This DHCP Snooping configuration guide explains how to secure a Cisco switch against rogue DHCP servers, using a simple and practical topology.
We’ll use a simple topology: a router (R1) as the DHCP server and a PC connected through a switch.
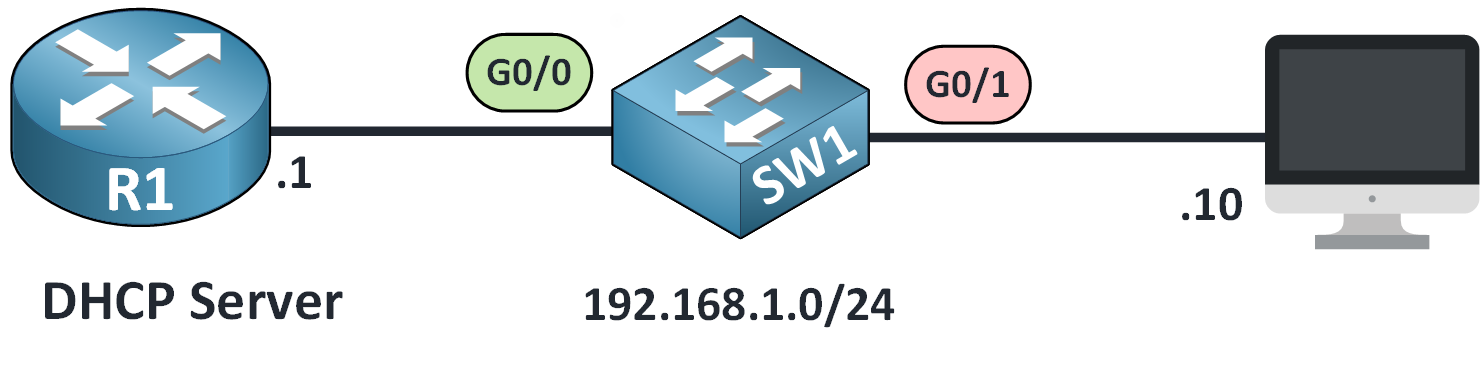
Figure 1 – DHCP Snooping Configuration Topology
Enable DHCP Snooping
First, we need to enable the feature globally:
SW1# conf t Enter configuration commands, one per line. End with CNTL/Z. SW1#(config)# ip dhcp snoopingDefine VLAN to Protect
Next, we specify the VLAN where DHCP Snooping should operate.
By default, we’ll use VLAN 1.
SW1#(config)# ip dhcp snooping vlan 1This tells the switch to inspect and filter DHCP traffic only on this VLAN.
Set Trusted Interface
By default, all interfaces are untrusted, which means the switch blocks DHCP replies (like Offer and ACK) from those ports.
You need to trust the interface that connects to the legitimate DHCP server:
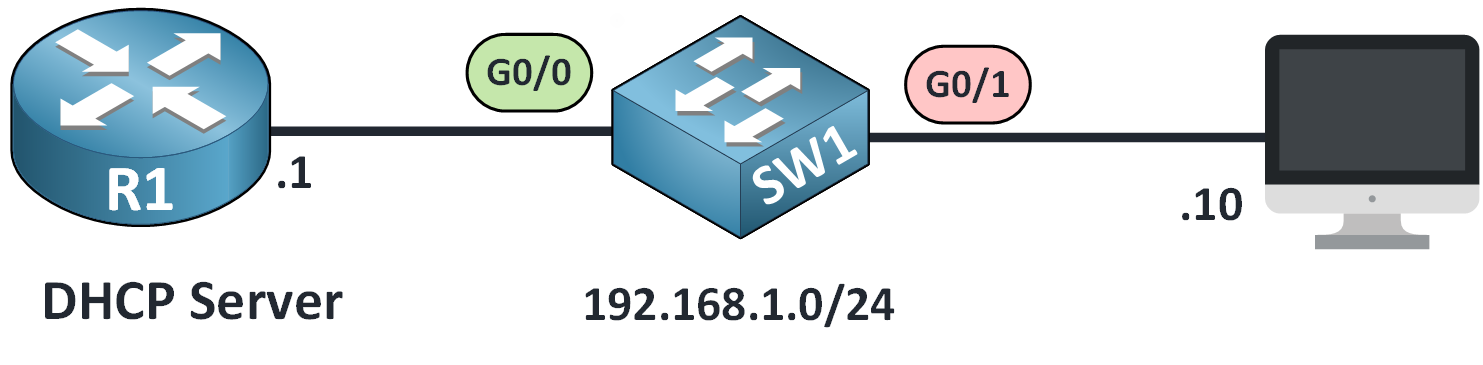
Figure 2 – Setting a Trusted Interface for DHCP Snooping
SW1(config)# int g0/0 SW1(config-if)# ip dhcp snooping trustThis allows DHCP messages from the server to reach clients. All other interfaces remain untrusted to block rogue DHCP servers.
Disabling Option 82
Cisco switches add
Option 82to DHCP messages by default.
In simple networks (without relay agents), this may cause the DHCP server to reject requests.Disable it to avoid problems:
SW1(config)# no ip dhcp snooping information option SW1(config)# endThis topic will be explained in more detail later.
Verify the Configuration
To validate your DHCP Snooping configuration, run the following command:
SW1# show ip dhcp snooping Switch DHCP snooping is enabled Switch DHCP gleaning is disabled DHCP snooping is configured on following VLANs: 1 DHCP snooping is operational on following VLANs: 1 DHCP snooping is configured on the following L3 Interfaces: Insertion of option 82 is disabled circuit-id default format: vlan-mod-port remote-id: 50f6.1504.7a00 (MAC) Option 82 on untrusted port is not allowed Verification of hwaddr field is enabled Verification of giaddr field is enabled DHCP snooping trust/rate is configured on the following Interfaces: Interface Trusted Allow option Rate limit (pps) ----------------------- ------- ------------ ---------------- GigabitEthernet0/0 yes yes unlimited Custom circuit-ids:This output confirms that your dhcp snooping configuration is active, trusted ports are correctly defined, and Option 82 is disabled.
View the Binding Table
The switch dynamically tracks legitimate clients:
SW1# show ip dhcp snooping binding MacAddress IpAddress Lease(sec) Type VLAN Interface ------------------ --------------- ---------- ------------- ---- ------------ 00:50:79:66:68:7B 192.168.10.10 86390 dhcp-snooping 1 GigabitEthernet0/1 Total number of bindings: 1What this tells us:
The MAC address and IP address of the client are recorded
The interface and VLAN match our setup
The lease time shows that the IP is still valid
This table allows the switch to track legitimate DHCP clients and block traffic from unauthorized sources.
Answer the question below
By default, what do Cisco switches add to DHCP messages that may need to be disabled in simple networks?
After completing your dhcp snooping configuration, it’s essential to protect the switch from excessive DHCP traffic that could lead to flood attacks.
A flood attacks ?
An attacker could flood the switch with fake DHCP Discover messages. This overloads the switch CPU and may cause:
The switch to stop processing DHCP properly
Security checks like DHCP Snooping to fail
Interfaces to become unstable
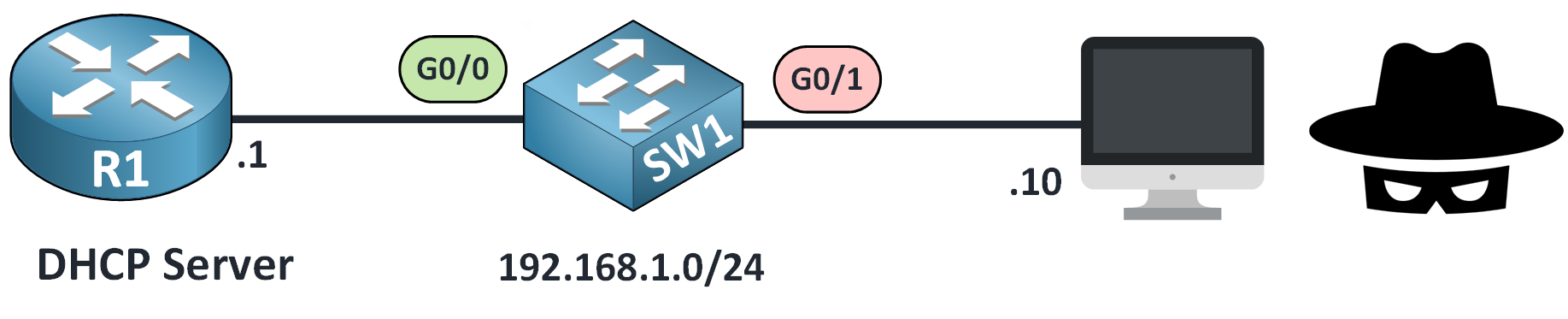
Figure 3 – DHCP Snooping Rate Limiting to Prevent Flood Attacks
To prevent this, we set a rate limit on how many DHCP packets are allowed per second.
Configure Rate Limiting
Here’s how to apply a limit of 10 packets per second on a client-facing interface.
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
DHCP Snooping Configuration
DHCP Snooping configuration secures your switch by blocking rogue DHCP servers and validating only trusted sources. In this lesson, you’ll learn how to enable the feature, define trusted ports, apply rate limiting, and verify bindings for a safer network.