When managing a network, you often need more than just blocking traffic by source IP.
That’s where Extended Access Control Lists (ACLs) come in.
An Extended ACL is different from a Standard ACL. It allows you to filter traffic by source IP, destination IP, protocol, and port numbers.
Let’s say you have this topology:
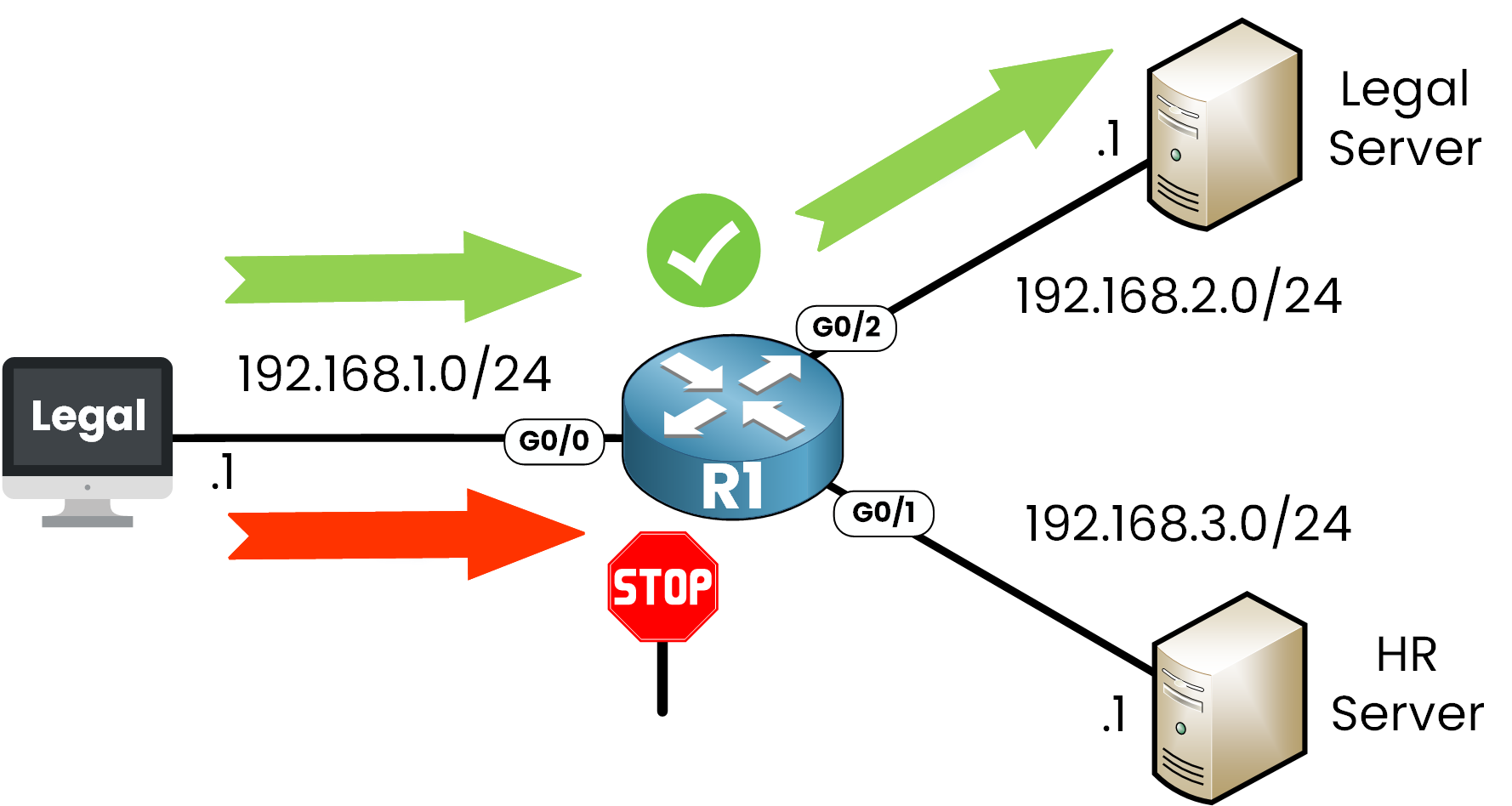
Figure 1 – Extended ACL Use Case
In this example, we want to control access using an Extended ACL:
Allow HTTPS traffic from the Legal PC to a secure Legal Server at 192.168.2.1
Deny all access from the Legal PC to the HR Server at 192.168.3.1
This is a common situation that requires Extended ACLs. Standard ACLs can't filter by protocol or port.
Answer the question below
Now that you know what an Extended ACL is, let’s go through the steps to set one up on a Cisco router.
Step 1 - Enter Global Configuration Mode
Start by entering configuration mode:
R1# configure terminal Enter configuration commands, one per line. End with CTRL/Z. R1(config)#Then, check available ACL types with the ip access-list ? command:
R1(config)# ip access-list ? extended Extended Access List helper Access List acts on helper-address log-update Control access list log updates logging Control access list logging resequence Resequence Access List standard Standard Access ListAs you can see, we have the option to create either a standard or an extended ACL.
We’ll proceed with extended.Step 2 – Create the Extended ACL
Now let's check the available formats for Extended ACLs:
R1(config)# ip access-list extended ? <100-199> Extended IP access-list number <2000-2699> Extended IP access-list number (expanded range) WORD Access-list nameExtended ACLs can be:
Numbered (ranges: 100–199 or 2000–2699)
Named (custom name of your choice)
Let’s create a numbered ACL 101:
In this example, we will create a numbered Extended ACL with the number 101.
R1(config)# ip access-list extended 101 R1(config-ext-nacl)#You are now in Extended ACL configuration mode, ready to define rules.
Step 3 - Permit HTTPS to the Legal Server
We want to allow HTTPS traffic (TCP port 443) from the Legal PC to the Legal Server.
🔹 Choose the Protocol
Start with the permit, then see the protocol options:
R1(config-ext-nacl)# permit ? <0-255> An IP protocol number ahp Authentication Header Protocol eigrp Cisco's EIGRP routing protocol esp Encapsulation Security Payload gre Cisco's GRE tunneling icmp Internet Control Message Protocol igmp Internet Gateway Message Protocol ip Any Internet Protocol ipinip IP in IP tunneling nos KA9Q NOS compatible IP over IP tunneling object-group Service object group ospf OSPF routing protocol pcp Payload Compression Protocol pim Protocol Independent Multicast sctp Stream Control Transmission Protocol tcp Transmission Control Protocol udp User Datagram ProtocolWe want HTTPS, which runs over TCP, so:
R1(config-ext-nacl)# permit tcp ? A.B.C.D Source address any Any source host host A single source host object-group Source network object group🔹 Define the Source IP Address
Let's specify the Legal PC as the source:
R1(config-ext-nacl)# permit tcp host 192.168.1.1 ? A.B.C.D Destination address any Any destination host eq Match only packets on a given port number gt Match only packets with a greater port number host A single destination host lt Match only packets with a lower port number neq Match only packets not on a given port number object-group Destination network object group range Match only packets in the range of port numbers🔹 Define the Destination IP Address
We want to reach the Legal Web Server:
R1(config-ext-nacl)# permit tcp host 192.168.1.1 host 192.168.2.1 ? ack Match on the ACK bit dscp Match packets with given dscp value eq Match only packets on a given port number established Match established connections fin Match on the FIN bit fragments Check non-initial fragments // OUTPUT OMITTED FOR BREVITYTo choose the port number to filter, we use eq, as you can see in the CLI.
🔹 Match the HTTPS Port (443)
We now filter only HTTPS traffic (port 443)
40 % Complete: you’re making great progress
Unlock the rest of this lesson
If you’d like to continue your CCNA journey, create your free account now.
Access all free CCNA lessons
Practice with quizzes and level test
Progress tracking in your dashboard
Made by network engineers - CCNP certified
Create your Free Account1151 learners continued their CCNA journey this month