CDP (Cisco Discovery Protocol) is a Layer 2 protocol developed by Cisco. It helps Cisco devices (like switches and routers) discover directly connected neighbors.
Imagine you're connected via console cable to a router (R1), but you have no idea what other devices are connected.
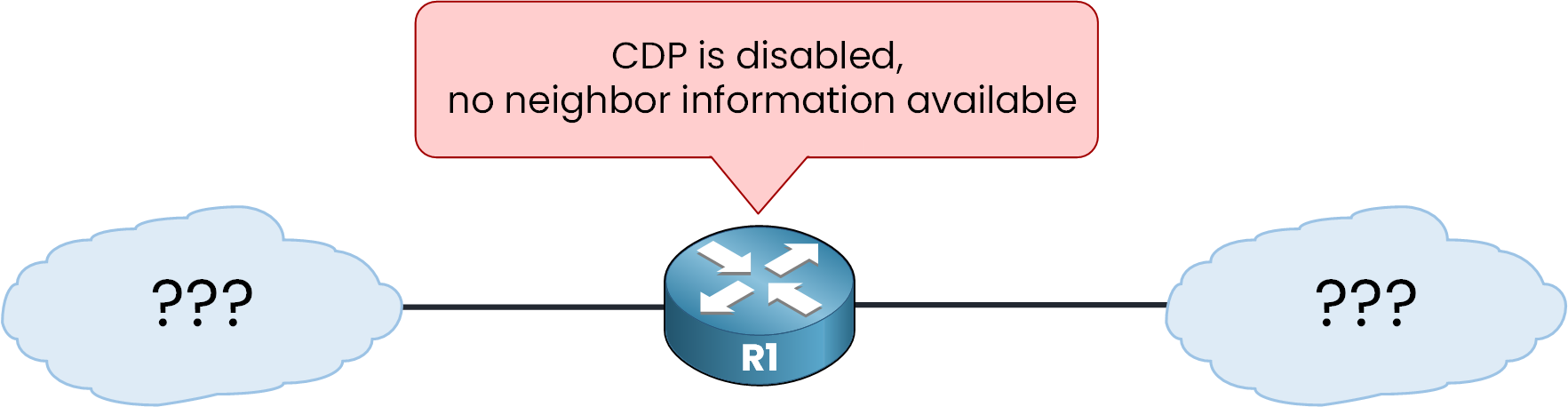
Figure 1 – CDP disabled: R1 cannot see any directly connected neighbors
If CDP is disabled, R1 stays blind it sees no neighbors.
But when CDP is enabled, R1 automatically learns about its directly connected Cisco neighbors such as R2 and R3.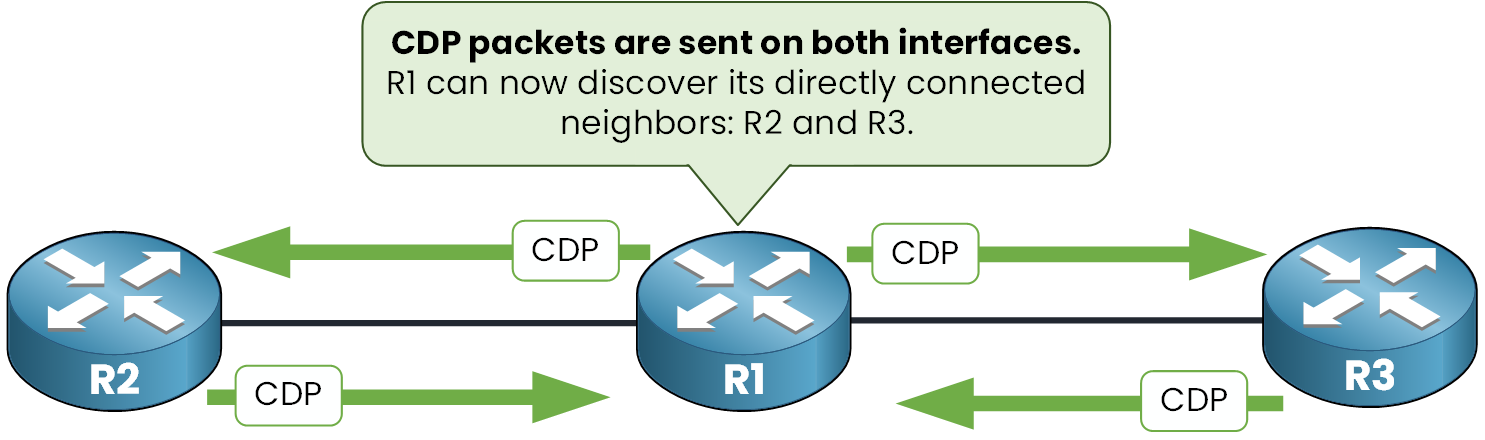
Figure 2 – CDP enabled: neighbors R2 and R3 discovered
CDP is especially useful when you're in an undocumented or unknown network. With just one command, you can start discovering connected devices and mapping the topology.
Answer the question below
CDP works in a simple and efficient way:
Cisco devices exchange messages on active interfaces to discover their directly connected Cisco neighbors.CDP Advertisements
Each Cisco device periodically sends CDP messages on its active interfaces. These messages contain:
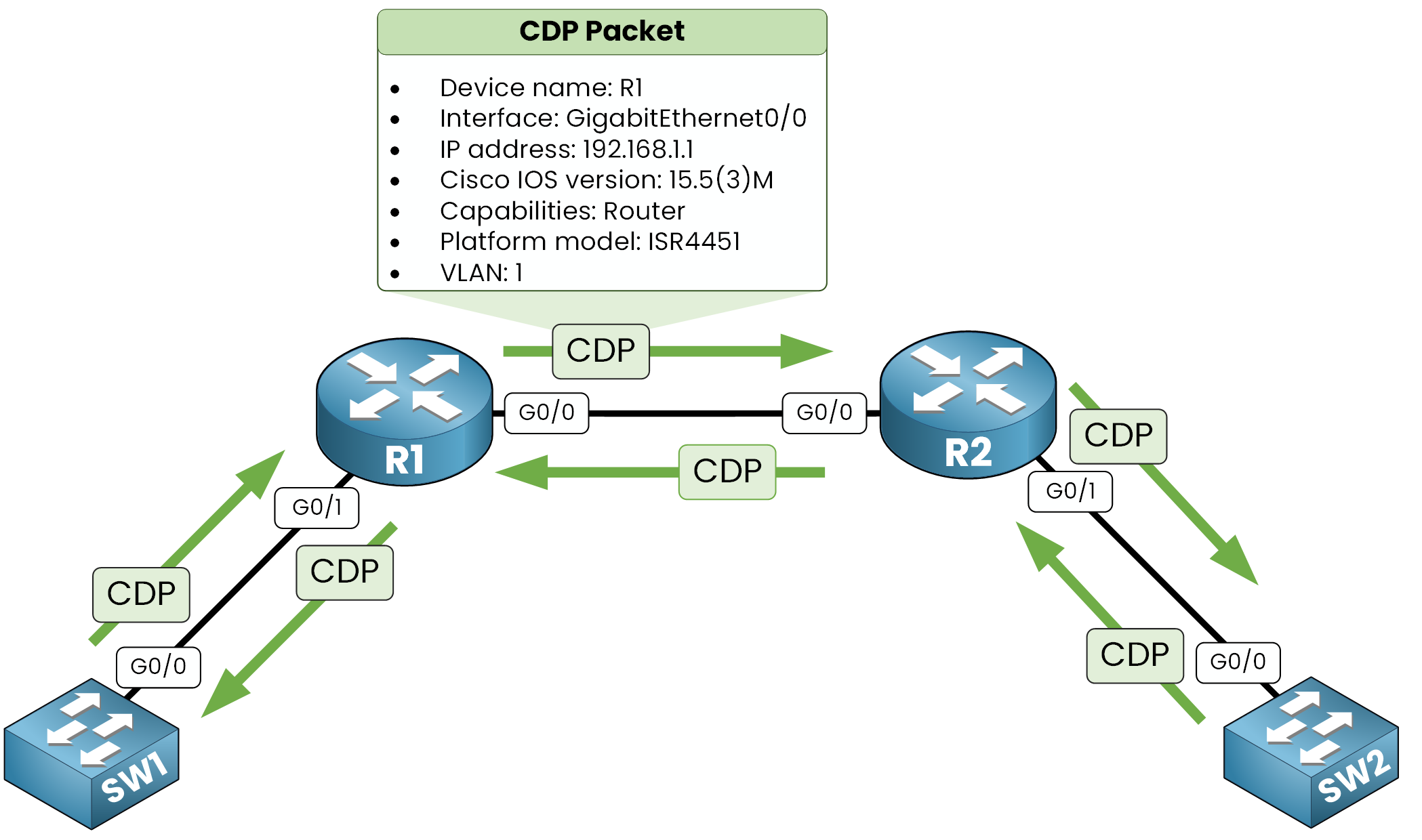
Figure 3 – CDP advertises neighbor info on all active interfaces
Device ID: Hostname of the neighbor (example,
R1)Local Interface: Port used on your device (example,
Gig0/0)Port ID: Port used by the neighbor (example,
Gig0/1)Platform: Neighbor’s model (example,
ISR4451)Capabilities: Whether it's a router, switch, IP phone, etc.
IP Address: Management IP (if configured)
These messages are sent as Layer 2 frames and don’t require IP addressing. The information is stored locally in CDP Table.
CDP Table
Each Cisco device builds and maintains a CDP table of its discovered neighbors.
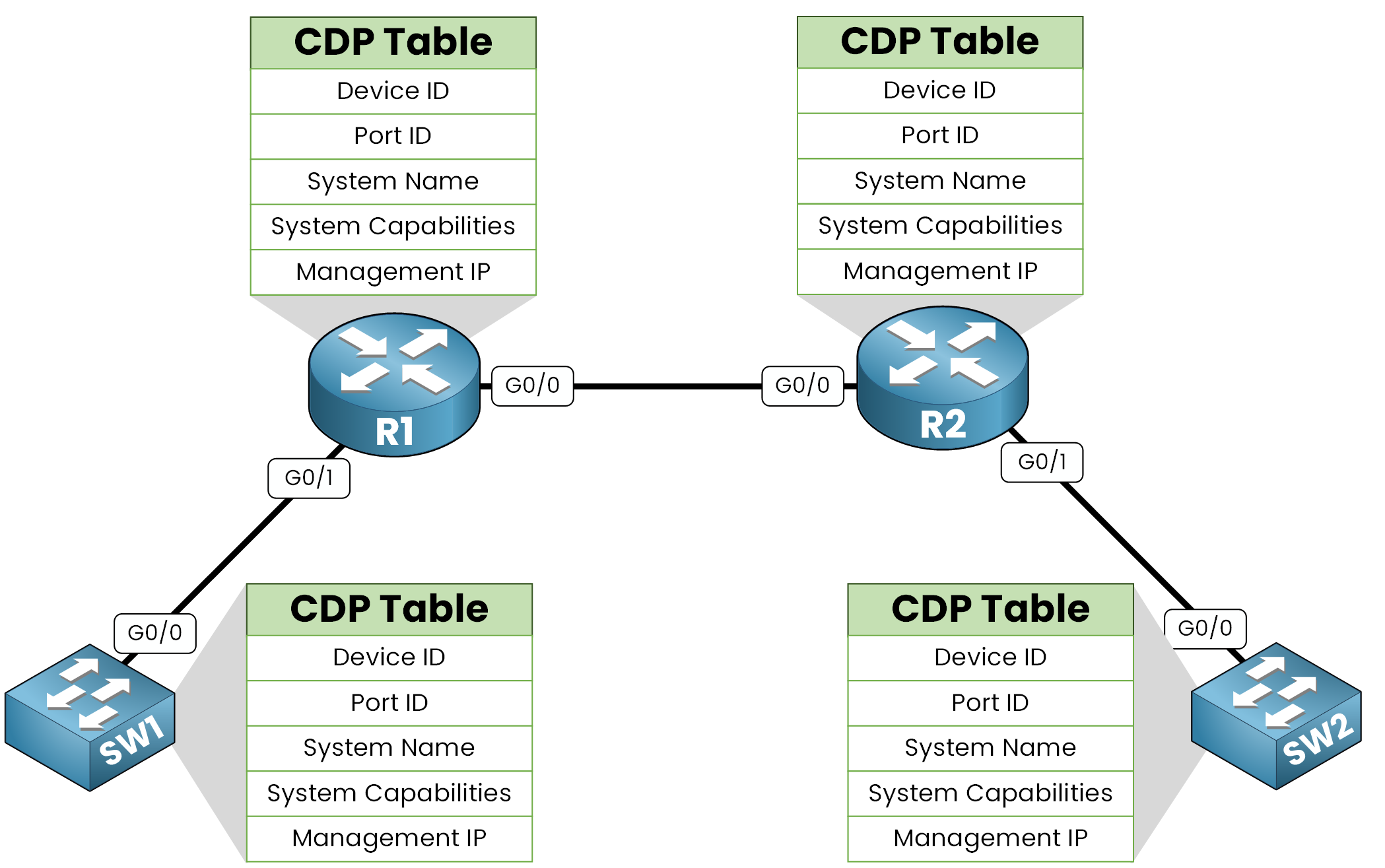
Figure 4 – CDP tables list details of directly connected neighbors
You can view it by using the
show cdp neighborscommand on a device like SW1:SW1# show cdp neighbors Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone, D - Remote, C - CVTA, M - Two-port Mac Relay Device ID Local Intrfce Holdtme Capability Platform Port ID R1 Gig 0/0 157 R B Gig 0/1This tells us:
SW1 is connected to R1
Using local port Gig0/0
R1 uses port Gig0/1
R1 is a Router/Bridge
Its platform is ISR4451
On SW1, we clearly see that it has a directly connected Cisco neighbor which is R1.
Answer the question below
Which command displays directly connected Cisco neighbors?
CDP uses two timers to manage how long neighbor information is stored and how often it is refreshed:
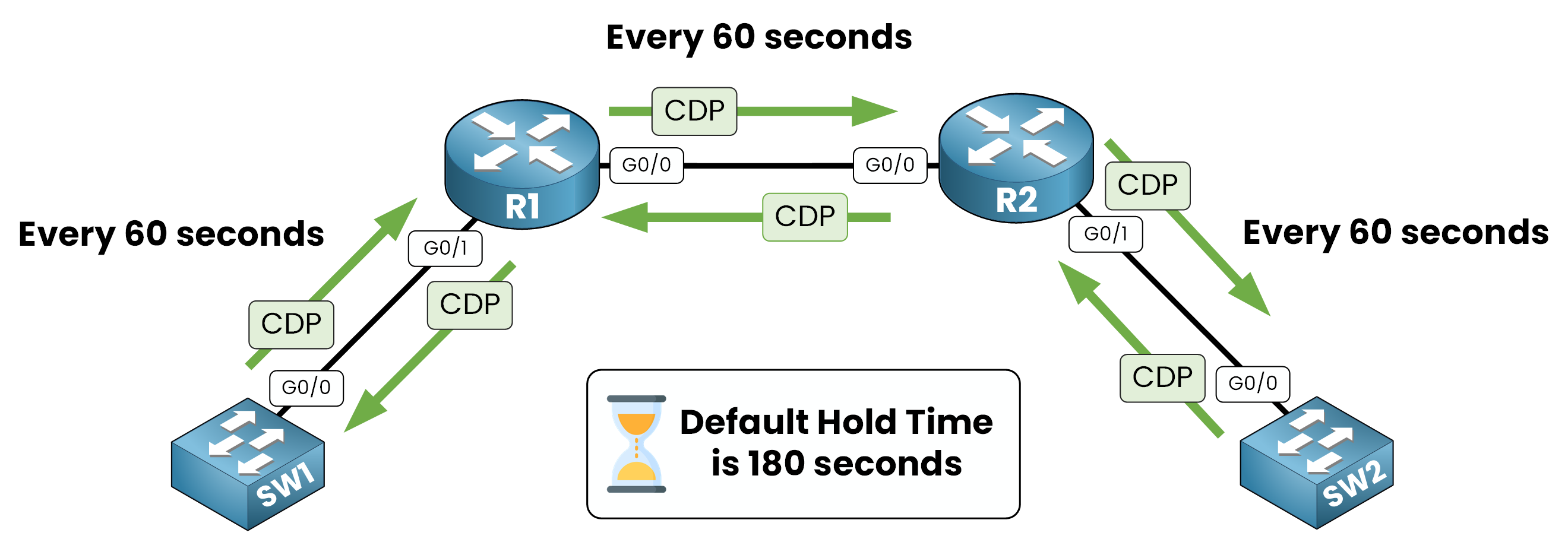
Figure 5 – CDP sends updates every 60s; hold time is 180s
1. Update Timer
By default, CDP sends advertisements every 60 seconds on all active interfaces.
This regular interval ensures devices consistently share their presence with directly connected neighbors.2. Hold Timer
Each device applies a hold time of 180 seconds to neighbor entries.
If no new CDP advertisement is received before this timer expires, the neighbor is removed from the CDP table.
This helps prevent outdated or incorrect data from remaining in the network.Both timers can be adjusted if needed.
Answer the question below
What is the default CDP hold time in seconds?
Enable CDP Globally
CDP is enabled by default on Cisco devices.
But if, for any reason, it was disabled, you can turn it back on usingcdp runcommand:40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
Cisco Discovery Protocol (CDP)
Cisco Discovery Protocol (CDP) allows Cisco devices to automatically learn about their directly connected neighbors without relying on IP addressing. In this lesson, you will see how to configure CDP, verify neighbors, and understand both its advantages and security risks.