DHCP Snooping Cisco is a security feature originally created by Cisco to protect your network from rogue DHCP servers and IP address exhaustion.
In a typical network, DHCP simplifies configuration by automatically assigning IP settings to clients. But this convenience comes with a risk: malicious devices can impersonate DHCP servers and hijack traffic or deny access to other users.
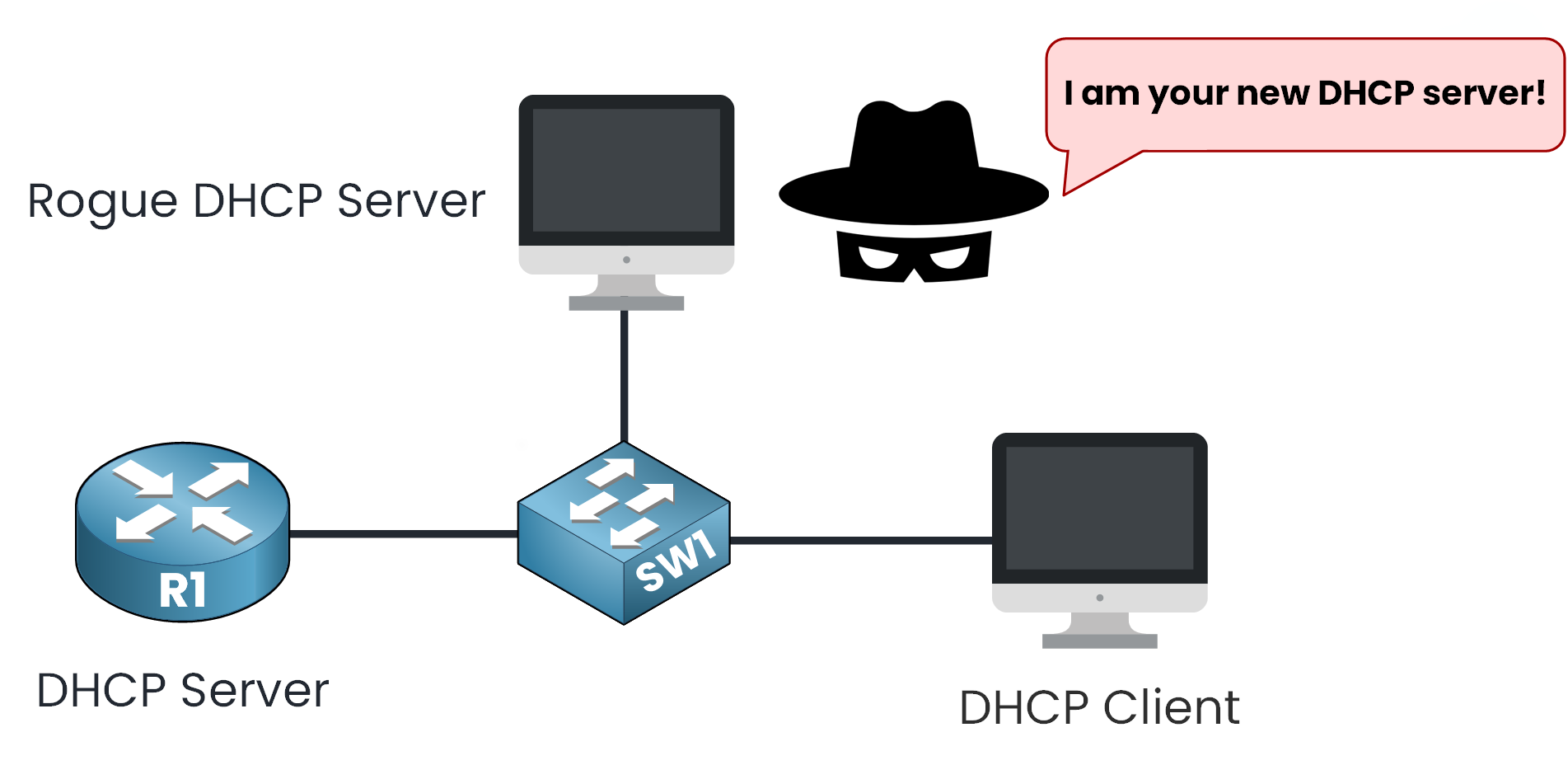
Figure 1 – Rogue DHCP Server Impersonation
This lesson shows you how attackers exploit DHCP, and how DHCP Snooping defends your network by filtering messages, verifying sources, and maintaining trusted zones.
Let’s start by understanding the two main types of DHCP attacks.
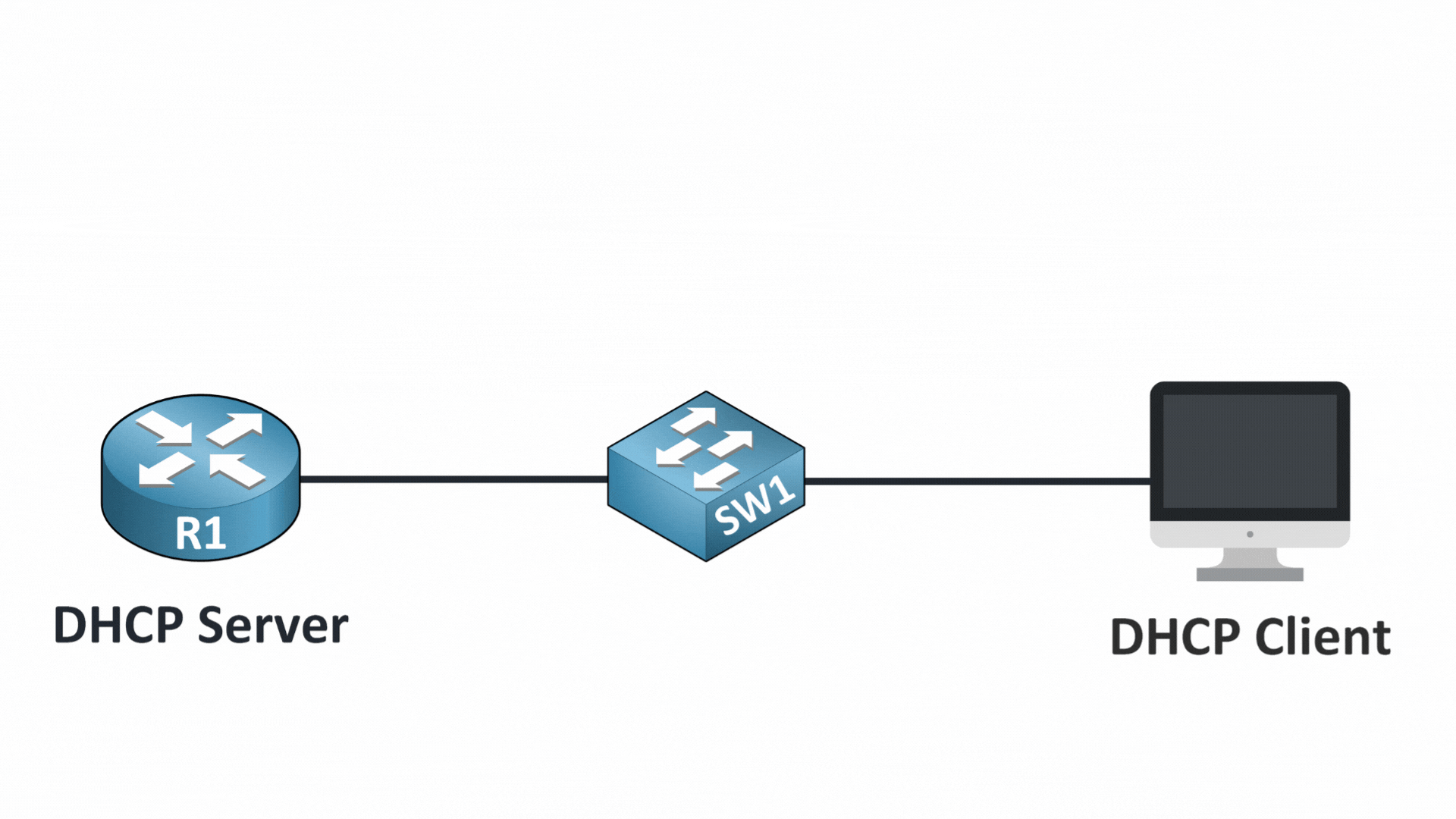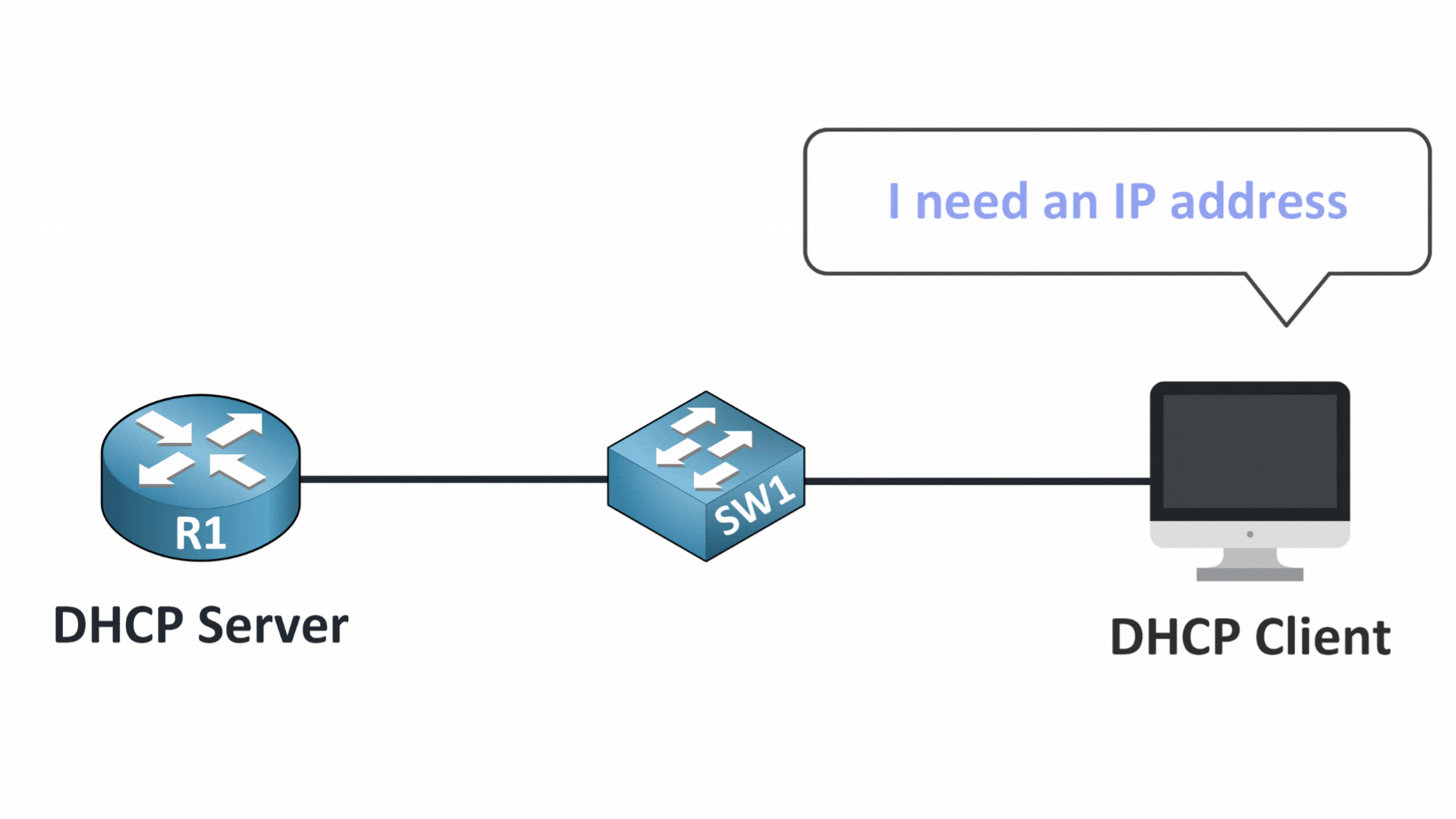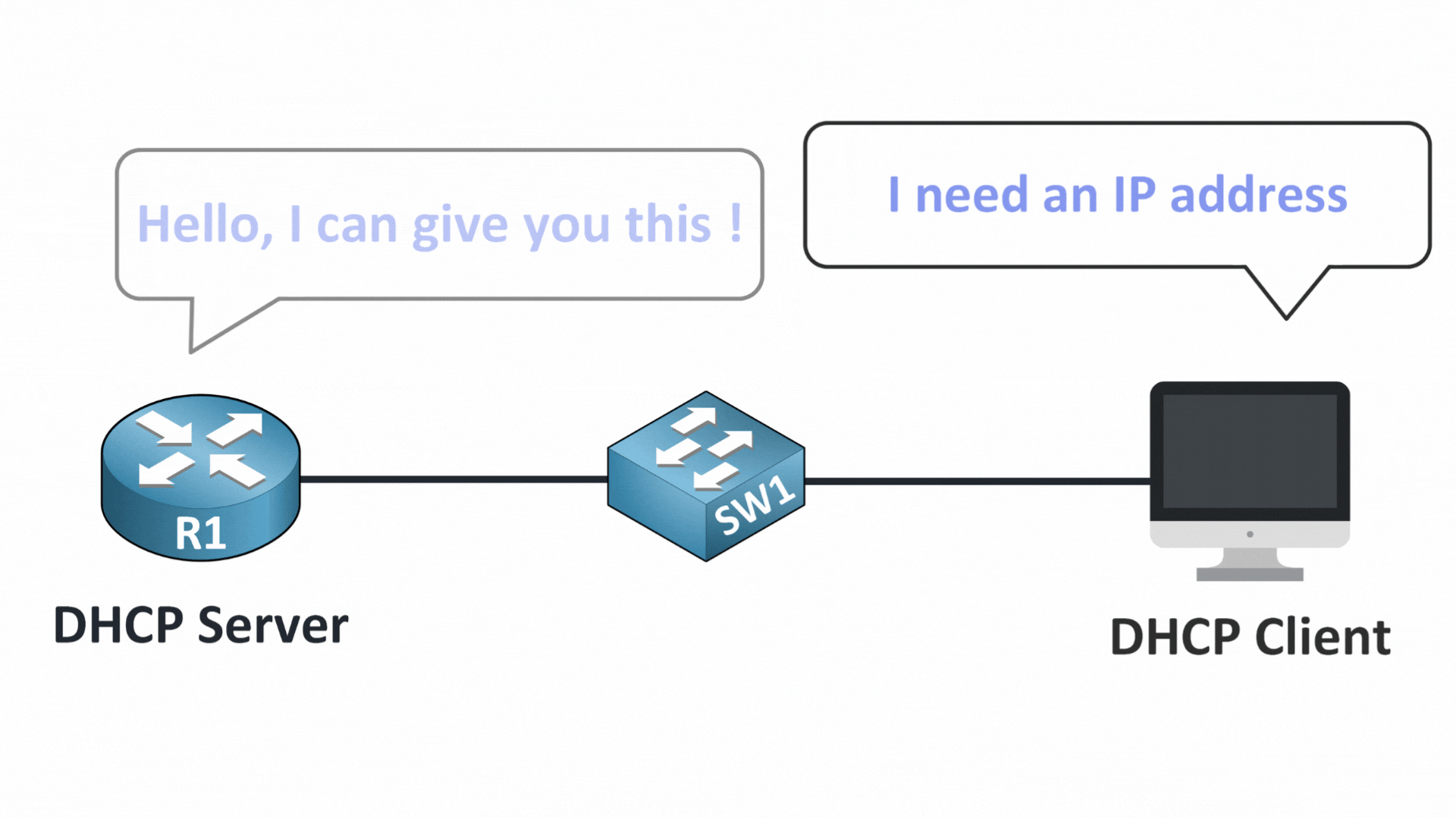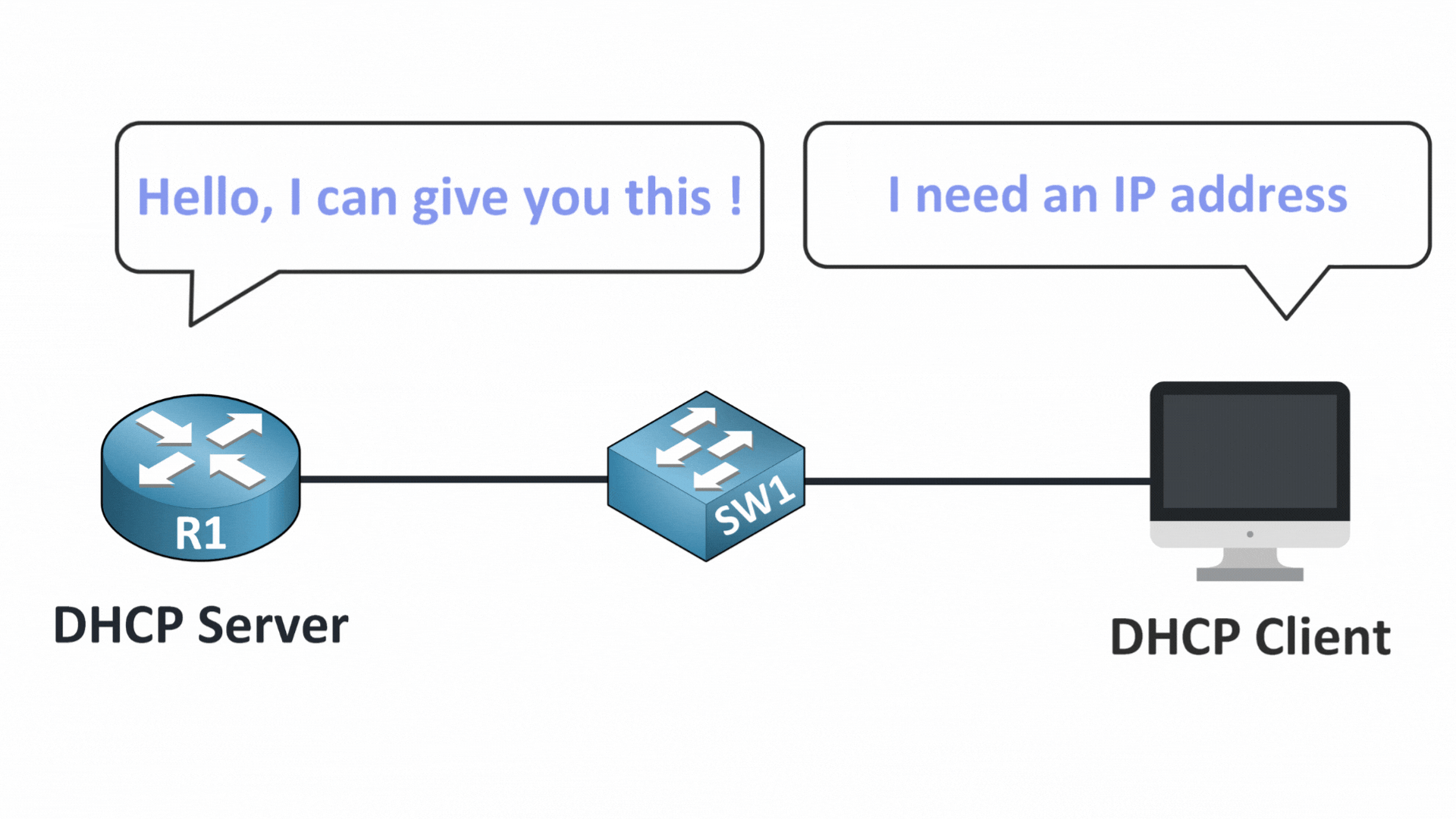
Figure 2 – DHCP Server and Client Communication
You likely already know that DHCP (Dynamic Host Configuration Protocol) plays a key role in your network.
It automatically assigns devices essential configuration like:
IP addresses,
Subnet masks,
Default gateways,
DNS server
But let’s imagine a scenario. What if a malicious device pretends to be your network’s DHCP server?
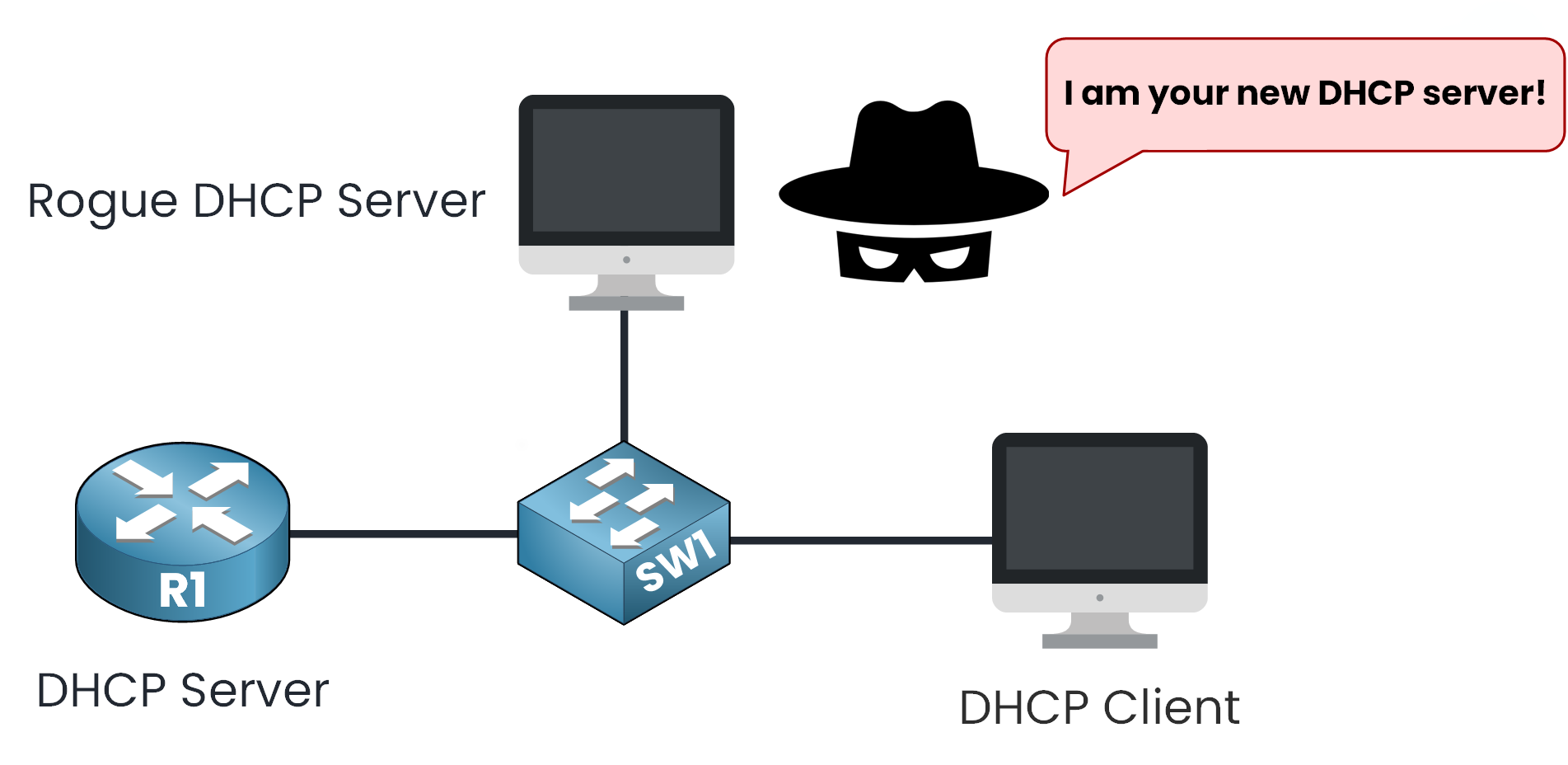
Figure 3 – Rogue DHCP Server Threat Scenario
Two major threats can occur in this situation:
Man-in-the-Middle (MITM) attacks (intercepting your sensitive data) or
DHCP starvation (denying legitimate devices access to the network)
Sounds alarming, right? Don’t worry! Before we explain how DHCP Snooping solves these issues, first we’ll break down DHCP attacks: the Man-in-the-Middle attack and DHCP Starvation.
This will give you the context you need to see how DHCP Snooping protects your network.
Let’s dive into the details together!
Answer the question below
Step 1 – DHCP Discover
When a device connects to the network, it starts by sending a DHCP DISCOVER message.
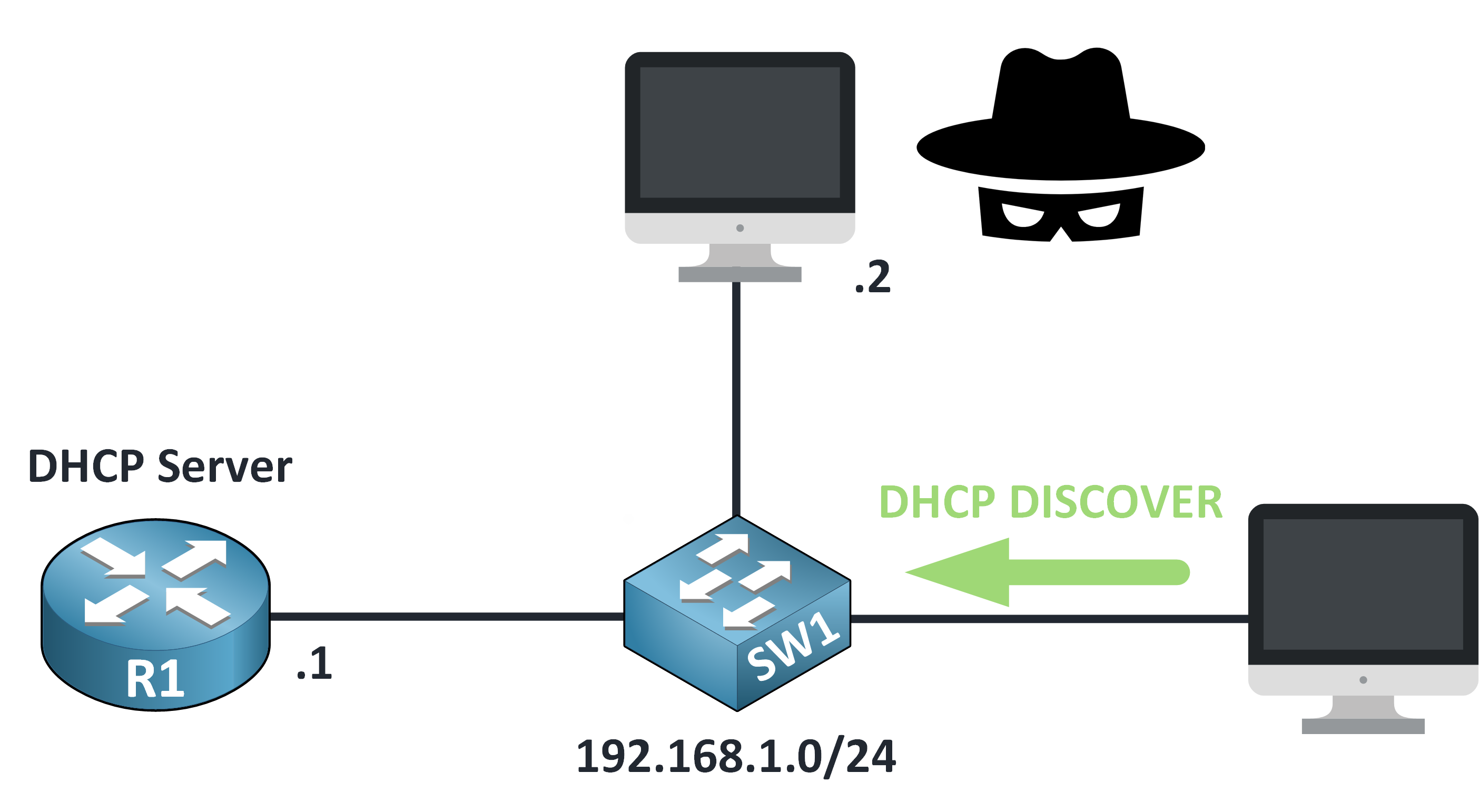
Figure 4 – DHCP Discover in a Man-in-the-Middle Attack
It’s like asking: “Is there a DHCP server out there that can give me an IP address?”
At this point, everything is normal, the device simply broadcasts its request to the entire local network.
Step 2 – Rogue Server Joins In
The DISCOVER message reaches both the legitimate DHCP server and a rogue device pretending to be one.
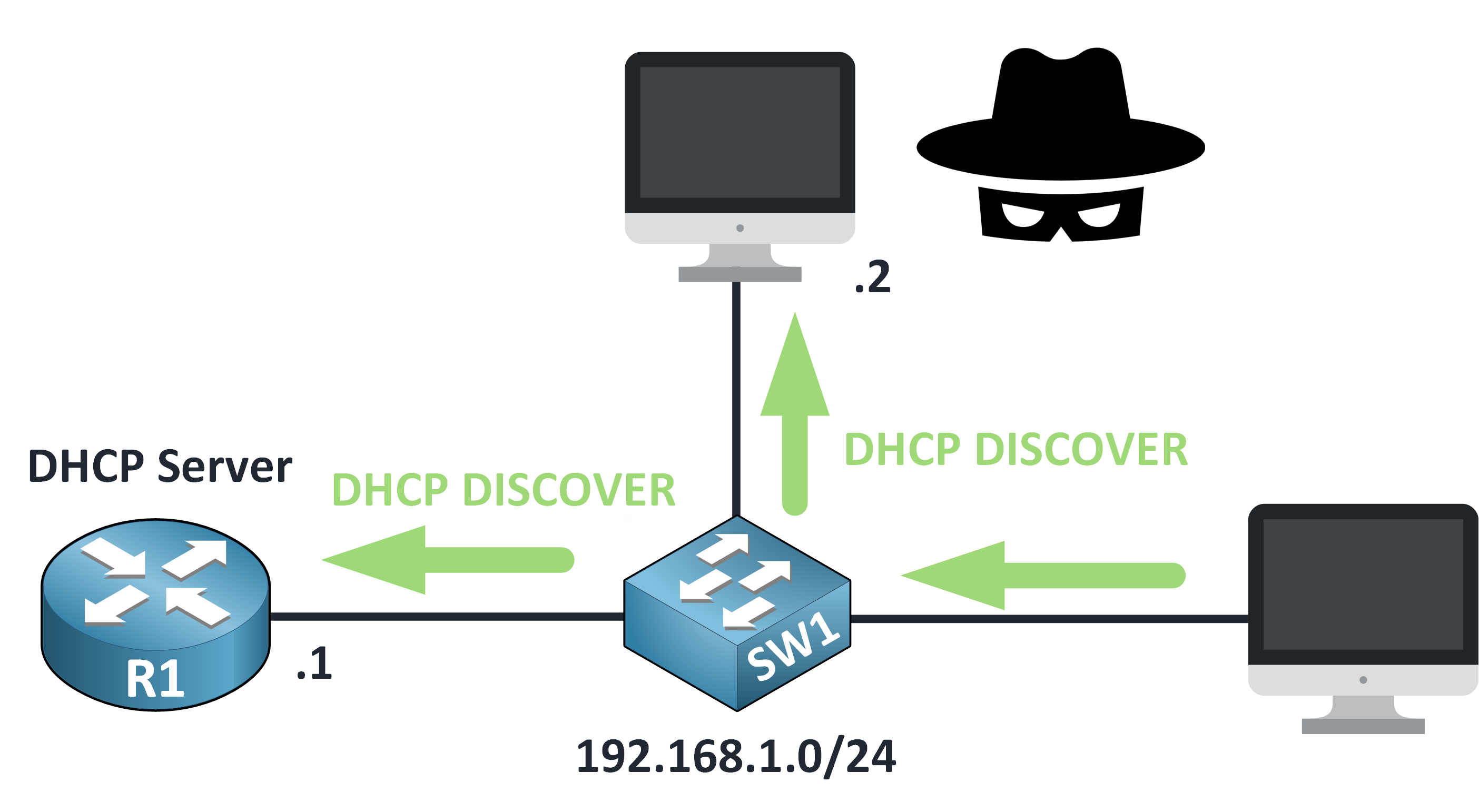
Figure 5 – DHCP Discover Reaches All Devices
That rogue server quickly responds with a fake DHCP OFFER.
Step 3 – First Come, First Served
Both servers reply with a DHCP OFFER.
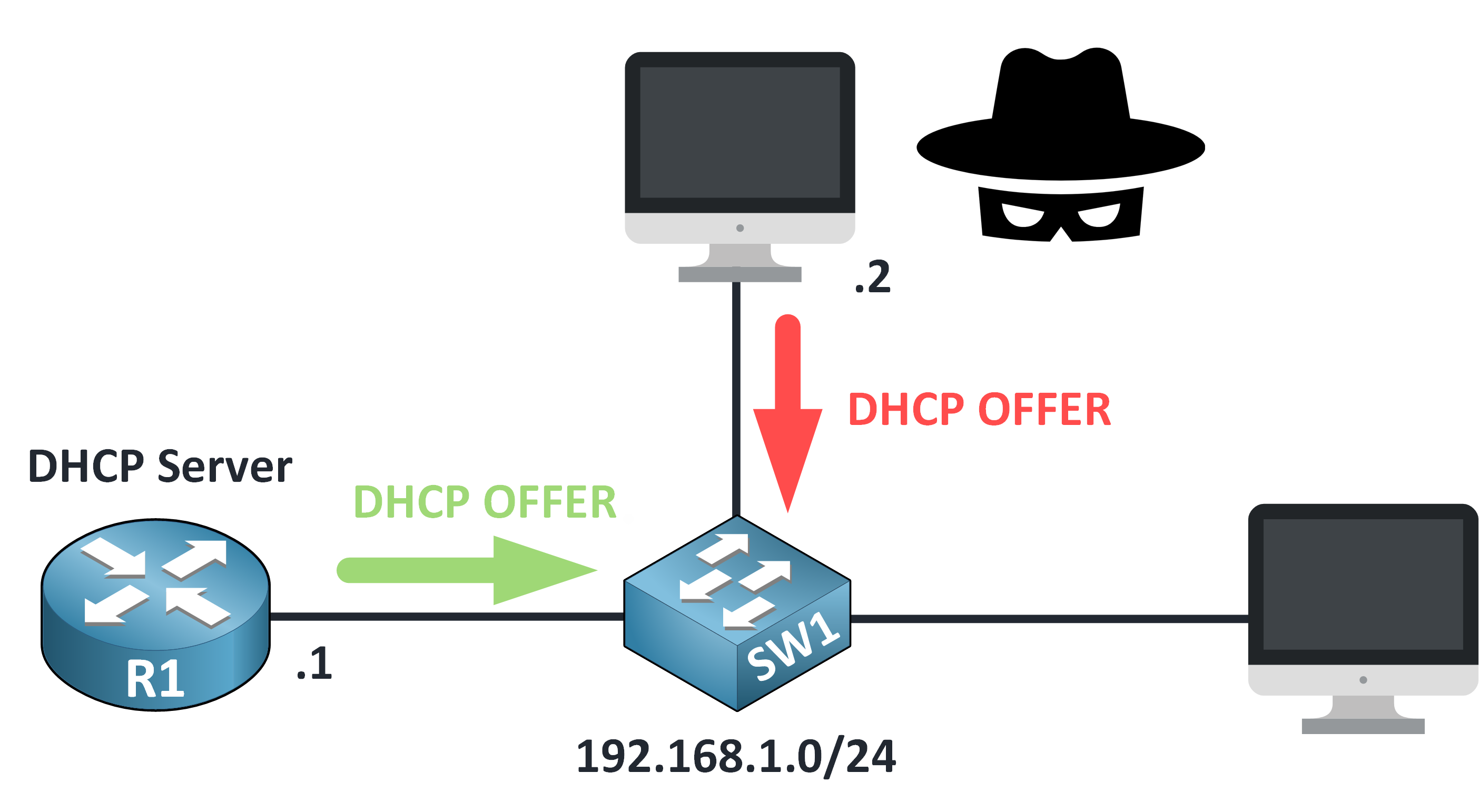
Figure 6 – Competing DHCP Offers: Legitimate vs Rogue
The client will usually accept whichever offer arrives first and that’s often the rogue one.
Step 4 – Malicious Offer Accepted
The client receives the rogue DHCP OFFER first and accepts it.
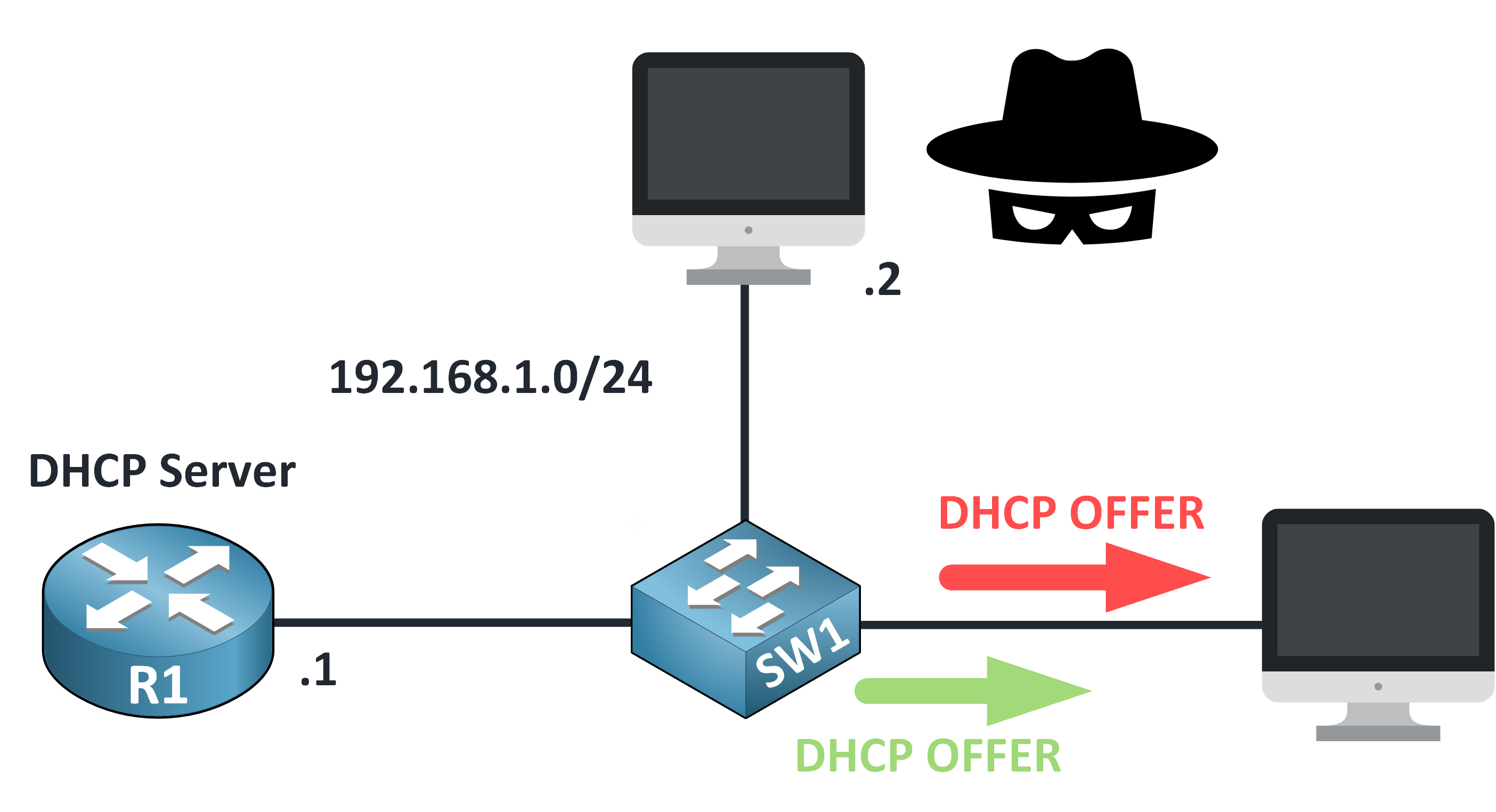
Figure 7 – Rogue DHCP Offer Accepted by Client
Step 5 – DHCP Request Sent
The device confirms its choice by sending a DHCP REQUEST to the rogue server.
It unknowingly agrees to use malicious network settings.
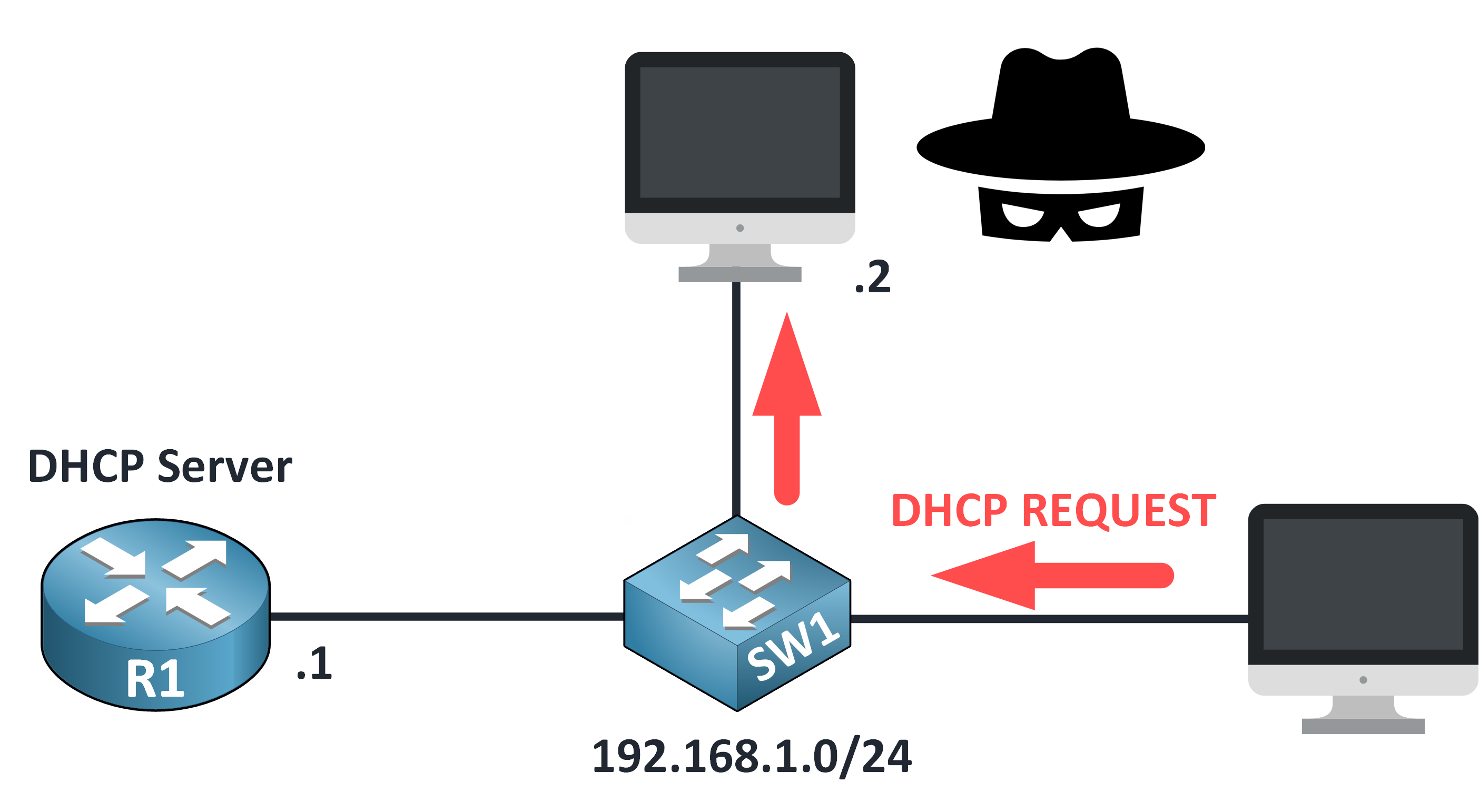
Figure 8 – DHCP Request Sent to Rogue Server
Unfortunately, the device it has no way of knowing that it just accepted settings from a malicious server.
At this point, the rogue server has successfully tricked your device with a malicious IP configuration.40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, simply create your free account.
Access all CCNA lessons
Practice with hands-on labs
Train with Practice exams and Quizzes
Progress tracking in your dashboard
Made by network engineers - CCNP certified
learners globally
DHCP Snooping
DHCP Snooping Cisco is a security feature that stops rogue DHCP activity and protects address allocation in the network. This lesson explains its operation and why it is essential for reliable connectivity.