Before AAA protocols, giving access to network devices was done manually. Each device, like routers and switches, needed to be set up one by one with its own username and password.
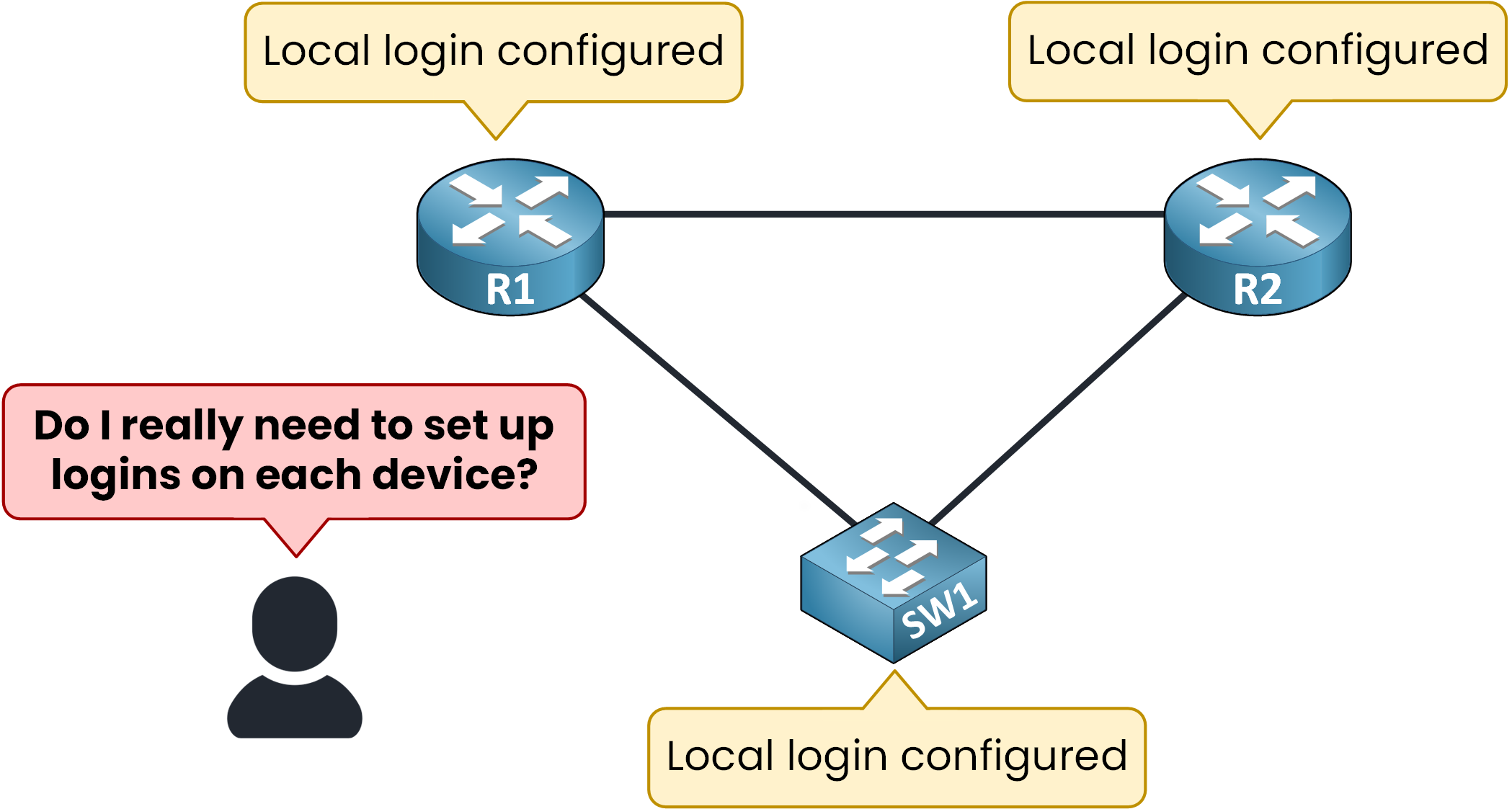
Figure 1 – Without AAA: Separate Logins on Each Device
This approach had several drawbacks:
Not Centralized: Since every device stored its own credentials, there was no unified way to manage or control access.
Security Risks: Local credentials were vulnerable to theft or unauthorized access, especially since each device held its own separate user information.
Lack of Visibility: Tracking who accessed which device and what they did was nearly impossible.
As networks grew larger, these challenges became more obvious. Businesses needed a centralized system to simplify and secure access to their equipment.
That’s when AAA (Authentication, Authorization, and Accounting) was introduced, providing a reliable and efficient way to control access across all devices.
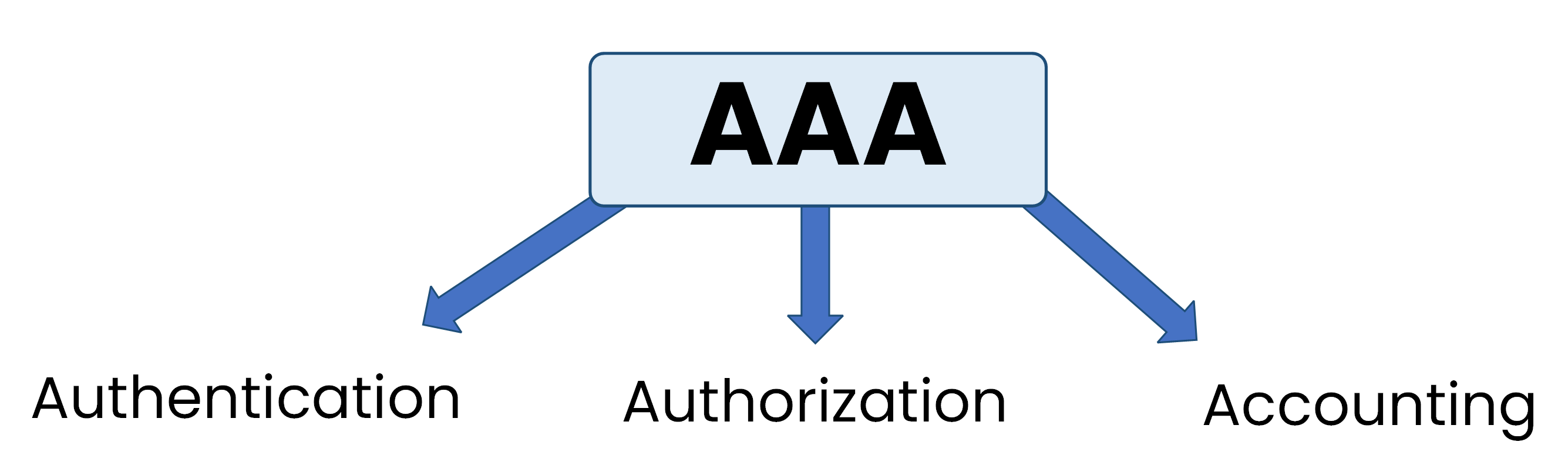
Figure 2 – AAA Centralizes Access Control
Answer the question below
What system was introduced to centralize and secure device access?
Imagine a network where every device like routers, switches has its own local credentials. Users log in separately to each device.
This method comes with major downsides:
It’s inefficient: Managing every device individually becomes a nightmare as the network grows.
It’s insecure: With no centralized control, vulnerabilities multiply.
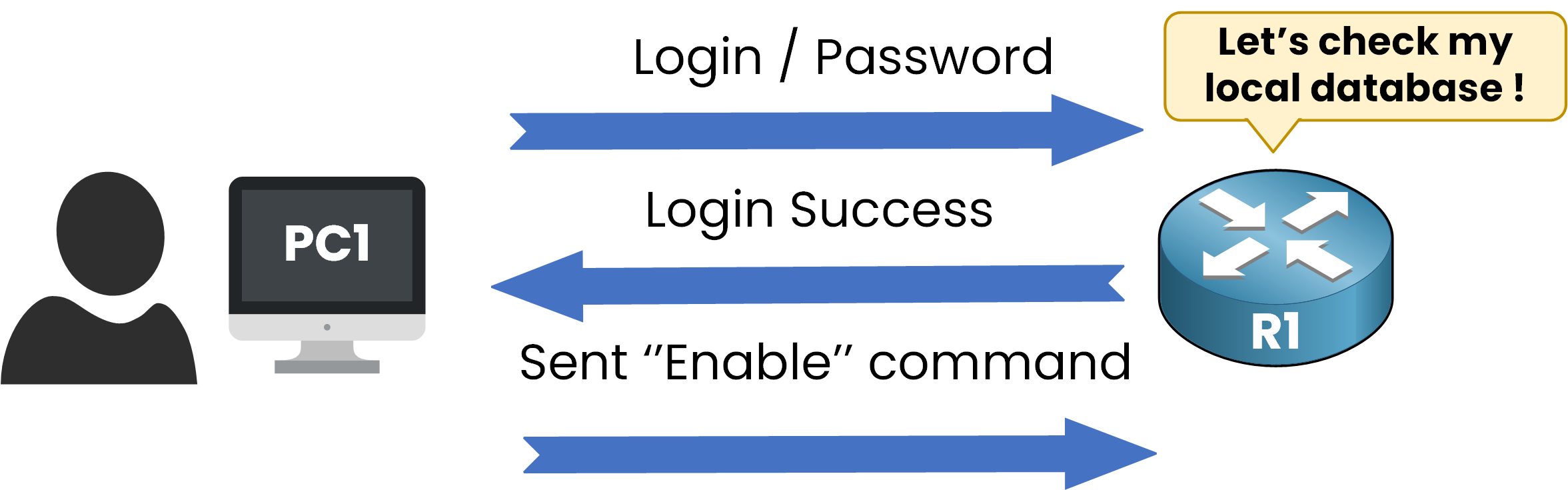
Figure 3 – Local Authentication Without AAA
That’s why AAA is a game-changer. It centralizes user management, enforces command controls, and tracks all activities, making your network more secure and manageable.
Answer the question below
Without AAA, how are users authenticated on each network device?
AAA is essential for modern networks because it solves key problems by offering:
Scalability: You can manage access for hundreds or even thousands of devices from one central point.
Centralized Control: Administrators can set, monitor, and update access policies easily.
Enhanced Security: Only authorized users get access, and their actions are restricted based on their role.
Activity Logs: Every action is tracked, providing a clear audit trail for troubleshooting and monitoring.
Example:
Think about a company with hundreds of devices across multiple locations. Without AAA, setting up access on each device separately is slow, inconsistent, and risky. With AAA, you can control everything centrally, who gets in, what they can do, and track every action.Answer the question below
According to this chapter, what benefit ensures that only authorized users get access?
Authentication is the first step in AAA. It’s all about verifying the user’s identity before allowing access to the network.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally