In the previous lesson, you learned that wireless security relies on three core principles: authentication, encryption, and integrity. These principles define what must be protected, but they do not explain how protection is implemented on a Wireless network.
We will now look at the various wireless security protocols that implement these protections on Wi-Fi networks.
They define how a wireless client authenticates, how data is protected, and how integrity is ensured.Open Authentication
Open Authentication is the simplest possible authentication method.
It provides no built-in security.As shown in Figure 2, the client sends an authentication request to the access point, and the access point accepts all authentication requests without verifying any credentials.
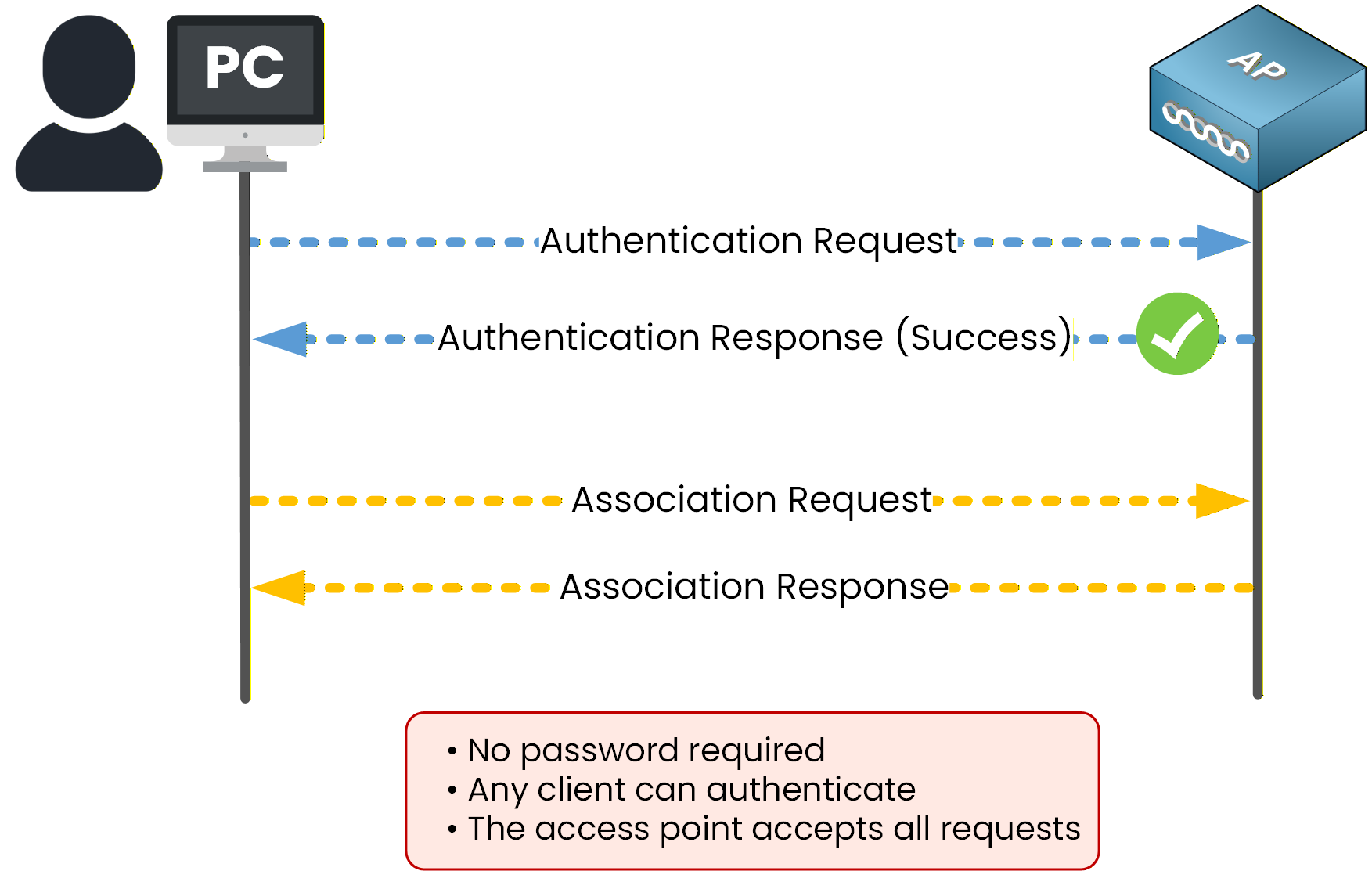
Figure 1 - Open authentication
In this model:
No password is required
Any client can authenticate
The access point does not verify the identity of the client
This type of authentication is commonly found in public Wi-Fi networks such as airports, cafés, or hotels.
⚠️ Important:
Because Open Authentication does not verify client identity and provides no encryption or integrity protection, the wireless network itself is not secure.From Open Authentication to Shared Secrets
Because Open Authentication provides no real security, additional mechanisms are required to protect wireless networks.
At a high level, wireless authentication mechanisms can be grouped into two categories:
Open Authentication
Authentication based on a shared secret
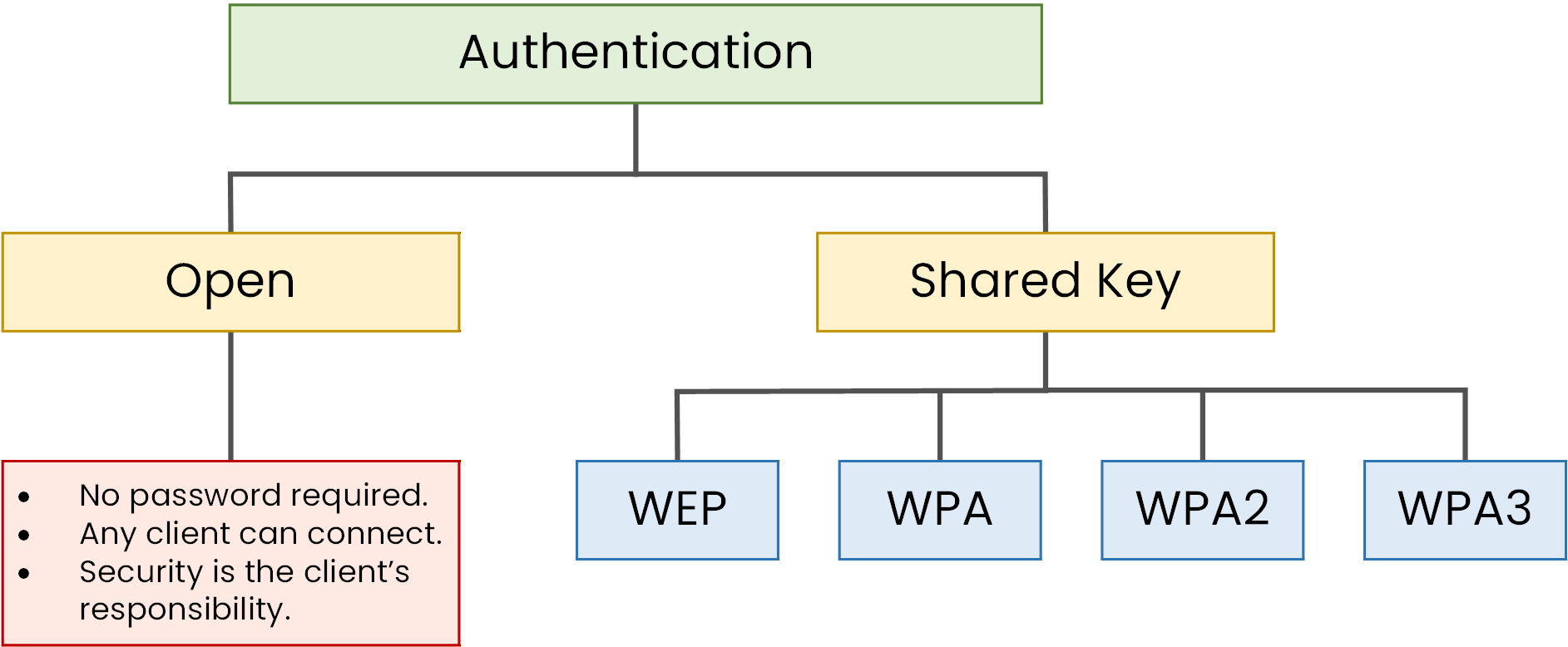
Figure 2 - Wireless authentication methods
Figure 2 summarises this evolution, showing how wireless security protocols have changed over time.
Answer the question below
Shared Key–Based Security
Shared key–based security requires the client and the access point to share a secret.
This shared secret is used as the basis for authenticating clients and protecting wireless traffic.All major wireless security protocols rely on shared secrets in some form:
WEP
WPA
WPA2
WPA3
Each new protocol improves how the shared secret is used, how encryption is performed, and how integrity is ensured.
Let’s start with WEP, the first wireless security protocol to implement a shared secret.Answer the question below
What is required by Shared Key Authentication to authenticate a wireless client?
Wired Equivalent Privacy (WEP) was the first wireless security protocol defined by the IEEE 802.11 standard. It was introduced in 1997 with the goal of providing a level of security for wireless networks comparable to wired networks.
The design of WEP was based on a shared secret key configured on both the client and the access point.
This key was used for authentication, encryption, and integrity protection.WEP Process
To understand WEP, let's look at a practical example, you are your PC attempting to authenticate to a WEP-protected wireless network.
Authentication
You send an Authentication Request to the access point.
The access point replies with a challenge, which is a random value sent in plaintext.
You encrypt this challenge using the shared WEP key and the RC4 algorithm.
You send the encrypted challenge back to the access point.
The access point decrypts the response using its own copy of the shared key.
If the decrypted value matches the original challenge, the access point sends an Authentication Response (Success).
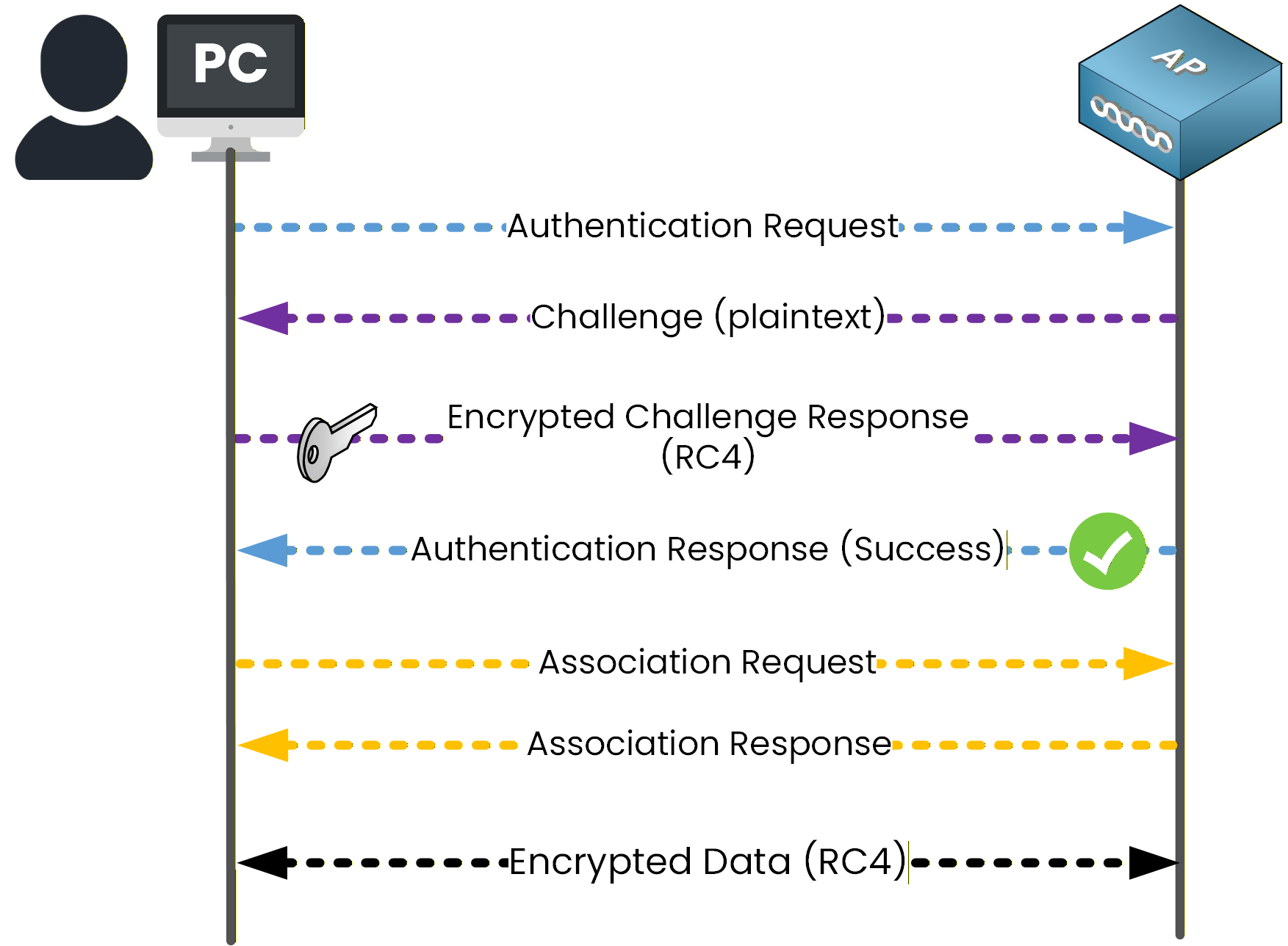
Figure 3 - WEPThe purpose of the challenge is to verify that both you and the access point possess the same shared secret key, without transmitting the key itself over the air.
Answer the question below
Which encryption algorithm is used by WEP?
Association
After successful authentication:
You send an Association Request to the access point.
The access point replies with an Association Response, allowing your device to join the wireless network.
Encrypted Data Transmittion
Once association is complete:
All wireless traffic is encrypted using the RC4 stream cipher.
CRC (Cyclic Redundancy Check) is used to verify data integrity.
CRC is not a secure integrity mechanism and does not protect against intentional data modification.
WEP Characteristics
At first glance, WEP appears to be a complete wireless security protocol because it includes mechanisms for authentication, encryption, and integrity.
Authentication: Open System, Shared Key
Encryption: RC4
Integrity: CRC
However, WEP is an old protocol. Over time, attackers discovered multiple security weaknesses in its design, including flaws in key management, encryption implementation, and integrity checking.
These vulnerabilities made WEP easy to break and unsuitable for modern wireless networks. As a result, the industry had to improve wireless security standards.
In the next section, we will see how WPA was introduced to address these weaknesses and enhance wireless security.
Answer the question below
Which mechanism does WEP use to verify data integrity?
Wi-Fi Protected Access (WPA) was introduced in 2003 by the Wi-Fi Alliance as an interim solution to fix the most critical security weaknesses of WEP, while remaining compatible with existing hardware.
Instead of redesigning everything from scratch, WPA kept the shared key concept but significantly improved key management and integrity protection.
WPA introduced two operating modes that are still used today:
WPA Personal — for home and small networks
WPA Enterprise — for enterprise environments using centralized authentication
WPA Personal
WPA Personal is designed for home users and small offices.
It relies on a Pre-Shared Key (PSK) configured on both the client and the access point.40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally