Every packet traveling across a network starts with something essential: its header.
Before any data can move from one device to another, routers need instructions.
Those instructions are stored inside the IPv4 Packet Header, right at the beginning of the packet.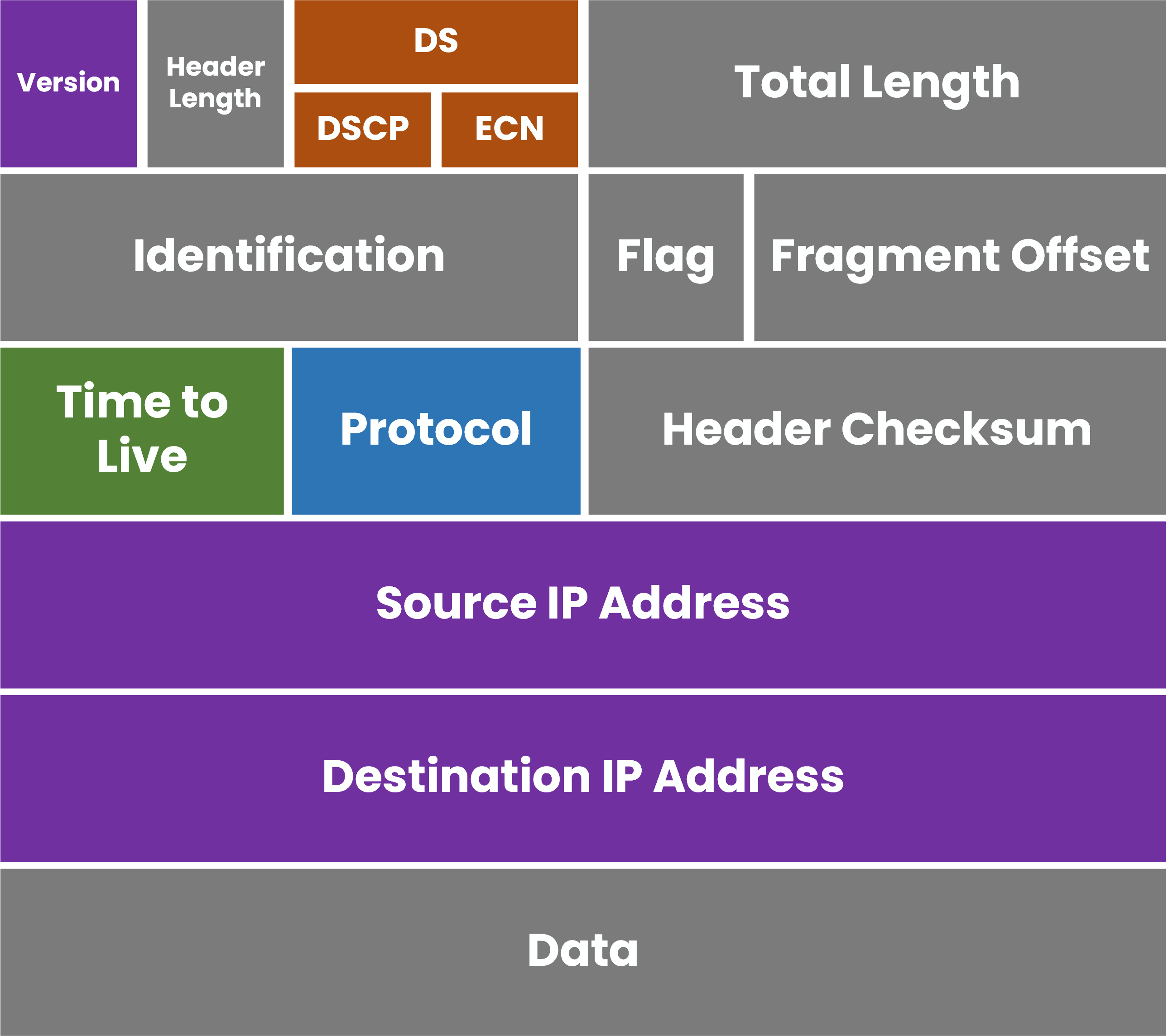
Figure 1 – IPv4 Packet Header Structure
This small section of information guides the router on how to handle the packet.
It tells the router where the packet came from, where it should go, how long it can stay, and how to check for any corruption during its journey.When you open Wireshark or troubleshoot a network, you’re constantly looking at these headers.
Without them, data wouldn’t reach its destination or might loop forever in the network.Why the IPv4 Header Matters
Each field inside the IPv4 header has a clear, technical purpose.
Some are used by routers to forward packets, others to detect errors or handle congestion.
And even though the header looks complex, you’ll see that only a few fields truly matter in real-world troubleshooting.Now that you understand why the header exists, let’s explore its structure field by field.
→ This will make it much easier to read and interpret IPv4 packets later in Wireshark.
Answer the question below
Now that you know why the IPv4 header exists, let’s look at what it contains.
Each field plays a specific role in how routers handle and forward packets through the network.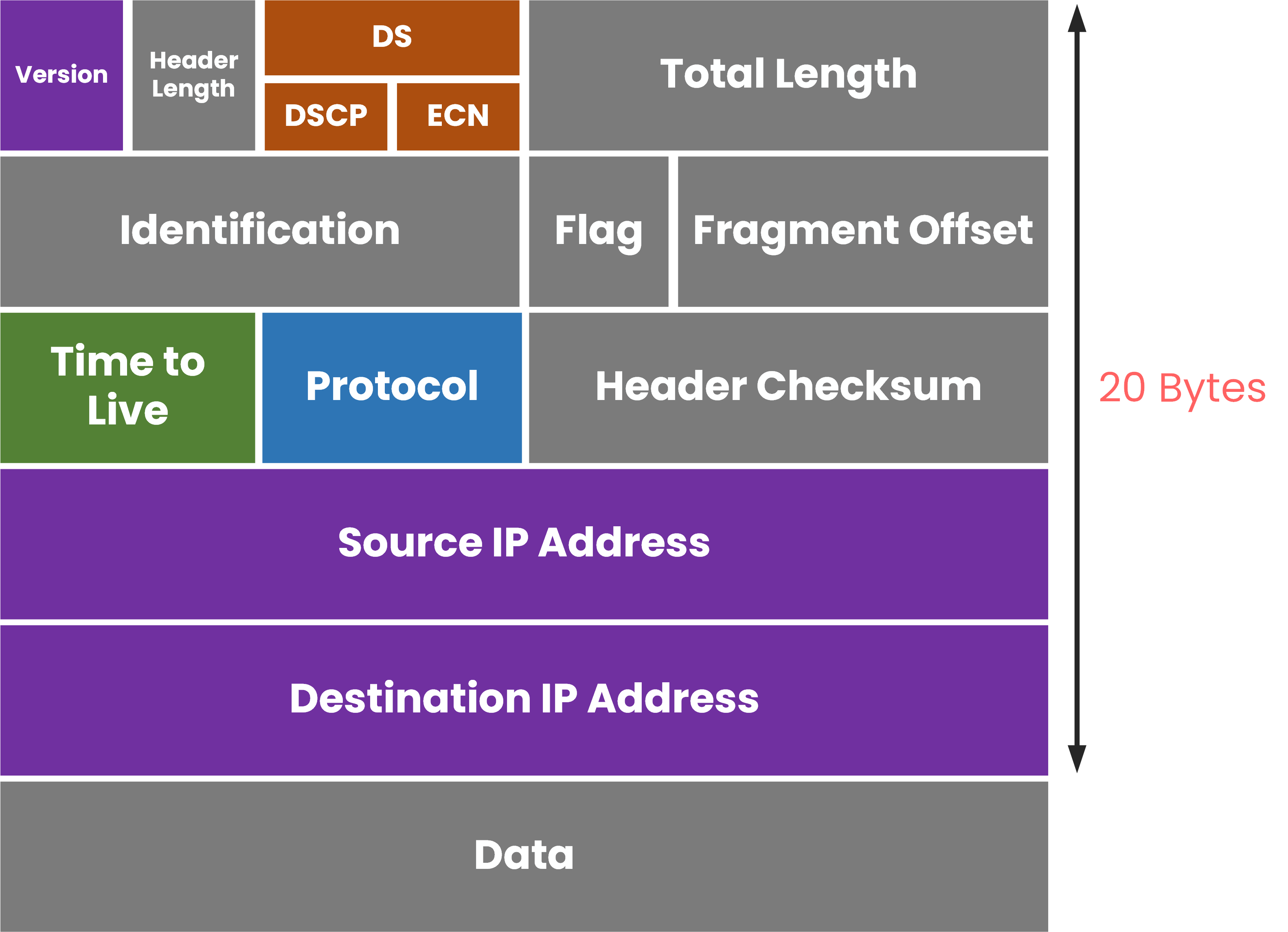
Figure 2 – IPv4 Packet Header (20 Bytes)
Source IP Address and Destination IP Address
These fields indicate where the packet comes from and where it is going.
Routers use them to forward packets toward their correct destination, based on entries in the Routing Table.Time to Live (TTL)
The TTL field defines how long a packet can remain in the network. Each router decreases the TTL by 1 before forwarding the packet. When it reaches 0, the packet is discarded, and an ICMP Time Exceeded message is sent back to the source host. This prevents packets from looping endlessly.
Protocol
The Protocol field identifies the transport-layer protocol encapsulated inside the packet.
Common values include:1→ ICMP6→ TCP17→ UDP
This tells the receiving device which upper-layer process should handle the data.
Answer the question below
Which IPv4 field identifies the IP version being used?
DSCP and ECN
These fields belong to the Differentiated Services (DiffServ) model.
They are used for Quality of Service (QoS) to mark packets for priority or congestion handling.DSCP defines the packet’s priority level.
ECN indicates congestion without dropping packets.
Header Checksum
The Header Checksum ensures the IPv4 header hasn’t been corrupted in transit.
When a router modifies the header (for example, when it decreases TTL), it recalculates the checksum before forwarding the packet.Version and Header Length
The Version field identifies which IP version is used.
If it’s set to 4, the packet is an IPv4 packet.
The Header Length (IHL) field indicates the header size in 32-bit words.
The minimum header size is 20 bytes (IHL = 5), which corresponds to a header without optional fields.Answer the question below
Which IPv4 field indicates the size of the header?
Total Length
The Total Length field specifies the complete size of the IPv4 packet in bytes including both the header and the data.
Its maximum value is 65,535 bytes, which is the largest number that can be represented with 16 bits.Identification, Flags, and Fragment Offset
These fields are used when a packet is fragmented to cross a link with a smaller MTU (Maximum Transmission Unit).
Identification keeps track of which fragments belong to the same packet.
Flags indicate if fragmentation is allowed or if more fragments follow.
Fragment Offset tells where each fragment fits when the packet is reassembled.
For the CCNA exam, you don’t need to memorize the details of how fragmentation works, just remember that these fields exist to handle packets that are too large for the network’s MTU.
Data (Payload)
The Data section is not part of the IPv4 header.
It carries the encapsulated segment, such as TCP, UDP, or ICMP, that will be processed by upper-layer protocols.As a network administrator, you need to recognize these key fields in Wireshark to interpret how packets move through the network. Let’s now look at a real IPv4 packet to see how these fields appear in practice.
Answer the question below
Which IPv4 field prevents infinite loops?
Now that you understand the purpose of each field, let’s bring everything together with a real example.
Here, PC1 opens an HTTPS session to the PingMyNetwork web server.
Each packet crossing the network includes an IPv4 Packet Header filled with real operational values that routers use to forward it correctly.
Figure 3 - PC1 sends traffic to PingMyNetwork webserver
Routers along the path don’t look at the data inside the packet.
They only inspect the header to decide where to send it next.
That’s the foundation of how the Internet works: routers read headers, not content.Visualizing the Header in Action
Before opening Wireshark, let’s look at what a complete IPv4 header looks like when filled with real values from this HTTPS connection.
Understanding these values will make it easier to recognize them later in the capture.In Figure 4, you can see each field of the IPv4 header represented with the real information routers process:
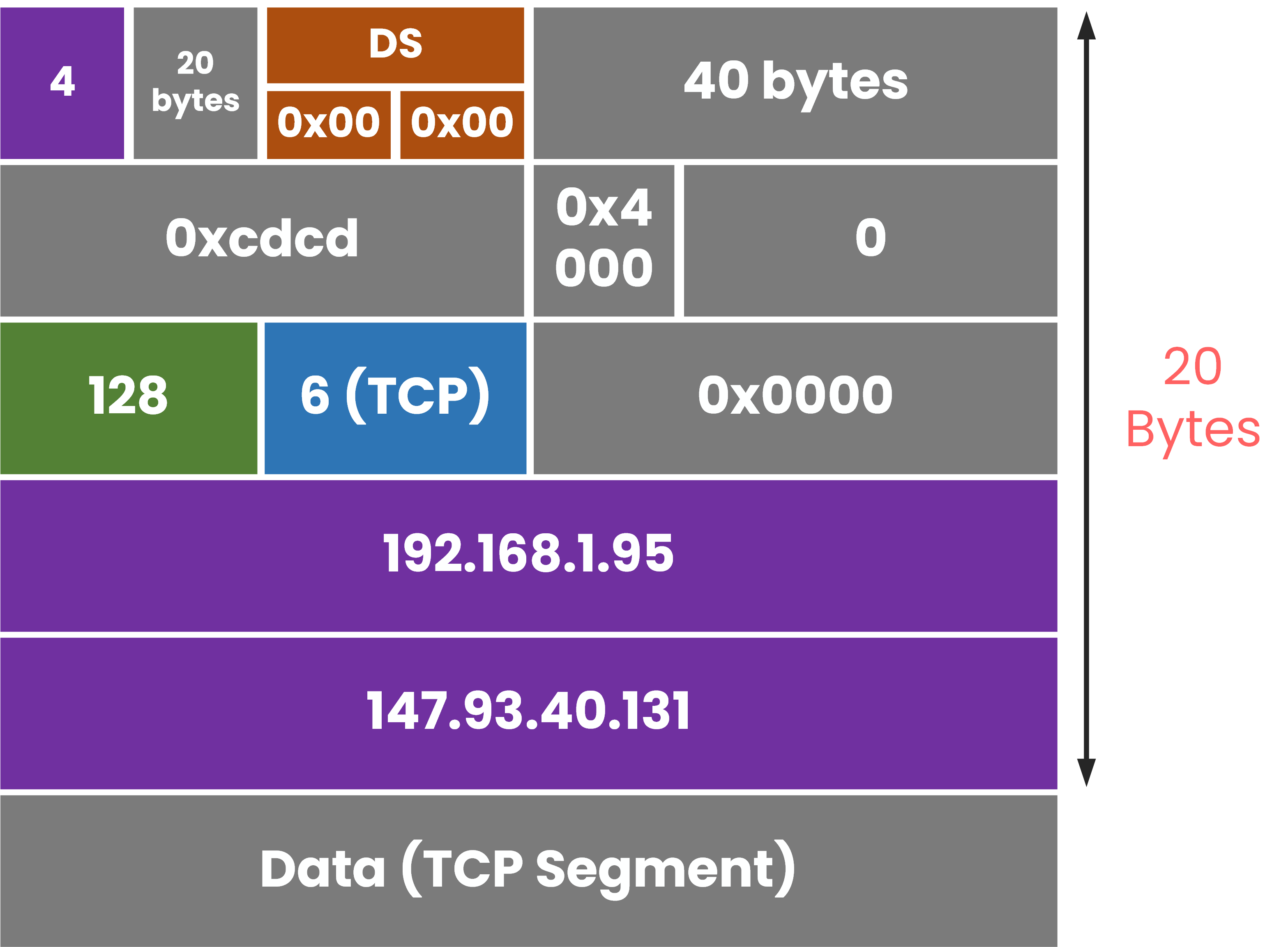
Figure 4 – Example of a Filled IPv4 Packet Header
Each of these values can be observed directly in the real capture below.
Inspecting the Packet in Wireshark
Let’s now open this same packet in Wireshark and expand the Internet Protocol Version 4 section.
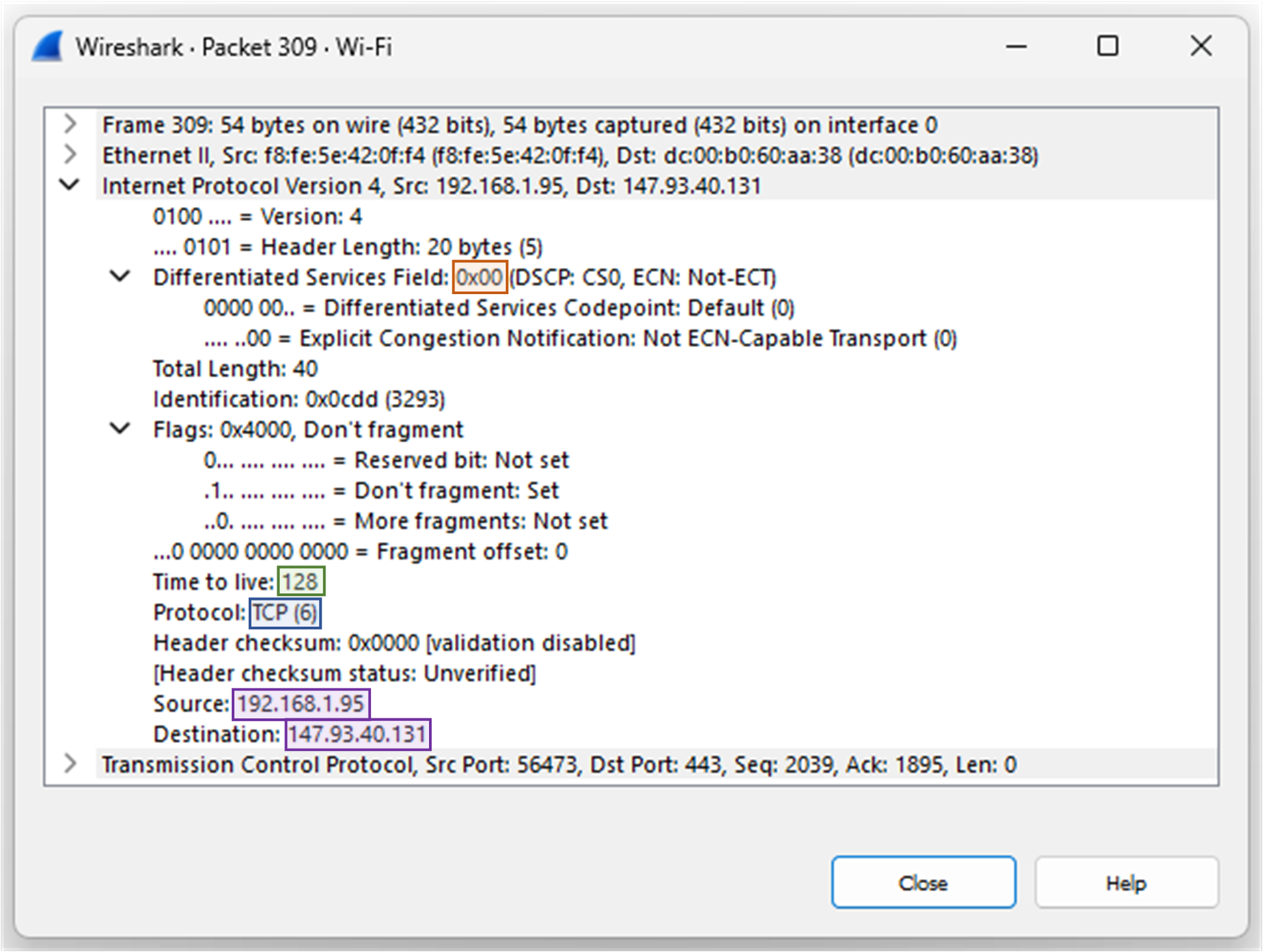
Figure 5 – IPv4 Packet Header Example in Wireshark
From this capture, you can confirm:
The Source (192.168.1.95) and Destination (147.93.40.131) match our example.
The TTL = 128 suggests the packet originated from a Windows host (Linux typically starts with 64).
The Protocol = 6 (TCP) confirms the packet is part of an HTTPS session.
The Checksum ensures that the header hasn’t been corrupted in transit.
These fields aren’t just numbers, together, they describe how the packet travels across the network and how routers make forwarding decisions.
Answer the question below
If the IPv4 header shows Protocol = 6, which transport protocol is being used?
At first glance, the IPv4 header may look complex, but it’s simply the packet’s instruction sheet,
telling routers exactly how to deliver data safely and efficiently.By now, you’ve seen that only a few fields truly matter in everyday troubleshooting:
the Source and Destination IP addresses, the TTL, the Protocol, and the Header Checksum.
These are the ones you’ll read most often in Wireshark or during network diagnostics.Every other field, such as fragmentation or QoS marking, serves specific use cases, but they all contribute to one thing:
making sure that data can travel reliably across the network.Key takeaway
The IPv4 header is the “instruction sheet” of every packet.
Without it, routers wouldn’t know how to forward, protect, or even recognize the data they carry.
Answer the question below