How ACLs Work
Course Contents
1. What is ACL and How It Works in Networking
When managing a network, one of your key responsibilities is deciding what traffic should be allowed and what should be blocked. That’s exactly what Access Control Lists (ACLs) are designed for.
An ACL is a set of rules that filters traffic based on specific conditions. You can apply these rules on Cisco routers or Layer 3 switches to permit or deny packets.
There are two main types of ACLs:

- Standard ACLs operate at Layer 3 (Network Layer) and filter traffic based only on the source IP address.
- Extended ACLs operate at both Layer 3 and Layer 4 (Network and Transport Layers), allowing filtering based on source and destination IP, protocols, and even port numbers.
Real-World Example
Let’s say you want to allow the Legal department (192.168.1.0/24) to access a server, but block the HR department (192.168.2.0/24).

Here’s how a basic Standard ACL would look:
R1(config)# ip access-list standard 10 R1(config-std-nacl)# permit 192.168.1.0 0.0.0.255 R1(config-std-nacl)# deny 192.168.2.0 0.0.0.255
What’s happening here?
- 10 is the ACL ID number.
- The Legal network is allowed to pass.
- The HR network is explicitly denied.
This is how you start applying control over who can access what in your network.
2. Access Control Entry (ACE)
Each rule in an ACL is called an Access Control Entry (ACE). Think of an ACL as a list and each rule in that list is an individual ACE.
Let’s take the example from earlier:
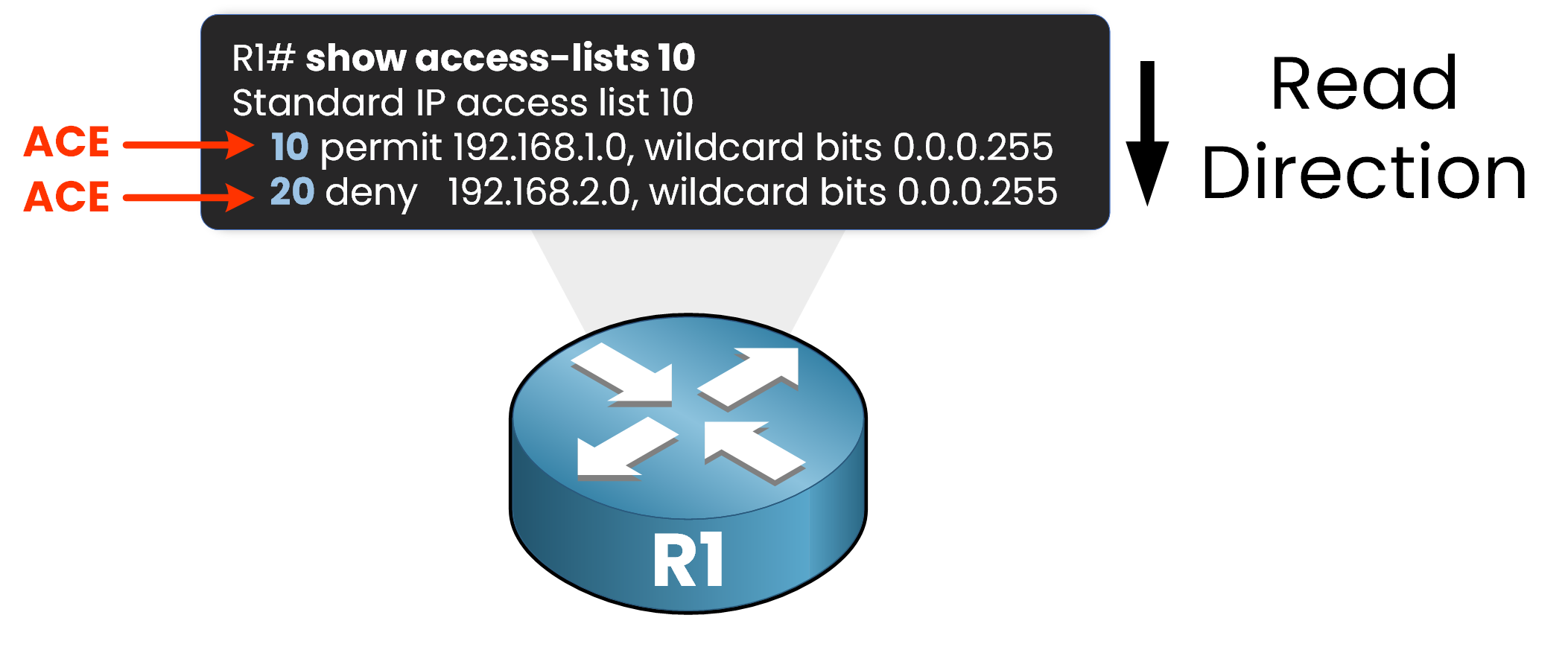
In this access list, we have two ACEs:
- ACE 10: Permits traffic from the 192.168.1.0/24 network.
- ACE 20: Denies traffic from the 192.168.2.0/24 network.
What About That Mask?
You may have noticed something strange in the ACE syntax, the mask doesn’t look like a typical subnet mask…
That’s because ACLs don’t use subnet masks. They use wildcard masks.
What Is a Wildcard Mask?
A wildcard mask works as the inverse of a subnet mask.
It tells the router which parts of the IP address must match exactly and which parts can vary.
| Subnet Mask | Wildcard Mask | Matches |
|---|---|---|
| 255.255.255.0 | 0.0.0.255 | All IPs in 192.168.1.0/24 |
| 255.255.255.255 | 0.0.0.0 | One specific IP address |
If we look at our example:
permit 192.168.1.0 0.0.0.255
This means: allow traffic from any device in the 192.168.1.0/24 network.
If you want to allow just one specific IP address, like 192.168.1.10, you would use:
permit 192.168.1.10 0.0.0.0
This would match only that address.
Reading Order
ACLs are read from top to bottom.
As soon as a packet matches an ACE, the router stops checking the rest of the list.

In this example, the packet with source IP 192.168.1.1 matches ACE 10, so the router allows it. ACE 20 is never evaluated.
3. Implicit Deny
At the end of every ACL, there’s an implicit deny rule.
This means that if a packet doesn’t match any of the ACEs in the list, it is automatically denied even though you don’t see this rule in the configuration.

Even if no explicit deny is written, the router applies the implicit deny at the end, silently dropping the packet.
This is a critical safety measure that ensures only traffic you explicitly allow is permitted on your network.
Now look at the following case:
A packet comes from the source 192.168.5.0 which isn’t listed in any permit or deny statement.

In this example:
- ACE 10 permits traffic from 192.168.1.0/24
- ACE 20 denies traffic from 192.168.2.0/24
- But 192.168.5.0 doesn’t match either rule
Since no match is found, the packet is automatically denied even if no rule matches.
4. Inbound vs Outbound ACLs
When you configure an ACL, you’ll always need to apply it either inbound or outbound on a router interface.
You might be thinking:
“Okay, but what’s the difference?”
The difference lies in when the router checks the traffic.
Inbound ACLs
If the ACL is applied inbound, the router inspects the traffic as it enters the interface before any routing decision is made.

That means the packet is checked immediately upon arrival at the interface. If it’s denied, it never goes any further.
Outbound ACLs
If the ACL is applied outbound, the router first makes its routing decision, outbound ACL checks traffic after the routing decision.

So the traffic is already accepted by the route and the ACL acts as the last filter before it exits.
5. Conclusion
Let’s recap what is ACL and How It Works :
- An ACL is a list of rules that lets you control which traffic is allowed or denied.
- Each rule is called an Access Control Entry (ACE).
- ACLs are processed from top to bottom, and the router stops at the first match.
- If no rule matches, traffic is denied by the implicit deny at the end.
- ACLs are applied either inbound (when traffic enters an interface) or outbound (when it leaves).
We also saw the two types of ACLs:
- Standard ACLs work at Layer 3 and filter based on source IP address.
- Extended ACLs work at Layer 3 and 4, and can filter based on source and destination IP, protocol, and port.
What’s next?
Now that you understand how ACLs work, the next lessons will guide you through:
You’ll see exactly how to apply them in real Cisco environments.
