Port security violation mode defines how a Cisco switch reacts when an unauthorized device sends traffic through a secured port.
Cisco offers three Port Security violation modes to control this behavior:
Shutdown (default)
Restrict
Protect
Figure 1 – Overview of Cisco Port Security violation modes
Each mode offers a different level of enforcement and logging. Let’s explore them one by one.
Answer the question below
What is the default Port Security violation mode on a Cisco switch?
The Shutdown mode is the most aggressive and secure option.
Behavior
The switch disables the port (err-disabled state).
A syslog and/or SNMP alert is generated when the violation occurs.
All traffic stops on the interface, including from authorized devices.
The violation counter increases once (at the moment of shutdown).
Once the port is shut down, no additional logs are generated, even if the unauthorized device keeps sending traffic.
This mode ensures maximum security but requires manual intervention or automatic recovery to bring the port back up.
Answer the question below
What happens to the port in Shutdown mode?
The Restrict mode is more flexible than Shutdown mode.
Behavior
Unauthorized traffic is dropped.
A syslog and/or SNMP message is generated every time a violation occurs.
The port remains operational for authorized devices.
The violation counter increases for each unauthorized frame.
This mode is useful in production environments where network availability is a priority but violation monitoring is still required.
Example Configuration for Restrict Mode
Let’s take a hands-on look at how Restrict Mode operates in practice!
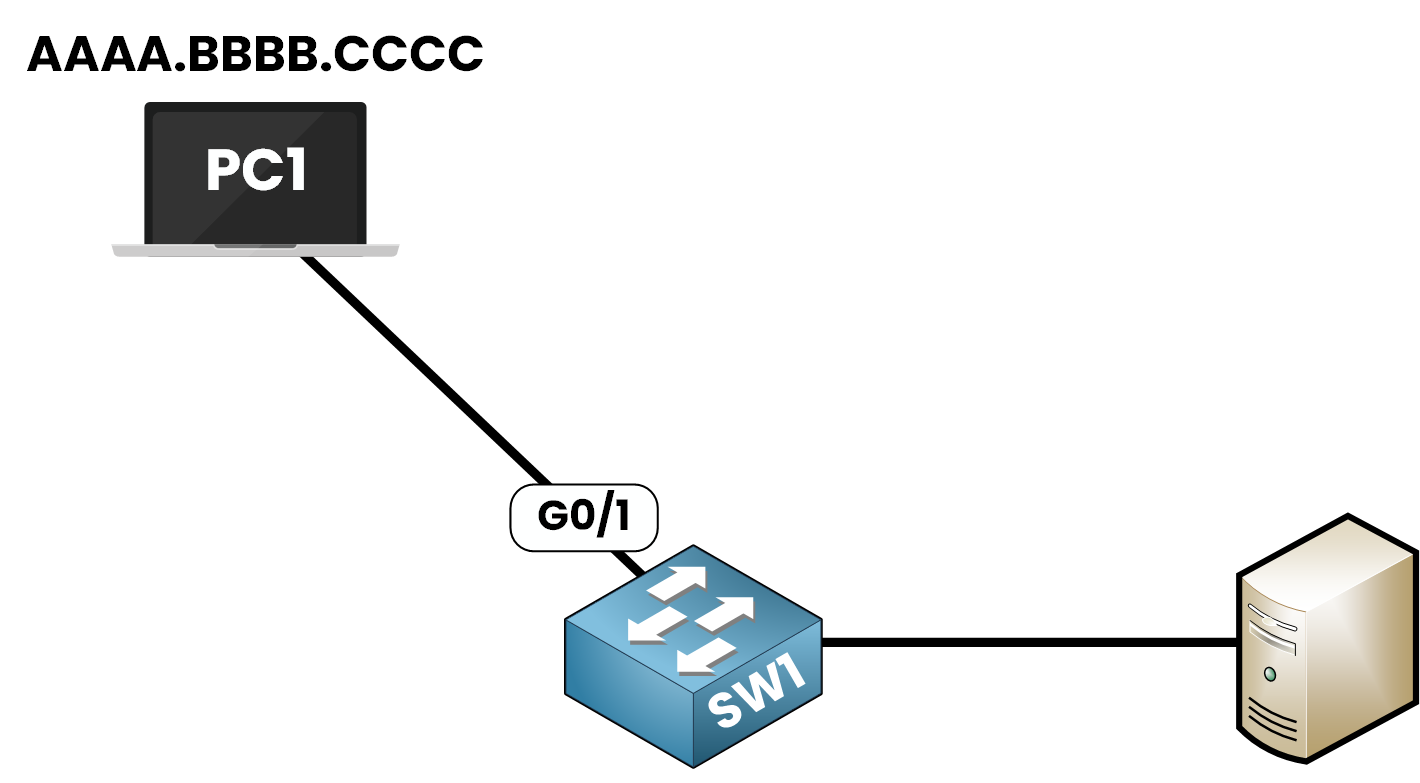
Figure 2 – Topology used to demonstrate Port Security Restrict mode in practice
Step 1 – Enable Port Security:
First, enable Port Security on interface G0/1:
SW1(config)# int g0/1 SW1(config-if)# switchport port-securityStep 2 – Configure a secure MAC address (PC1):
This time, I will statically authorize PC1’s MAC address. Let’s explore the available port security options:
SW1(config)# int g0/1 SW1(config-if)# switchport port-security ? aging Port-security aging commands mac-address Secure mac address maximum Max secure addresses violation Security violation modeNow, we configure PC1’s MAC address (AAAA.BBBB.CCCC) as the secure MAC address:
SW1(config-if)# switchport port-security mac-address AAAA.BBBB.CCCCStep 3 – Set violation mode to restrict:
Next, let’s configure the violation mode to Restrict:
SW1(config-if)# switchport port-security ? aging Port-security aging commands mac-address Secure mac address maximum Max secure addresses violation Security violation modeThe available violation modes are shown below:
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Port Security Violation Mode
Port security violation modes control how Cisco switches respond to unauthorized traffic on secured ports. This lesson explains the behavior of shutdown, restrict, and protect modes so you can apply the right balance between security and availability.