By default, all switch interfaces on a Cisco device are enabled.
This means any physically connected device can instantly gain network access.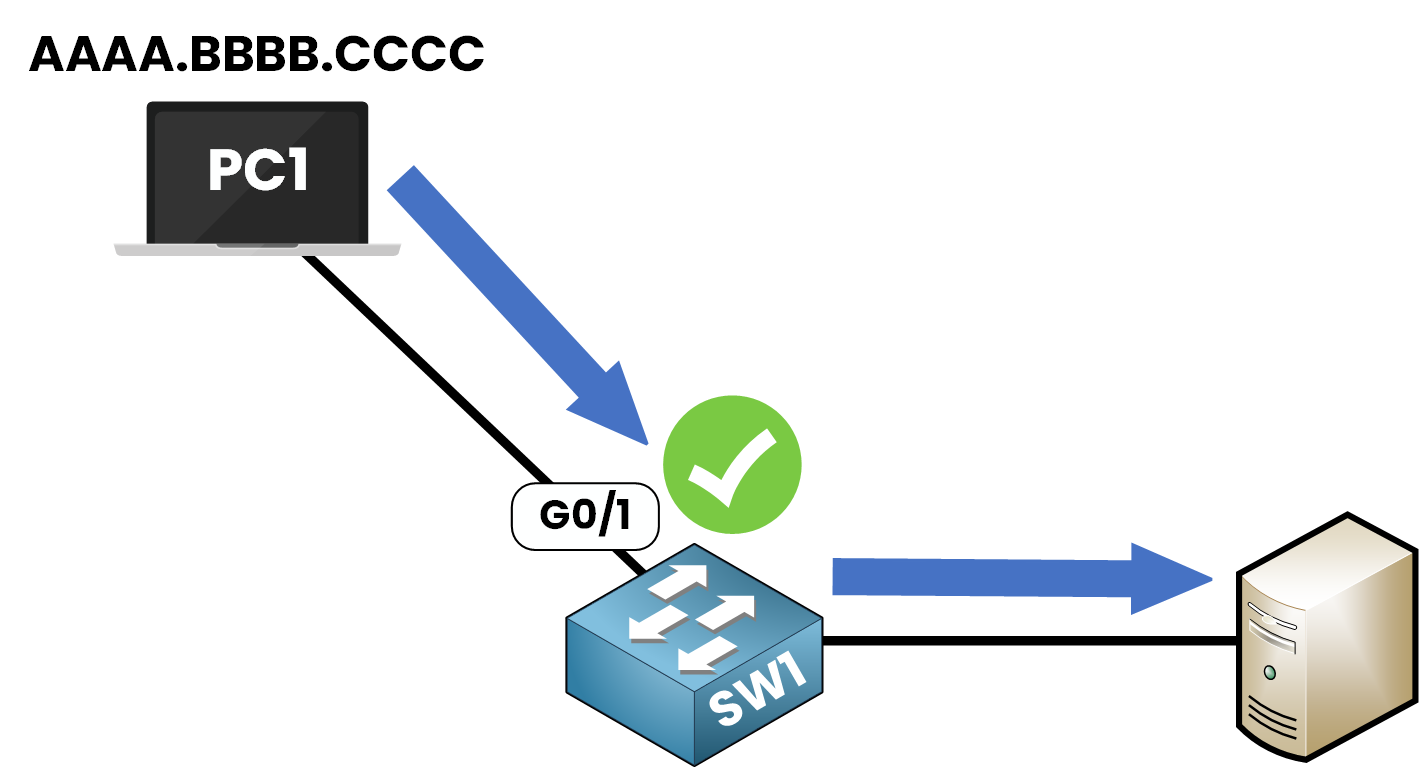
Figure 1 – Default Behavior of a Cisco Switch Port
This behavior may seem convenient, but it exposes the network to risk.
In shared offices, public spaces, or uncontrolled environments, anyone could plug in a rogue device and gain access.
Without restrictions, the switch would accept the connection, allowing unauthorized traffic or even malicious activity.
To prevent this, we use Port Security.
This feature allows you to control which MAC addresses are allowed to send traffic on each port.
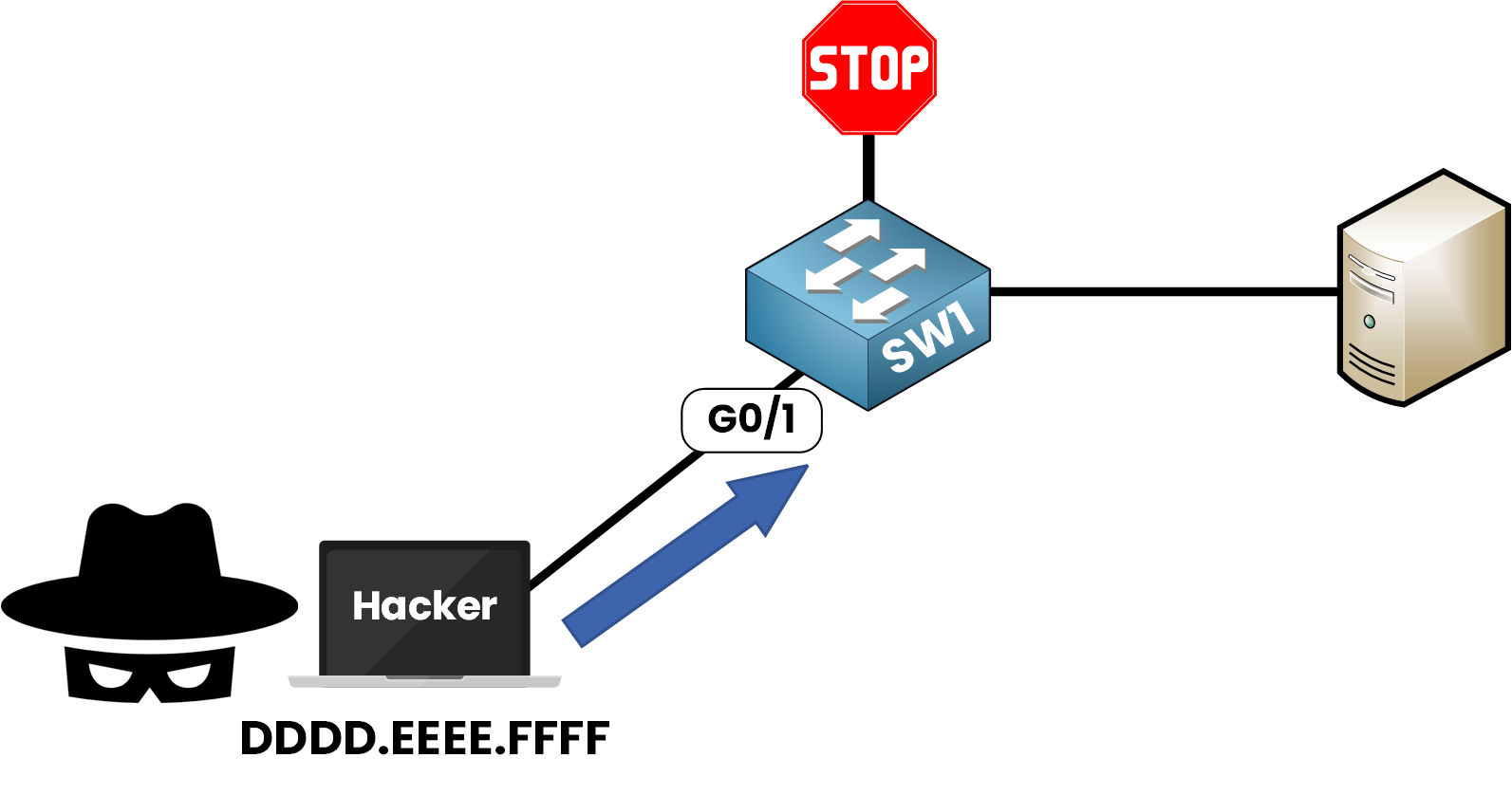
Figure 2 – Unauthorized Device Blocked by Port Security
How Port Security Works
Port Security is a Layer 2 feature.
It verifies the source MAC address of each incoming frame and checks if it matches an allowed address for that port.
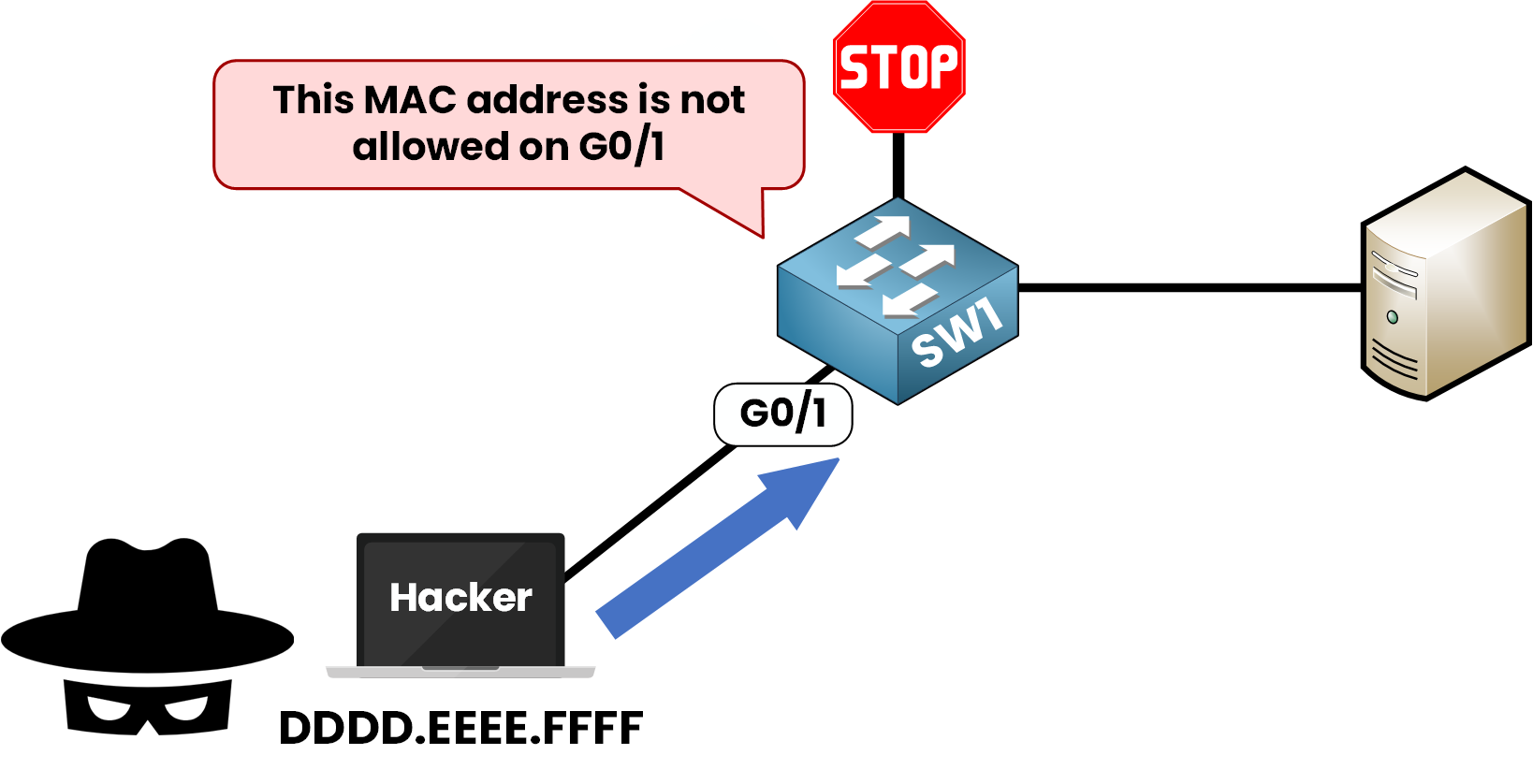
Figure 3 – MAC Address Violation Detected by Port Security
With Port Security, administrators can:
Choose what happens when a violation occurs
Define which devices are allowed on which ports
Limit the number of MAC addresses per port
Answer the question below
Which type of address does Port Security verify to control access on a switch port?
When configuring Port Security, you can decide how the switch will recognize trusted devices.
Cisco supports three key methods:Dynamic learning (automatic)
Static assignment (manual)
Multiple MAC addresses per port (for shared port)
Let’s explore each option with simple examples.
Dynamic Learning (Default)
The default method is called Dynamic Learning.
We enable Port Security on the interface.
The legitimate device is connected and sends traffic through the port.
The switch dynamically learns the MAC address and considers it trusted.
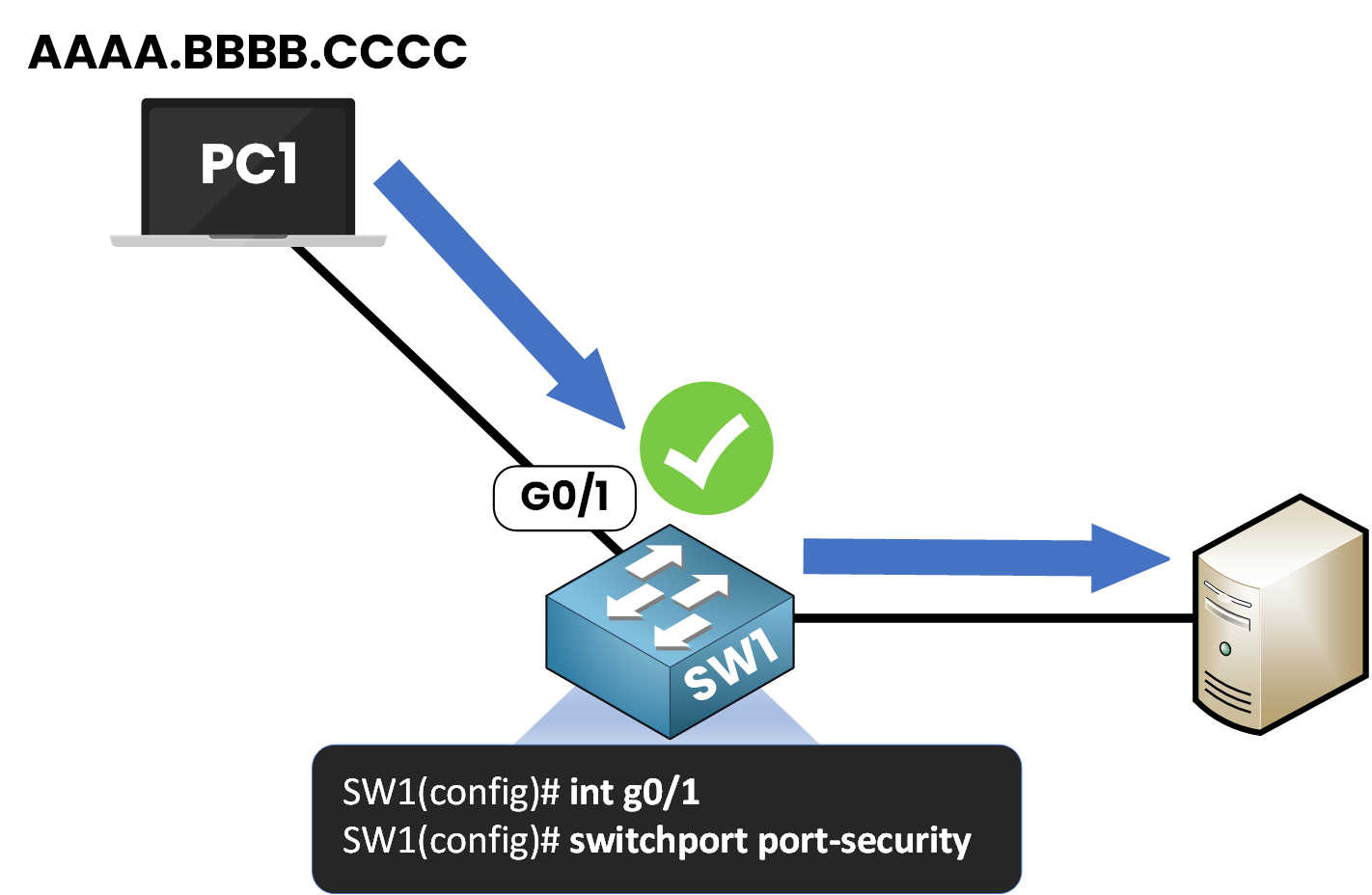
Figure 4 – Dynamic Learning of MAC Address with Port Security
By default, only one MAC address is allowed per port. Any additional device will cause a violation.
Static Configuration
In environments where strict control is needed, you can manually assign the MAC address allowed on a port.
For example, if we have a device with MAC address AAAA.BBBB.CCCC, we can statically configure the switch port to only accept frames from this MAC address.
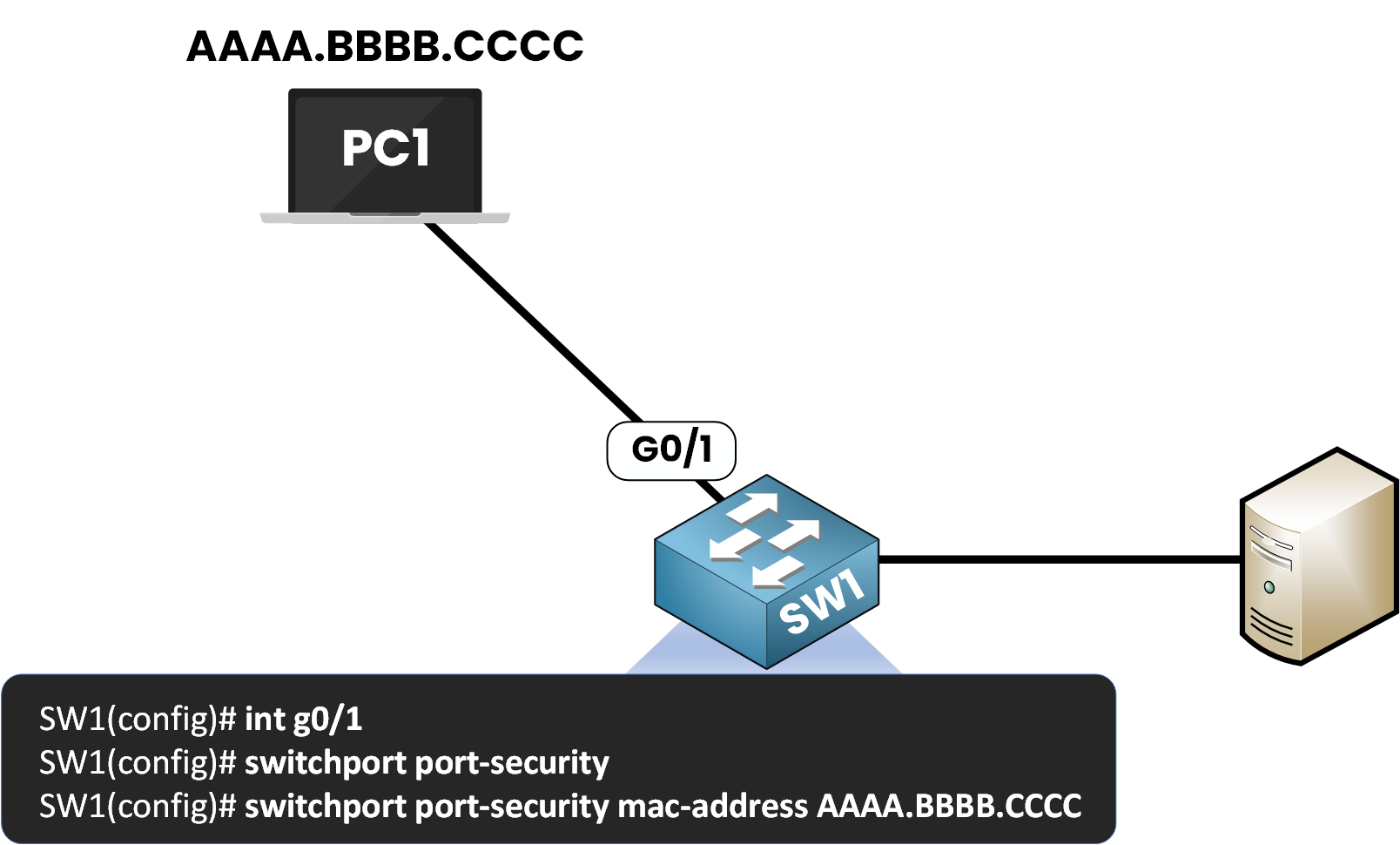
Figure 5 – Static MAC Address Configuration with Port Security
This means only the device with MAC AAAA.BBBB.CCCC will be accepted.
This method is very strict, but it requires more manual effort, especially when managing many interfaces.
Number of Allowed MAC Addresses
By default, only 1 MAC address is permitted per port.
However, in cases where multiple devices share a port (PC and an IP phone connected to a switch), we can modify the maximum number of allowed MAC addresses.
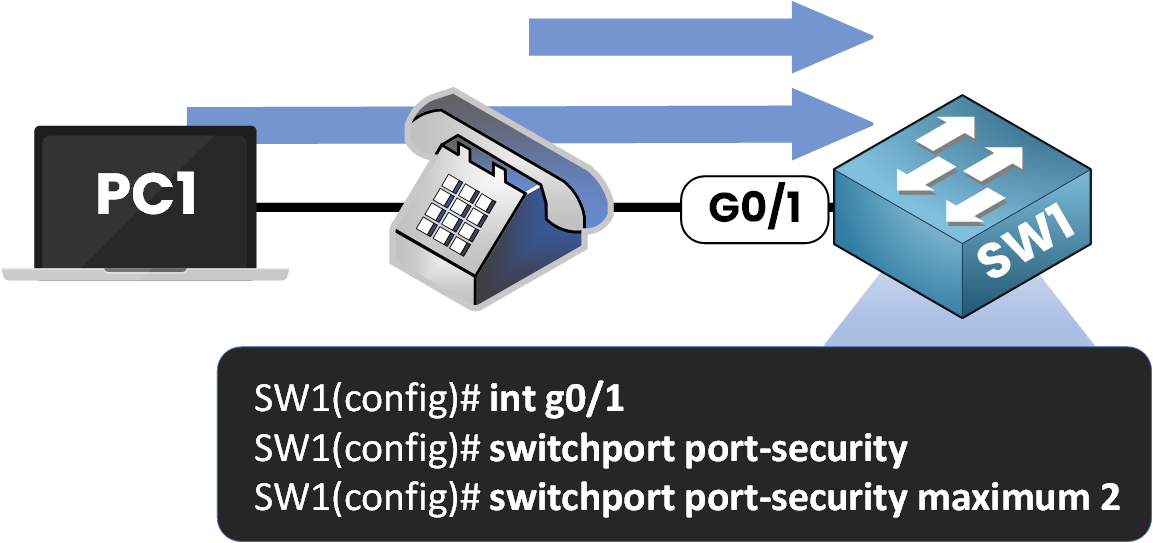
Figure 6 – Allowing Multiple MAC Addresses on a Single Port
In this example, the switch is configured to dynamically learn and allow 2 MAC addresses on the same port.
Answer the question below
What’s the default number of MAC addresses allowed per port?
Now that you’ve configured Port Security, let’s examine how the switch reacts under default settings and what happens when an unauthorized device connects.
Step 1 – Understanding the Default Behavior
Imagine PC1 is connected to SW1 on interface g0/1.
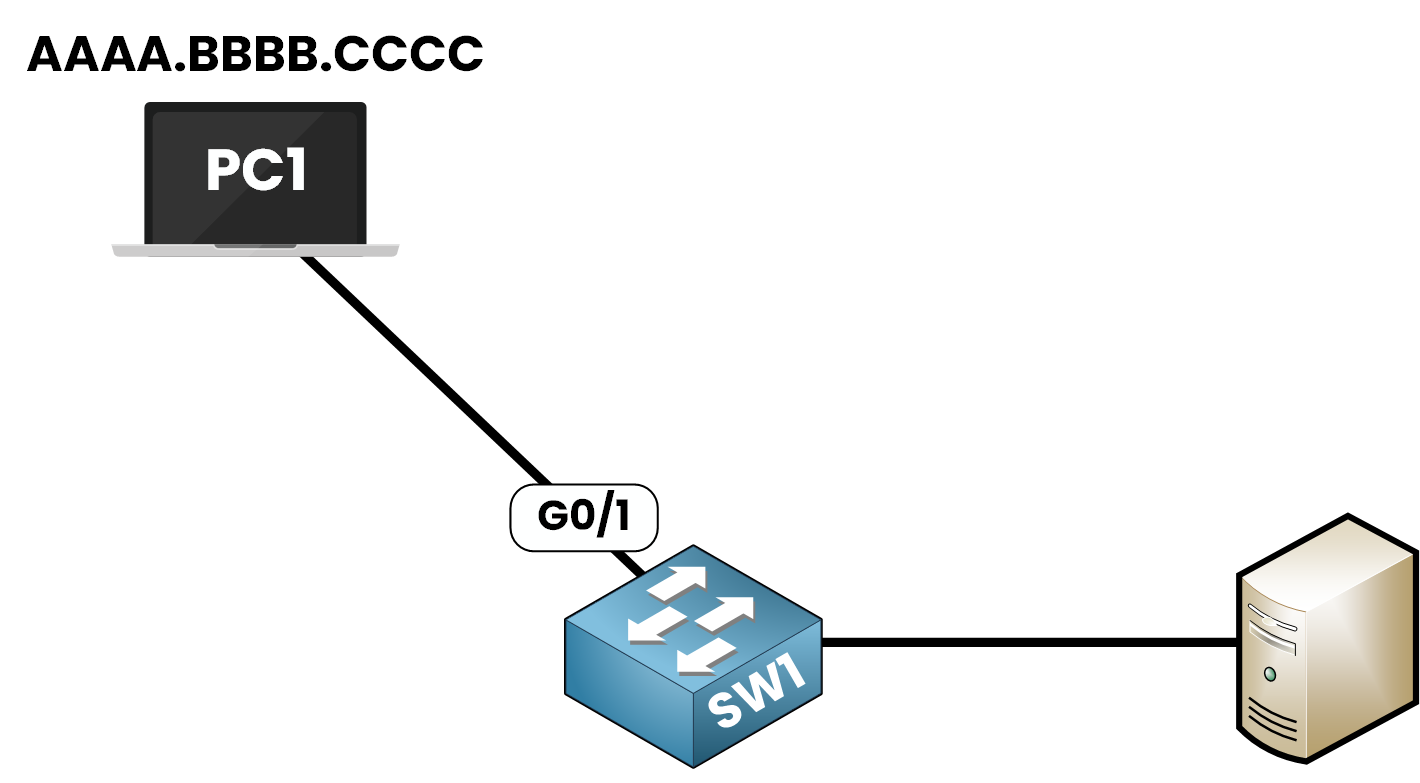
Figure 7 – Port Security Topology
When Port Security is enabled with default settings:
✅ The first MAC address that sends traffic is learned and trusted.
🚫 Any other MAC address on the same port causes a security violation.Step 2 – Enabling Port Security
Let’s try enabling Port Security:
SW1# conf t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# int g0/1 SW1(config-if)# switchport port-security Command rejected: GigabitEthernet0/1 is a dynamic port.You might get this error:
This happens because Port Security cannot be enabled on a port in dynamic auto mode.Step 3 – Fixing the Interface Mode
Set the interface to access or trunk mode before enabling Port Security
First, verify the current mode:
SW1(config-if)# end SW1# show interfaces g0/1 switchport Name: Gi0/1 Switchport: Enabled Administrative Mode: dynamic auto Operational Mode: static access !!! Output omitted !!!Now reconfigure the interface:
SW1# conf t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# int g0/1 SW1(config-if)# switchport mode accessWe can enable Port Security:
SW1(config-if)# switchport port-security SW1(config-if)# endStep 4 – Verifying Port Security
To check the current configuration:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0000.0000.0000:0 Security Violation Count : 0At this stage:
The port is active.
No MAC address has been learned yet.
The port is waiting for traffic to identify the first device.
Step 5 – When Traffic Is Detected
As soon as PC1 sends a frame, the switch learns its MAC address:
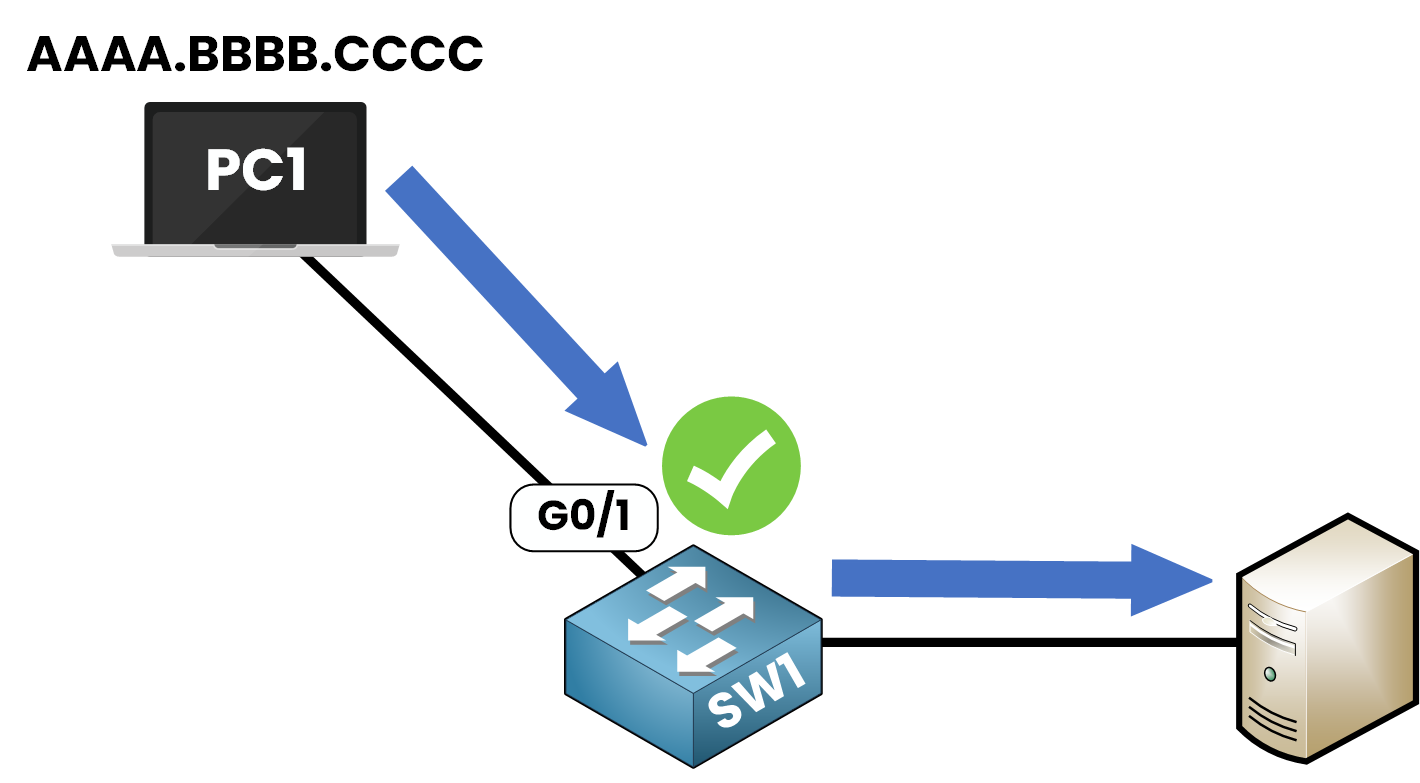
Figure 8 – MAC Address Learned After Traffic Detection
Check the updated status:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : AAAA.BBBB.CCCC:1 Security Violation Count : 0✅ The MAC address AAAA.BBBB.CCCC is now trusted.
🚫 Any other MAC address will trigger a violation.Step 6 – What If an Unauthorized Device Connects?
Let’s say someone plugs in a second device using MAC DDDD.EEEE.FFFF.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Port Security
Port Security is a Cisco switch feature that restricts access to interfaces by controlling which MAC addresses are allowed. This lesson shows how it protects against rogue devices, how to configure it, and how to recover from violations.