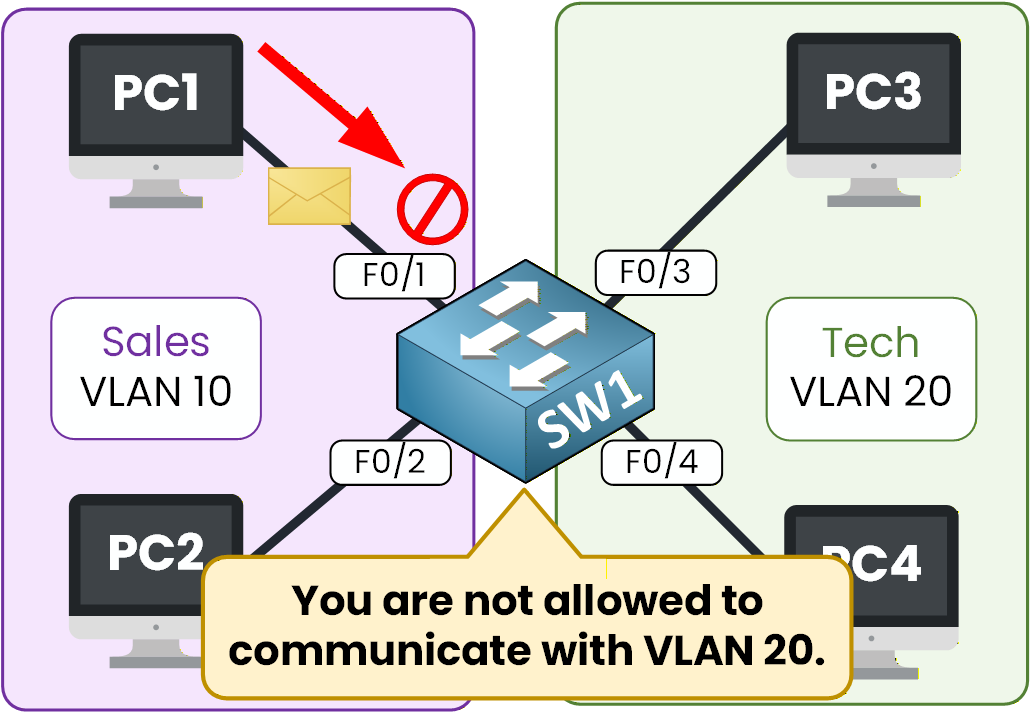
Figure 6 – Communication Blocked Between VLANs
Answer the question below
Which IP address does PC1 fail to ping?
Now that your VLANs are configured and all ports are assigned, let’s take a moment to look at how VLAN information is actually stored and managed on a Cisco switch.
This part is important, because VLAN data does not behave like most other configuration settings. It isn’t saved inside the running configuration or startup configuration.Where VLANs Are Stored?
When you create VLANs on a Cisco switch, they are not saved in the running or startup configuration.
Instead, they are stored in a separate file called vlan.dat, located in the switch’s flash memory.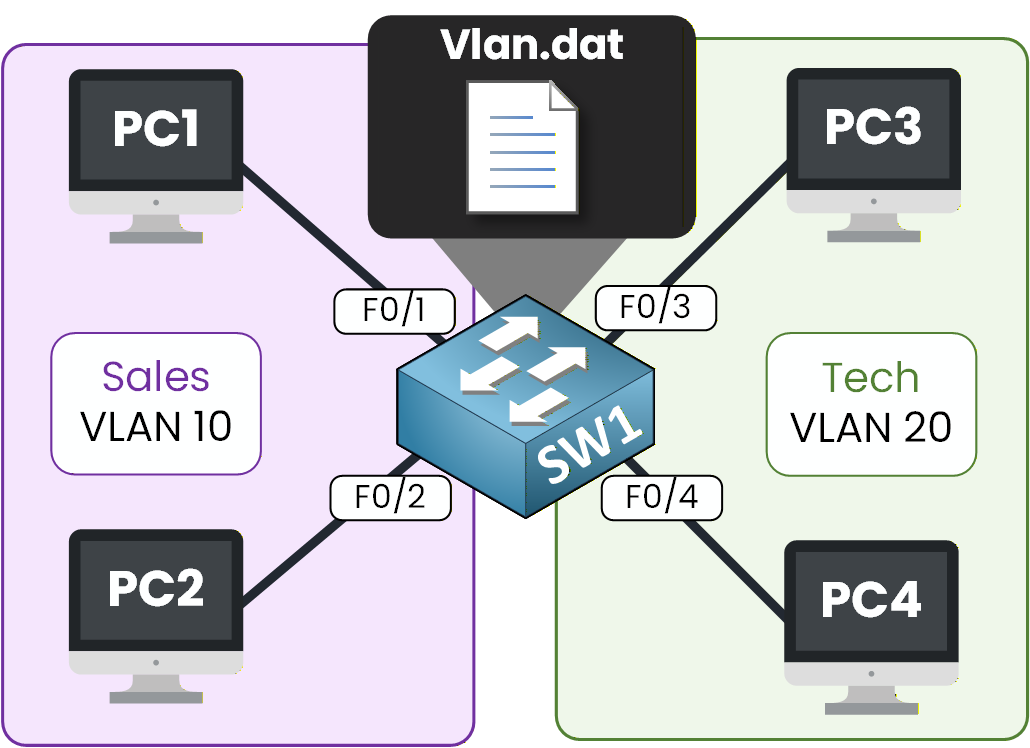
Figure 7 – Vlan.dat file in Cisco switch
This design ensures that VLAN information survives reboots and loads quickly when the switch starts.
Renaming a VLAN
You can rename a VLAN at any time without affecting its configuration or the ports assigned to it.
Let’s rename VLAN 10 from Sales to Sales_Department.SW1# conf t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# vlan 10 SW1(config-vlan)# name Sales_DepartmentTo confirm the change, use:
SW1#show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 10 Sales_Department active Fa0/1, Fa0/2 20 Tech active Fa0/3, Fa0/4 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeThe VLAN name has changed, and all associated ports remain the same.
Deleting a VLAN
Let’s now see what happens when you delete a VLAN.
Before removing VLAN 20, here is the current VLAN table:SW1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 10 Sales active Fa0/1, Fa0/2 20 Tech active Fa0/3, Fa0/4 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeNow delete VLAN 20:
SW1# conf t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# no vlan 20Check the VLAN table again:
SW1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12 Fa0/13, Fa0/14, Fa0/15, Fa0/16 Fa0/17, Fa0/18, Fa0/19, Fa0/20 Fa0/21, Fa0/22, Fa0/23, Fa0/24 Gig0/1, Gig0/2 10 Sales active Fa0/1, Fa0/2 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default activeImportant: After deleting VLAN 20, you may notice that the ports that previously belonged to it no longer appear under any VLAN. This is normal behavior.
When a VLAN is removed, its ports do not automatically return to VLAN 1. Instead, they become “orphaned” ports with a VLAN that no longer exists, and they must be manually assigned to a valid VLAN if you want to use them again.
Answer the question below
Where are VLANs stored?
Congratulations, you have completed the VLAN Configuration Lab!
This lab is an important step in your CCNA learning journey because VLANs are the foundation of modern LAN design.
By creating and assigning VLANs, you learned how to segment a network logically, reduce unnecessary broadcasts and improve overall security inside a switched environment.Before moving on, here are the commands I want you to remember from this lab.
Creating a VLAN
Use these commands to enter configuration mode and create a VLAN with a name.
SW1# configure terminal SW1(config)# vlan 10 SW1(config-vlan)# name SalesAssigning an Interface to a VLAN
Use these commands to put a port in access mode and assign it to a VLAN.
SW1(config)# interface f0/1 SW1(config-if)# switchport mode access SW1(config-if)# switchport access vlan 10Verifying VLANs
Use this command to display all VLANs and their associated ports.
SW1# show vlan briefYou are now ready for the next lesson on 802.1Q Trunking, where you will learn how multiple VLANs can travel across a single link between switches.
Let’s continue!
Answer the question below
Which command shows all VLANs on the switch?