Imagine you're managing a network, and, for example, an interface goes down on your router. How do you find out what happened?
This is where SYSLOG protocol can help you! It’s a standardized protocol used by network devices like routers and switches to send status updates and alerts.
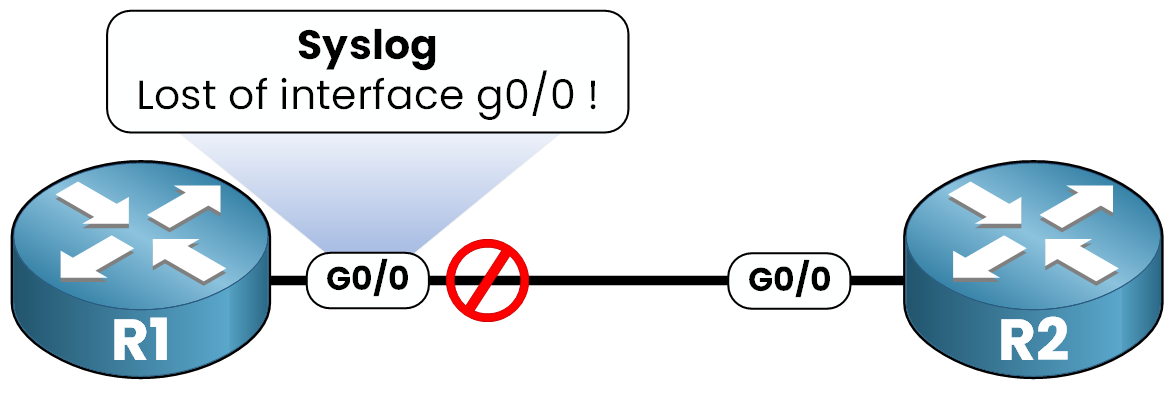
Figure 1 – Syslog message triggered when interface g0/0 goes down
If an interface goes down on our Router R1, SYSLOG will immediately generates a message like this:
R1# %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to downThis message tells you that the interface is no longer operational !
Answer the question below
What protocol is used by network devices to send status updates and alerts?
When a Cisco device detects an event, such as an interface going down, it generates a SYSLOG message. This message can be sent to different destinations, depending on how your device is configured.
Let’s look at each logging method and how it behaves in practice.
Console Logging
When you're physically connected to the router through the console port, SYSLOG messages are displayed in real time on your terminal.
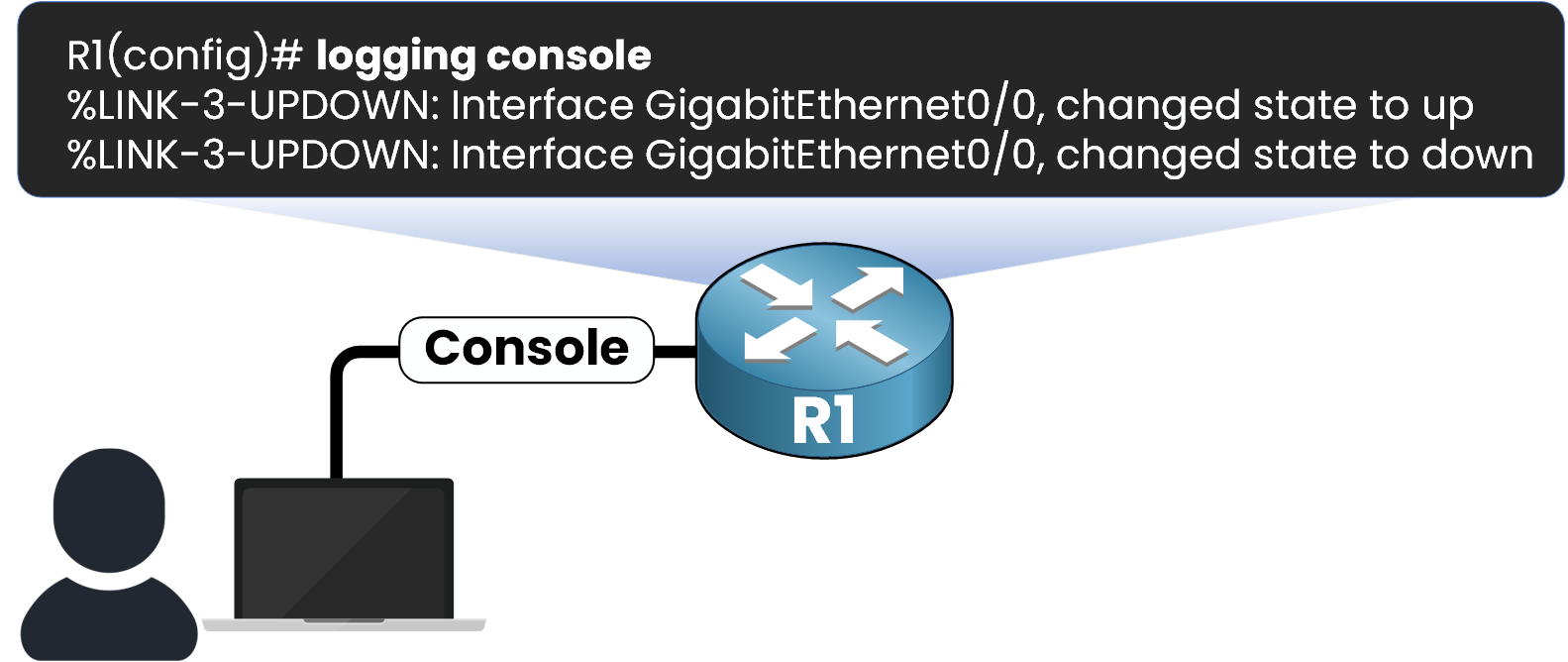
Figure 2 – Syslog messages displayed live through the console connection
This type of logging is enabled by default and is ideal for local troubleshooting during initial configuration. The logging console command can be used if your device has console logging disabled!
But let's me tell you, if the session is closed or the device reboots, all logs are lost...
Terminal Logging (Telnet/SSH)
When connecting remotely via SSH or Telnet, SYSLOG messages are not displayed by default. To see them, you need to explicitly enable real-time logging on your session by using the terminal monitor command.
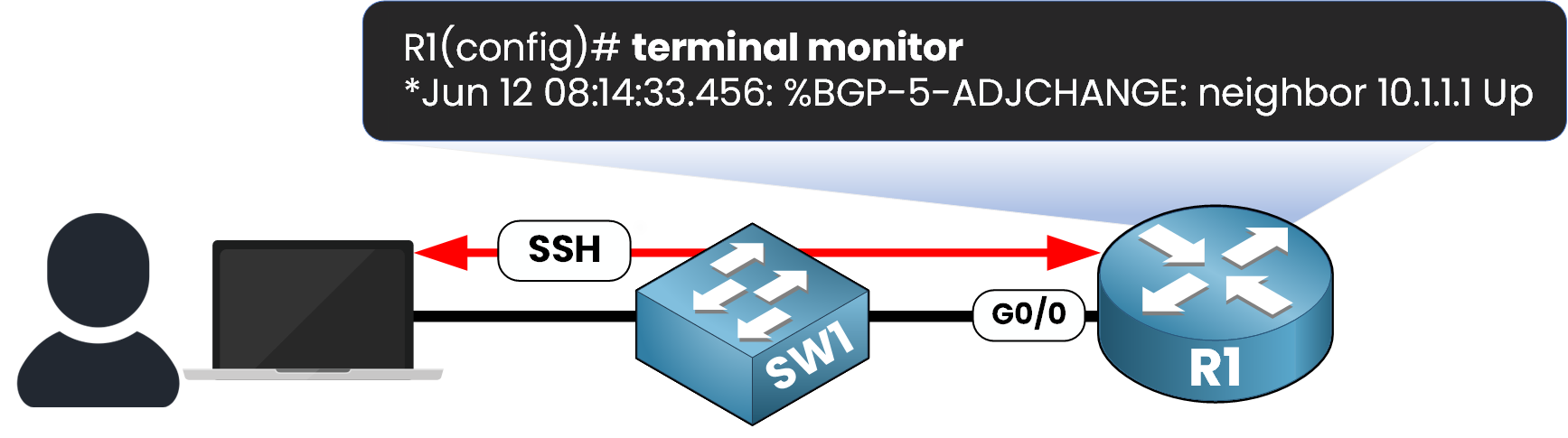
Figure 3 – Real-time logging over SSH or Telnet using the terminal monitor command
This command affects only your current session and must be re-entered if you reconnect to the device.
Buffered Logging (RAM)
Buffered logging allows you to store log messages temporarily in RAM.
This means you can view them even after an event has occurred as long as the device hasn't rebooted.You can choose how much memory to allocate for logging.
Let's me show you how to configure buffered logging:
R1(config)# logging buffered ? <0-7> Logging severity level <4096-2147483647> Logging buffer size (default is 4096) alerts (level 1) critical (level 2) debugging (level 7) emergencies (level 0) errors (level 3) informational (level 6) notifications (level 5) warnings (level 4)R1(config)# logging buffered 16384 4This command sets 16,384 bytes of buffer space and stores only logs with severity 4 (warnings) and higher. (We will see severity levels in part 4)
To review the logs use the command show logging:
R1# show logging Syslog logging: enabled (0 messages dropped, 0 flushes, 0 overruns) Console logging: level debugging, 7 messages logged, xml disabled, filtering disabled Monitor logging: level debugging, 0 messages logged, xml disabled, filtering disabled Buffer logging: level warnings, 36 messages logged, xml disabled, filtering disabled Exception Logging: size (4096 bytes) Count and timestamp logging messages: disabled Persistent logging: disabled Trap logging: level informational, 39 message lines logged Logging to 192.168.10.1 via udp on port 514 Logging Source-Interface: not set VRF Name: (default) Log Buffer (16384 bytes): *Jun 12 08:14:21.012: %SYS-5-CONFIG_I: Configured from console by admin on vty0 (192.168.1.100) *Jun 12 08:14:22.123: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up *Jun 12 08:14:23.315: %LINK-3-UPDOWN: Interface GigabitEthernet0/2, changed state to down *Jun 12 08:14:24.417: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to down *Jun 12 08:14:27.789: %SEC-6-IPACCESSLOGP: list 101 permitted tcp 10.1.1.5(51304) -> 172.16.1.10(22), 1 packet *Jun 12 08:14:31.456: %SYS-5-CONFIG_I: Configured from memory by console *Jun 12 08:14:33.111: %BGP-5-ADJCHANGE: neighbor 10.1.1.1 Up *Jun 12 08:14:35.962: %SYS-4-WARNING: High CPU utilization detected on process 'routing'Syslog Server (Centralized Storage)
In enterprise environments, logs are sent to a central Syslog server for long-term storage. This allows you to keep a complete history of events from multiple devices in one place.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Syslog
Syslog in Cisco devices is a protocol that records events like interface changes, errors, or configuration updates and sends them to different destinations. In this lesson, you will learn how to configure Syslog and interpret its messages for troubleshooting and monitoring.