Wireless security protects Wi-Fi networks from many potential threats that you might not even think about.
Unlike wired connections, wireless signals travel through the air, which makes them easier to capture or exploit.Without wireless security, attackers can listen to traffic, impersonate access points, or alter data in transit.
In this lesson, you'll learn about the most common wireless attacks and how we can protect ourselves against them.Eavesdropping
Let's imagine a university campus with Wi-Fi everywhere. It's in classrooms, libraries, and even outside.
At first this principe seem great but you need to understand that wireless signals don’t stop at the walls. They extend beyond the building, allowing anyone nearby to capture them.In Figure 1, you can see how this happens. PC1 sends wireless frames to the access point, but a hacker outside the building can also receive them.

Figure 1 - Wireless signals leak outside the building
Even without connecting to the Wi-Fi network, the attacker can listen to the communication taking place in the air.
This is called eavesdropping, which means someone can silently intercepting wireless signals as they travel between a device and an access point. If the wireless traffic is not encrypted, the attacker can easily read the data being exchanged.
Rogue AP
Now imagine that the attacker takes it one step further.
Instead of only listening wireless traffic, they create their own fake access point using the same SSID as the real network.In Figure 2, the user sees two Wi-Fi networks with the same SSID, “University Network.”
Since the fake access point has a stronger signal, PC1 automatically connects to it, thinking it is the legitimate network.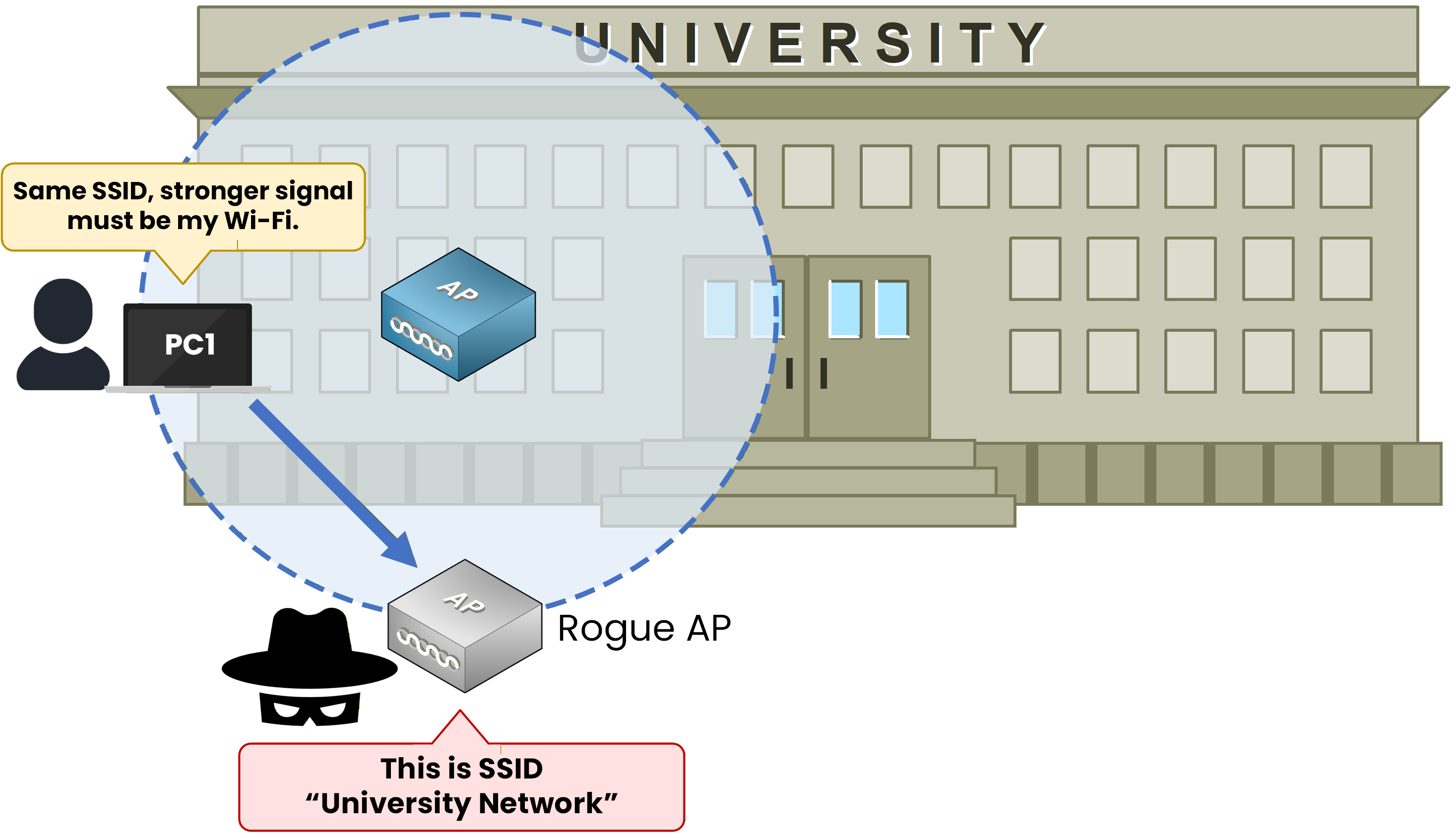
Figure 2 - Rogue AP mimics the real Wi-Fi to trick users into connecting.
Once connected, all of the user’s traffic goes through the attacker’s device, allowing them to monitor or modify the data in real time.
This type of attack is called a Rogue Access Point.
It tricks users into joining a fake Wi-Fi network that seems real. This gives the attacker complete control over the communication.Once the attacker controls the traffic, the next step is to manipulate it.
Data Tampering
After eavesdropping or setting up a rogue access point, an attacker can go even further.
Instead of just listening traffic or tricking users into false access point, they can intercept and alter the data being transmitted.Figure 3 shows PC1 transmitting wireless frames to the access point. An attacker first captures those frames, modifies their content, and then forwards them to the access point so the traffic looks legitimate.

Figure 3 - Attacker intercepts, alters and forwards PC1's wireless frames to the server.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Wireless Security Fundamentals
Every day, millions of devices connect to Wi-Fi at home, in offices, and in public spaces. But few people realize how easily these networks can be attacked.