1. Introduction to DHCP Snooping
DHCP Snooping Cisco is a security feature originally created by Cisco to protect your network from rogue DHCP servers and IP address exhaustion.
In a typical network, DHCP simplifies configuration by automatically assigning IP settings to clients. But this convenience comes with a risk: malicious devices can impersonate DHCP servers and hijack traffic or deny access to other users.
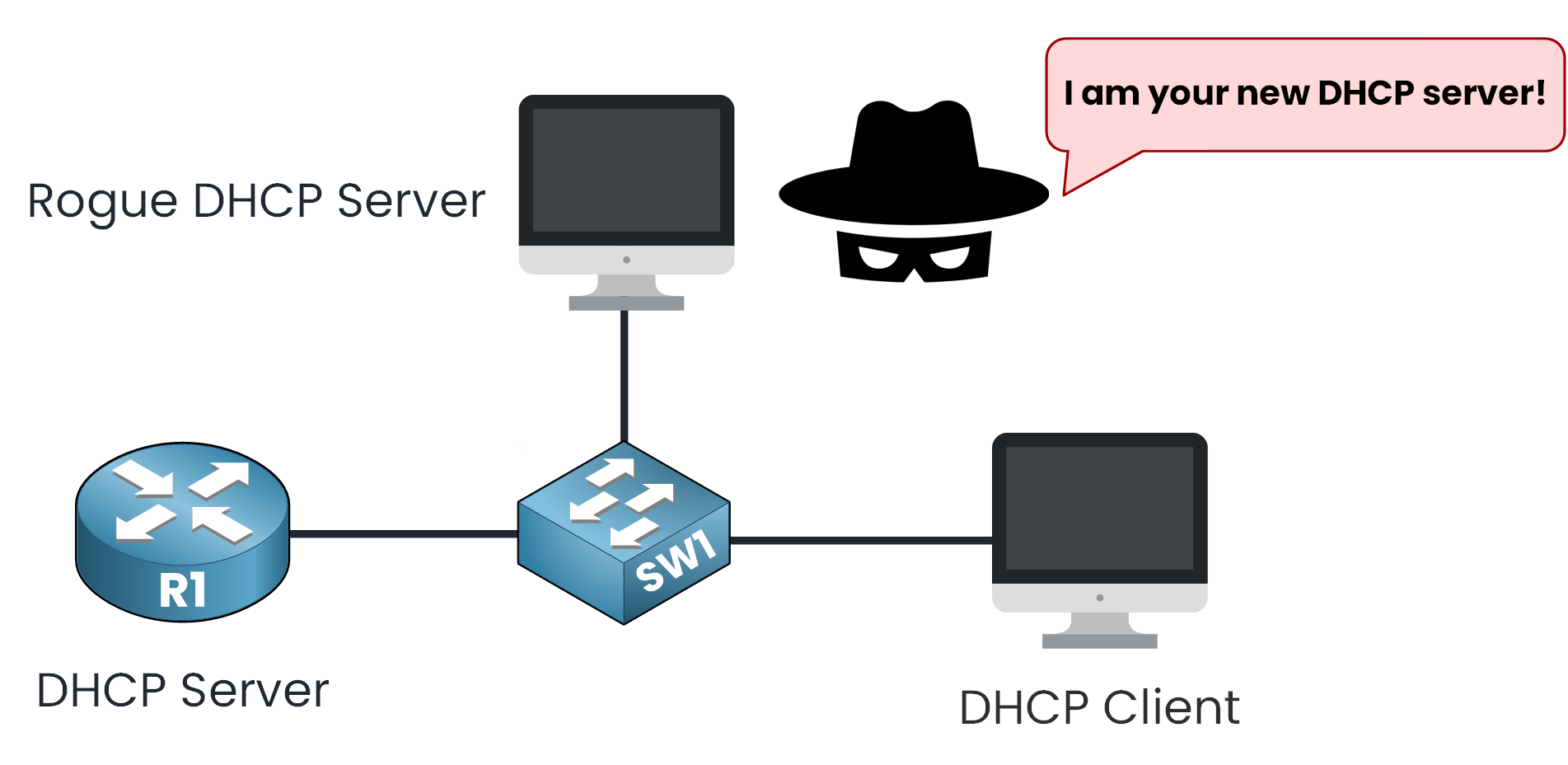
Figure 1 – Rogue DHCP Server Impersonation
This lesson shows you how attackers exploit DHCP, and how DHCP Snooping defends your network by filtering messages, verifying sources, and maintaining trusted zones.
Let’s start by understanding the two main types of DHCP attacks.
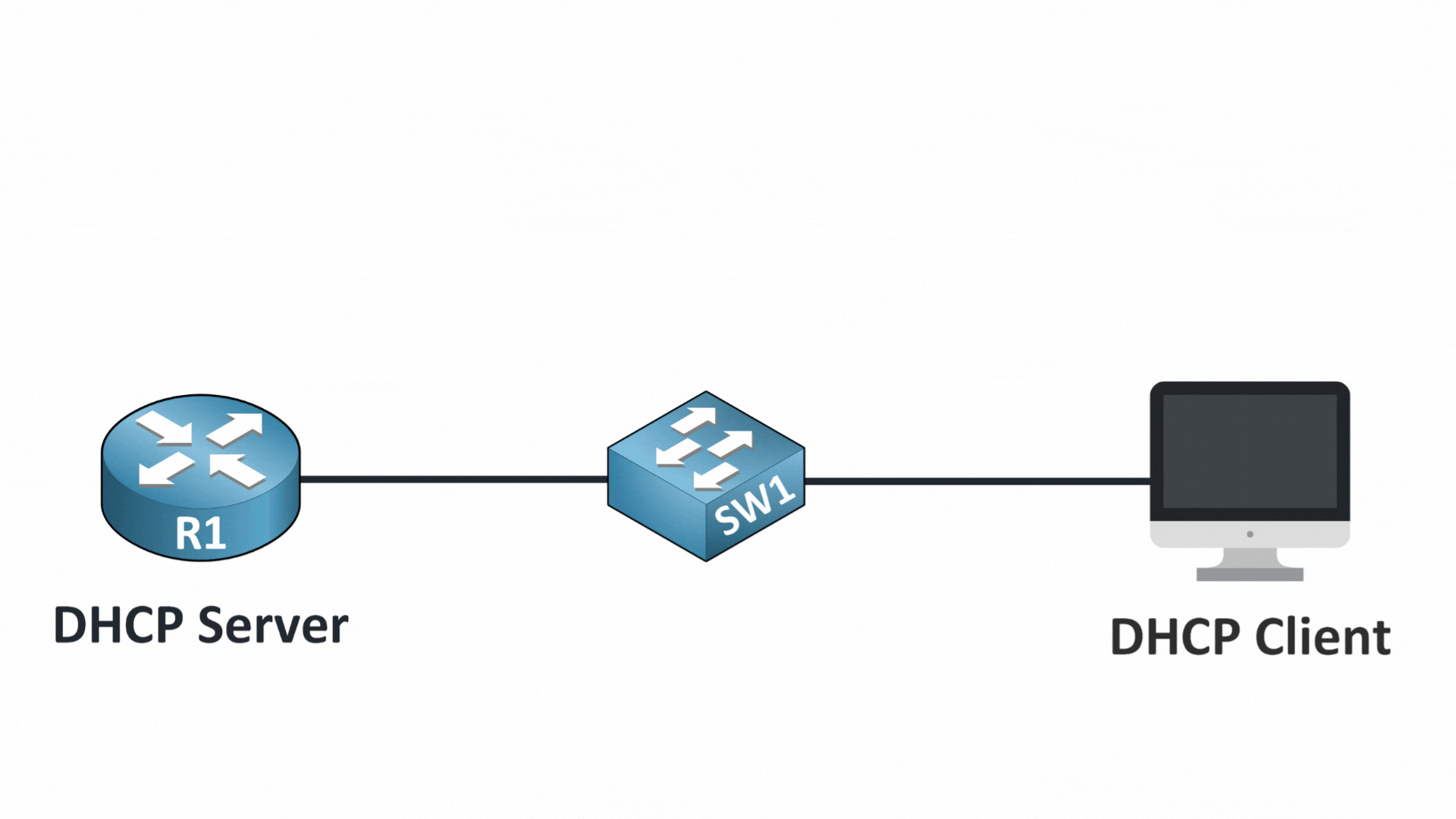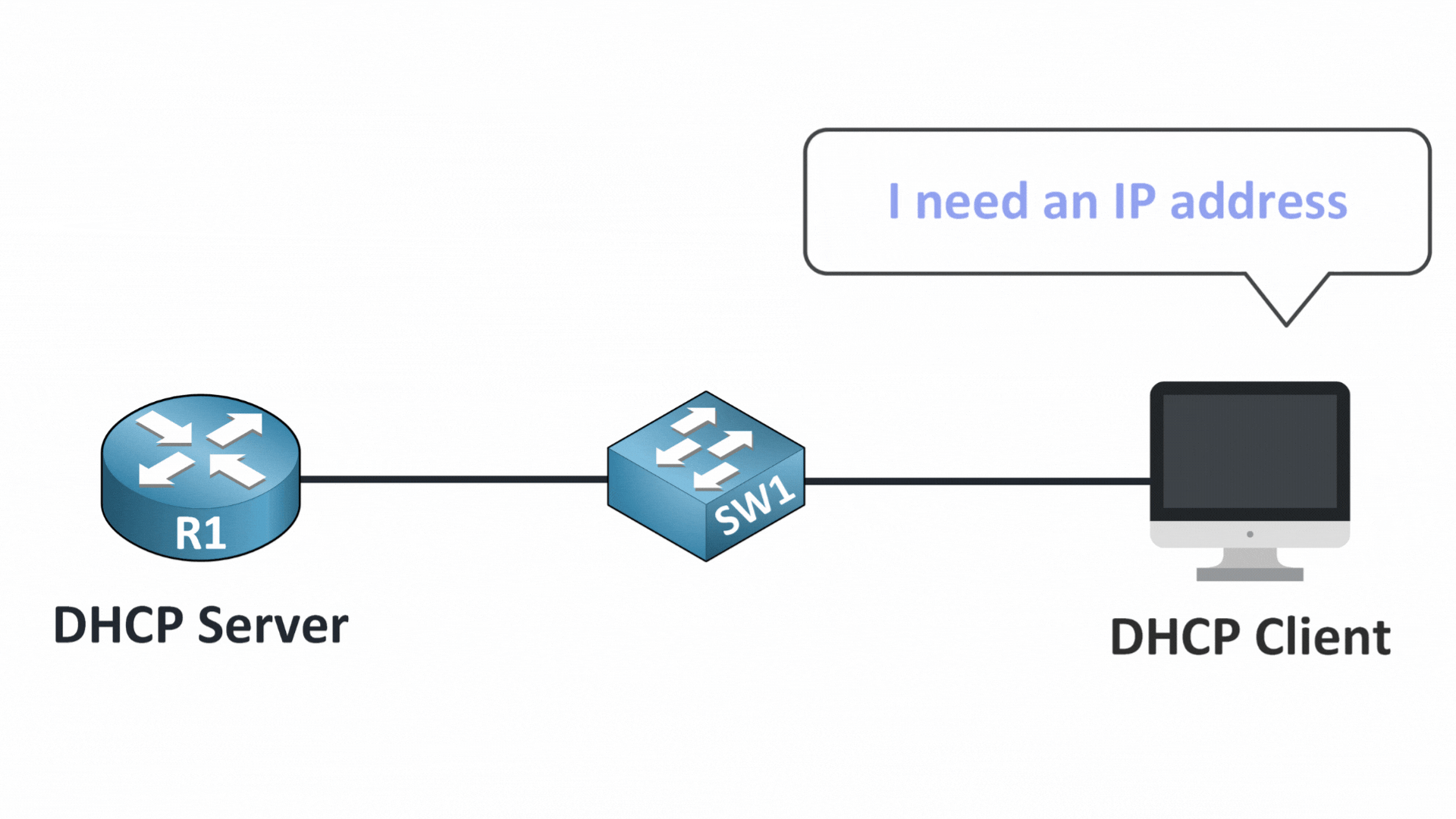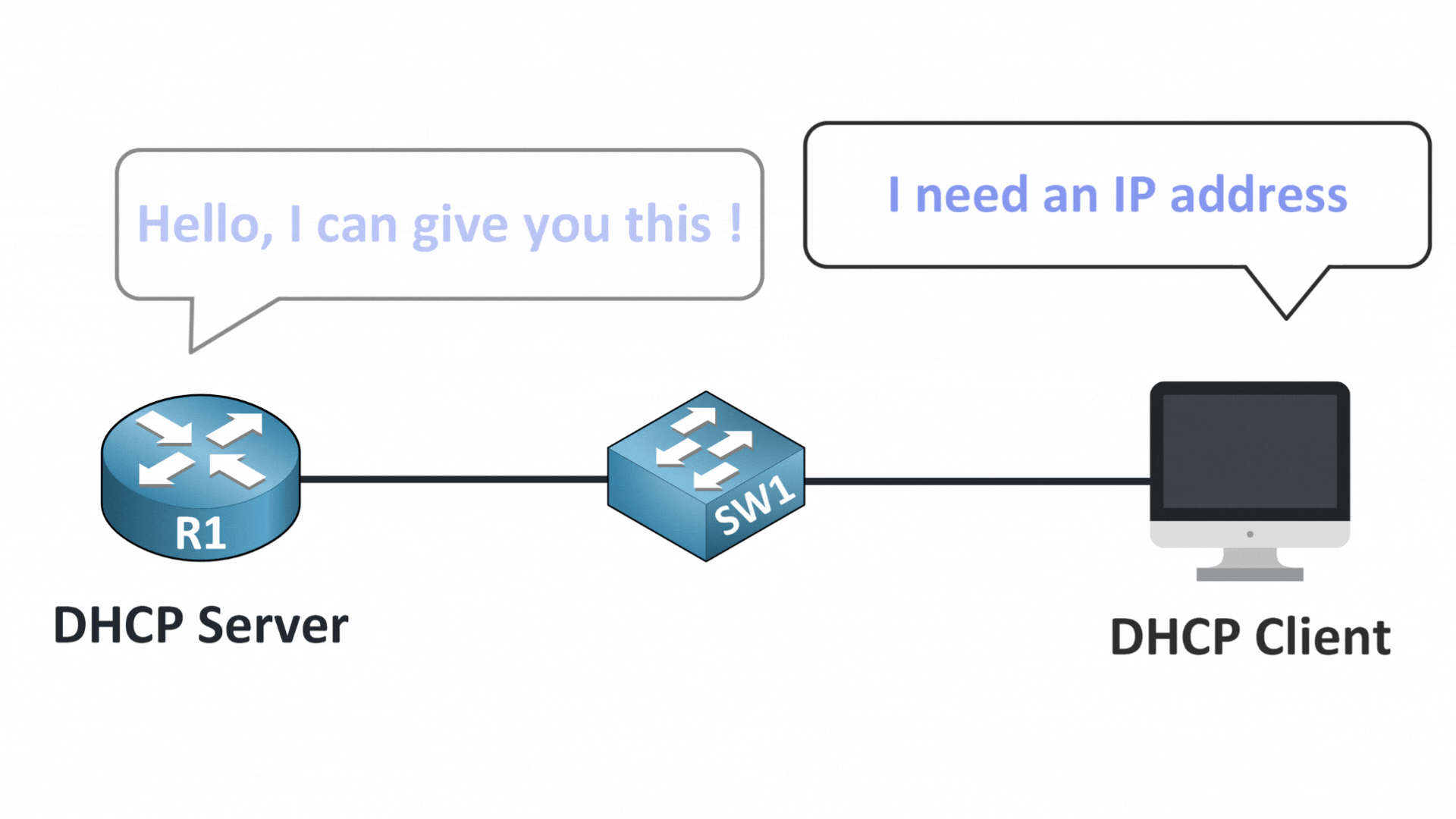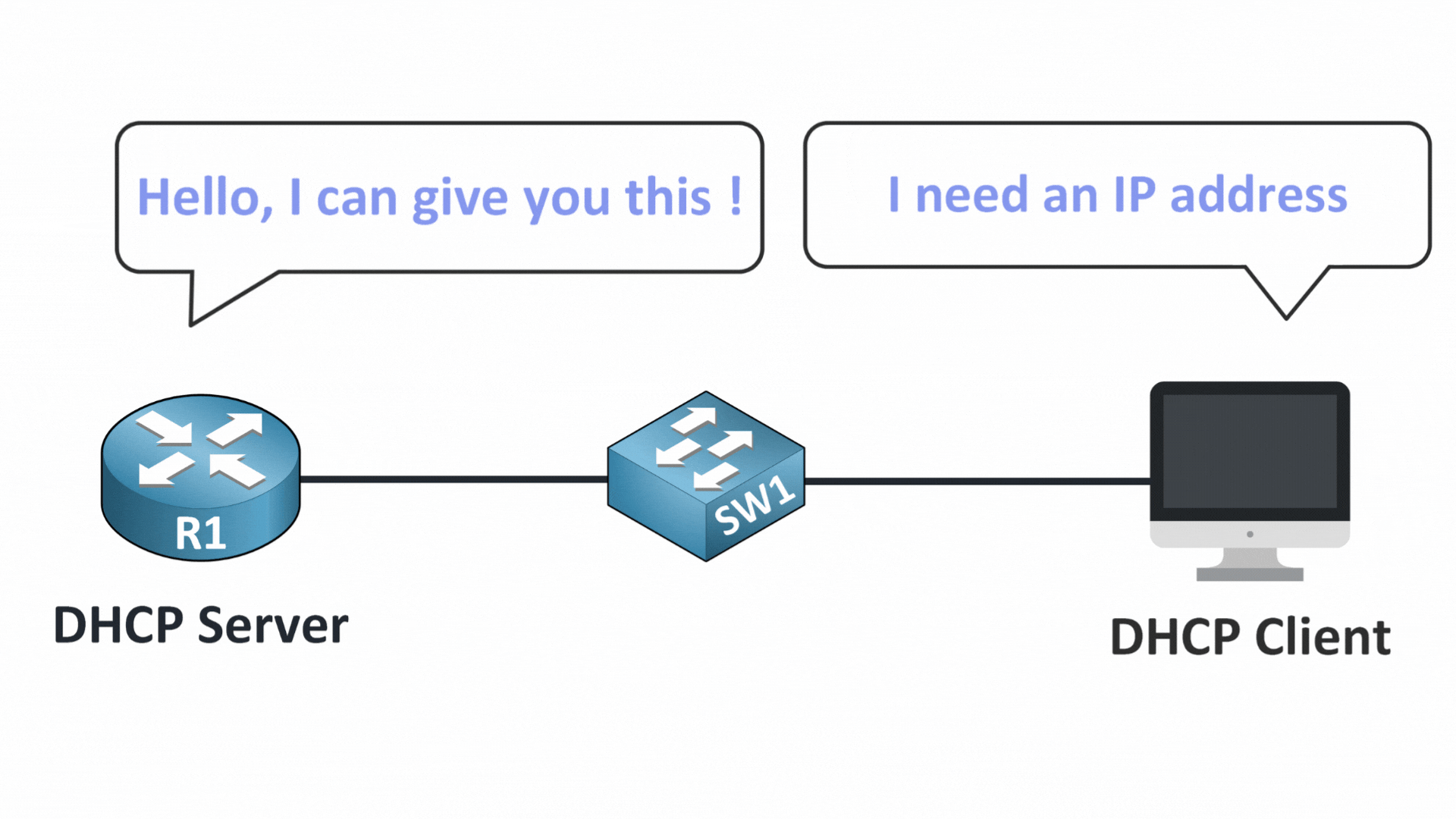
Figure 2 – DHCP Server and Client Communication
You likely already know that DHCP (Dynamic Host Configuration Protocol) plays a key role in your network.
It automatically assigns devices essential configuration like:
IP addresses,
Subnet masks,
Default gateways,
DNS server
But let’s imagine a scenario. What if a malicious device pretends to be your network’s DHCP server?
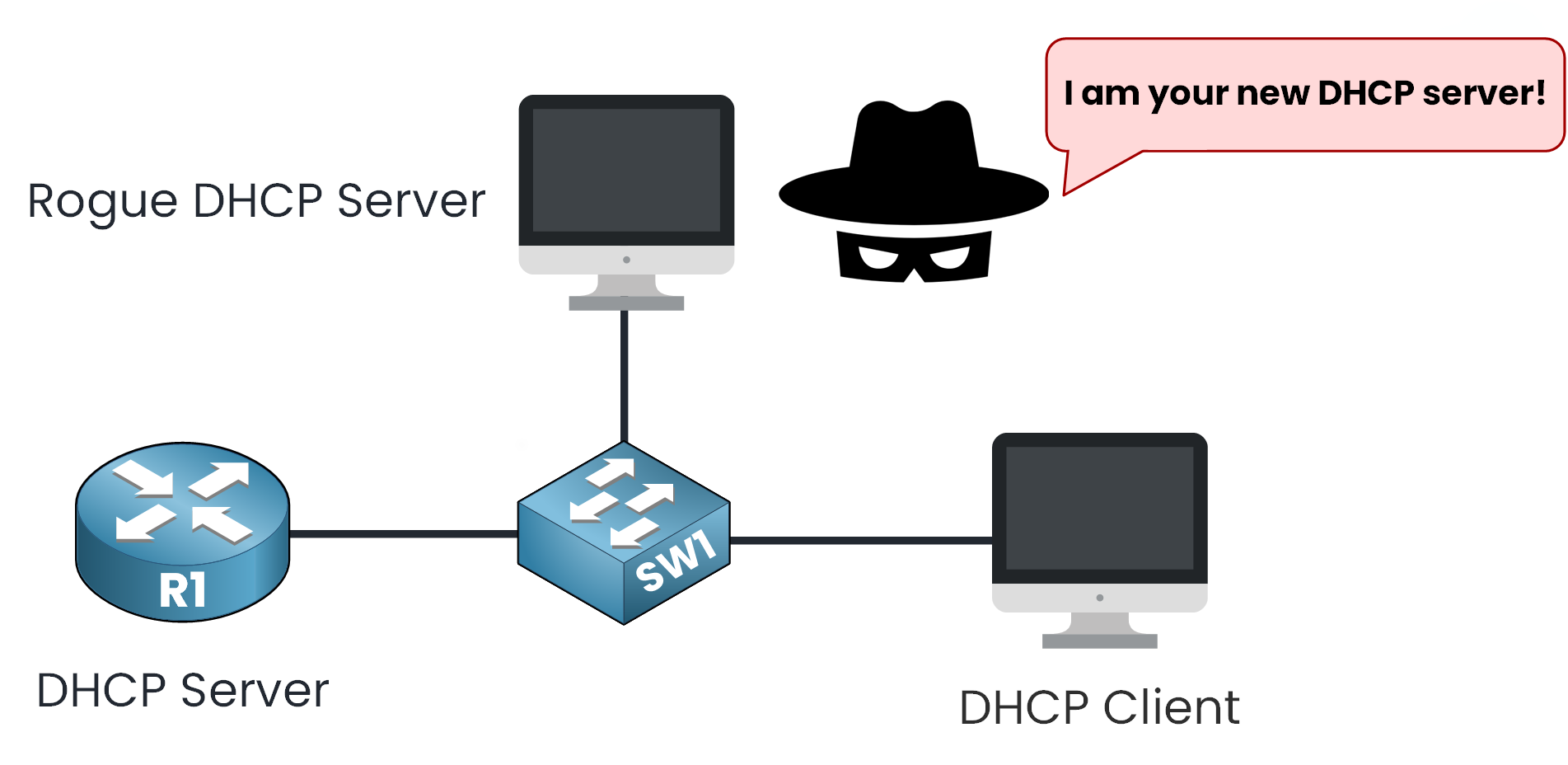
Figure 3 – Rogue DHCP Server Threat Scenario
Two major threats can occur in this situation:
Man-in-the-Middle (MITM) attacks (intercepting your sensitive data) or
DHCP starvation (denying legitimate devices access to the network)
Sounds alarming, right? Don’t worry! Before we explain how DHCP Snooping solves these issues, first we’ll break down DHCP attacks: the Man-in-the-Middle attack and DHCP Starvation.
This will give you the context you need to see how DHCP Snooping protects your network.
Let’s dive into the details together!
2. Understanding DHCP Attacks
Step 1 – DHCP Discover
When a device connects to the network, it starts by sending a DHCP DISCOVER message.
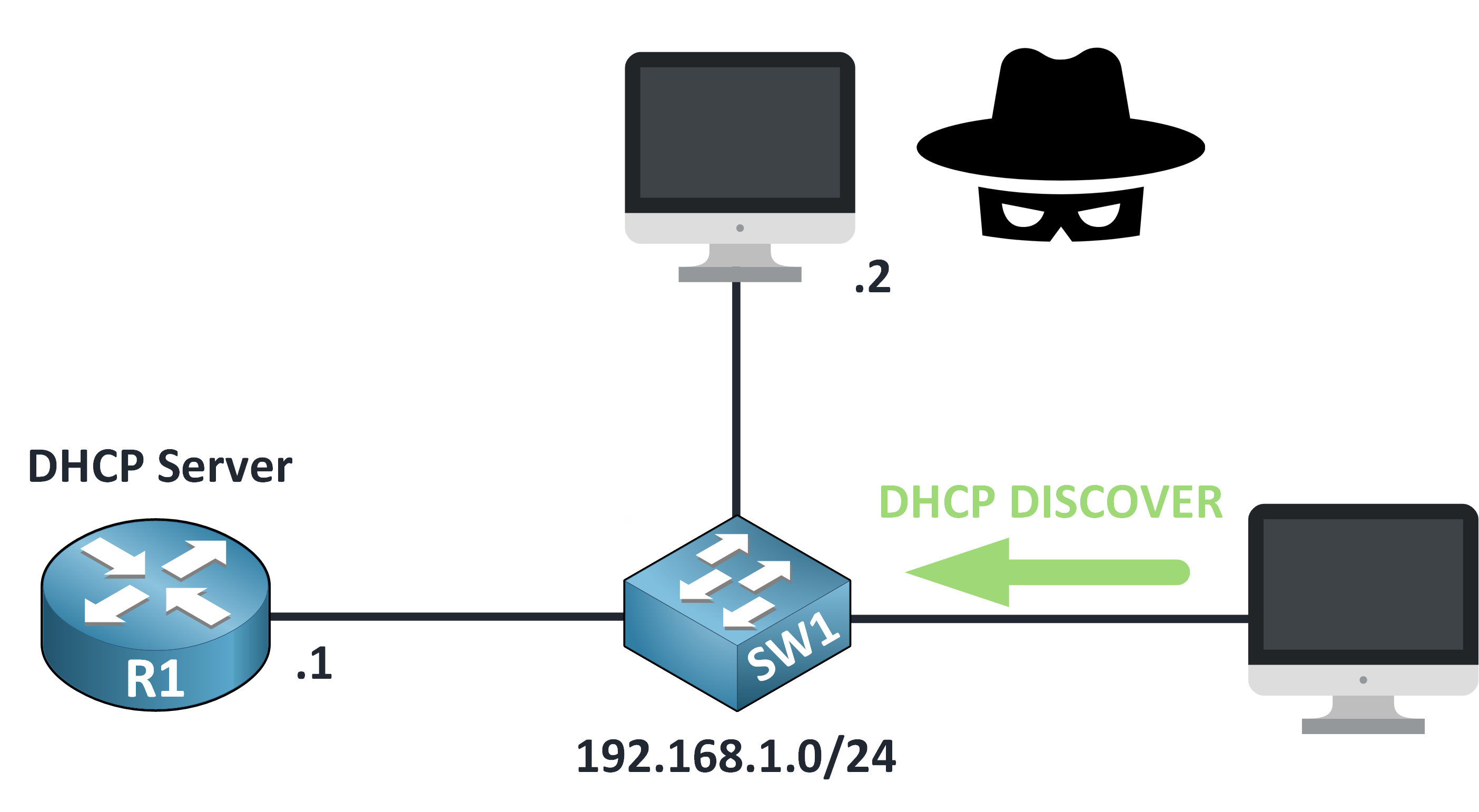
Figure 4 – DHCP Discover in a Man-in-the-Middle Attack
It’s like asking: “Is there a DHCP server out there that can give me an IP address?”
At this point, everything is normal, the device simply broadcasts its request to the entire local network.
Step 2 – Rogue Server Joins In
The DISCOVER message reaches both the legitimate DHCP server and a rogue device pretending to be one.
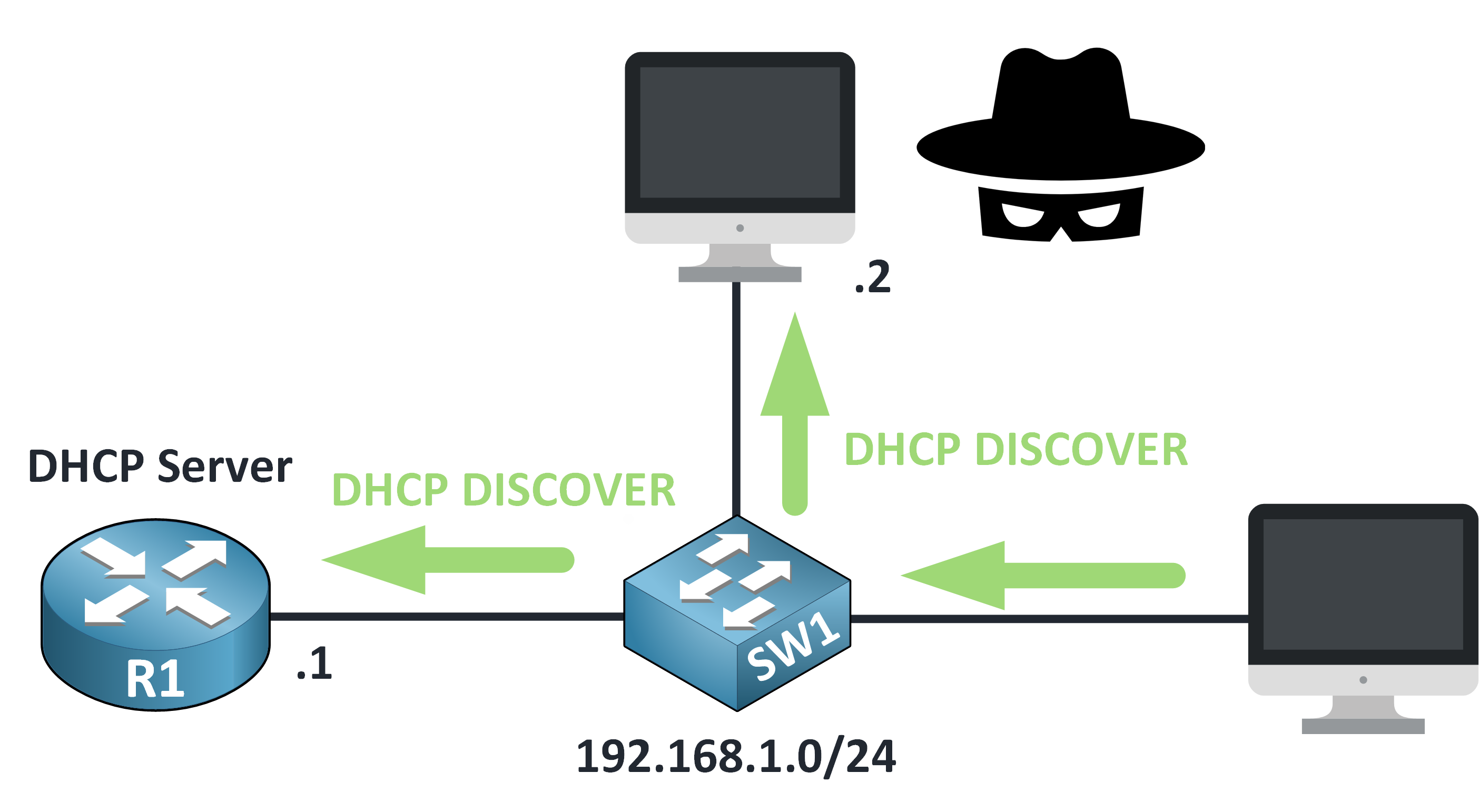
Figure 5 – DHCP Discover Reaches All Devices
That rogue server quickly responds with a fake DHCP OFFER.
Step 3 – First Come, First Served
Both servers reply with a DHCP OFFER.
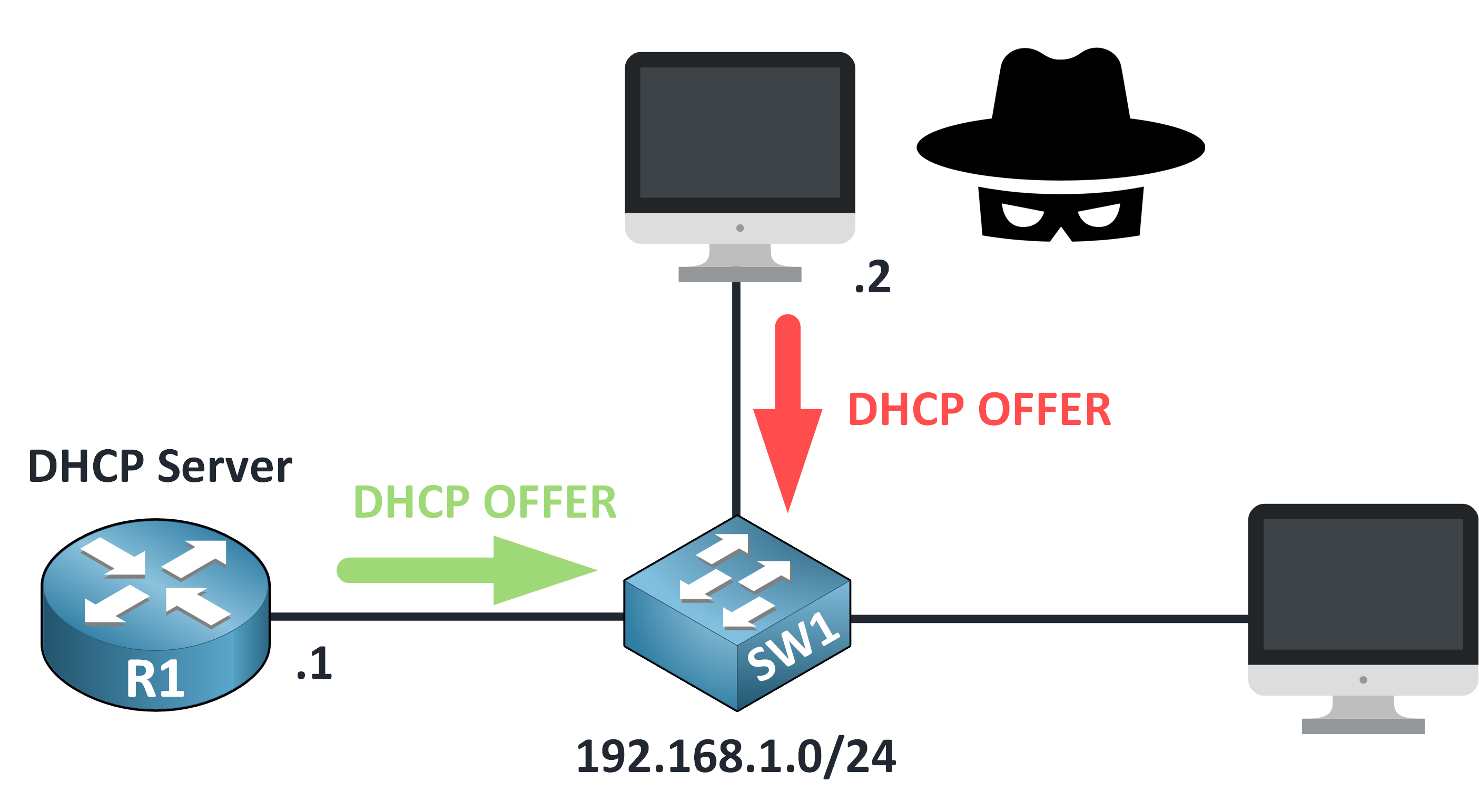
Figure 6 – Competing DHCP Offers: Legitimate vs Rogue
The client will usually accept whichever offer arrives first and that’s often the rogue one.
Step 4 – Malicious Offer Accepted
The client receives the rogue DHCP OFFER first and accepts it.
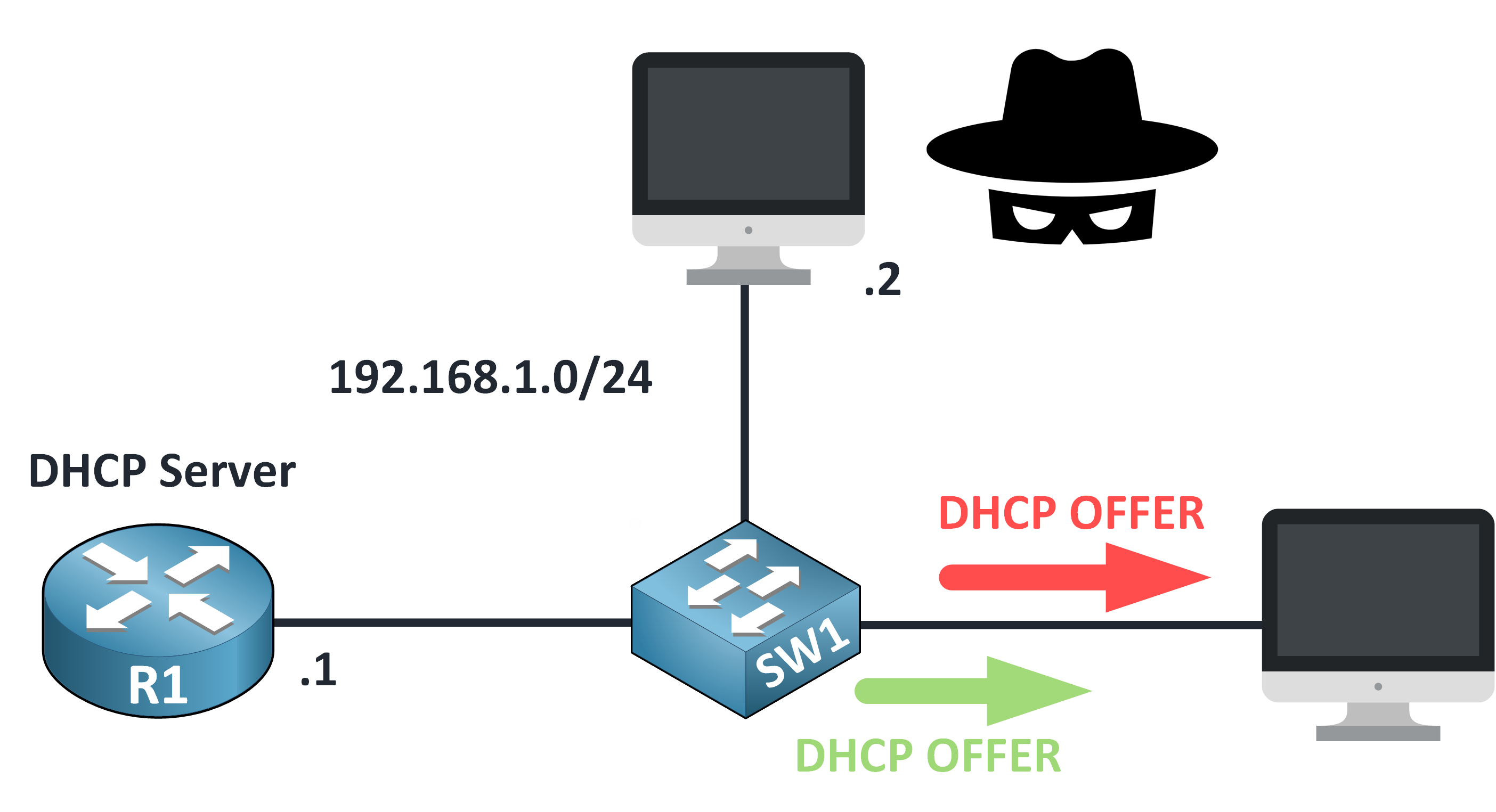
Figure 7 – Rogue DHCP Offer Accepted by Client
Step 5 – DHCP Request Sent
The device confirms its choice by sending a DHCP REQUEST to the rogue server.
It unknowingly agrees to use malicious network settings.
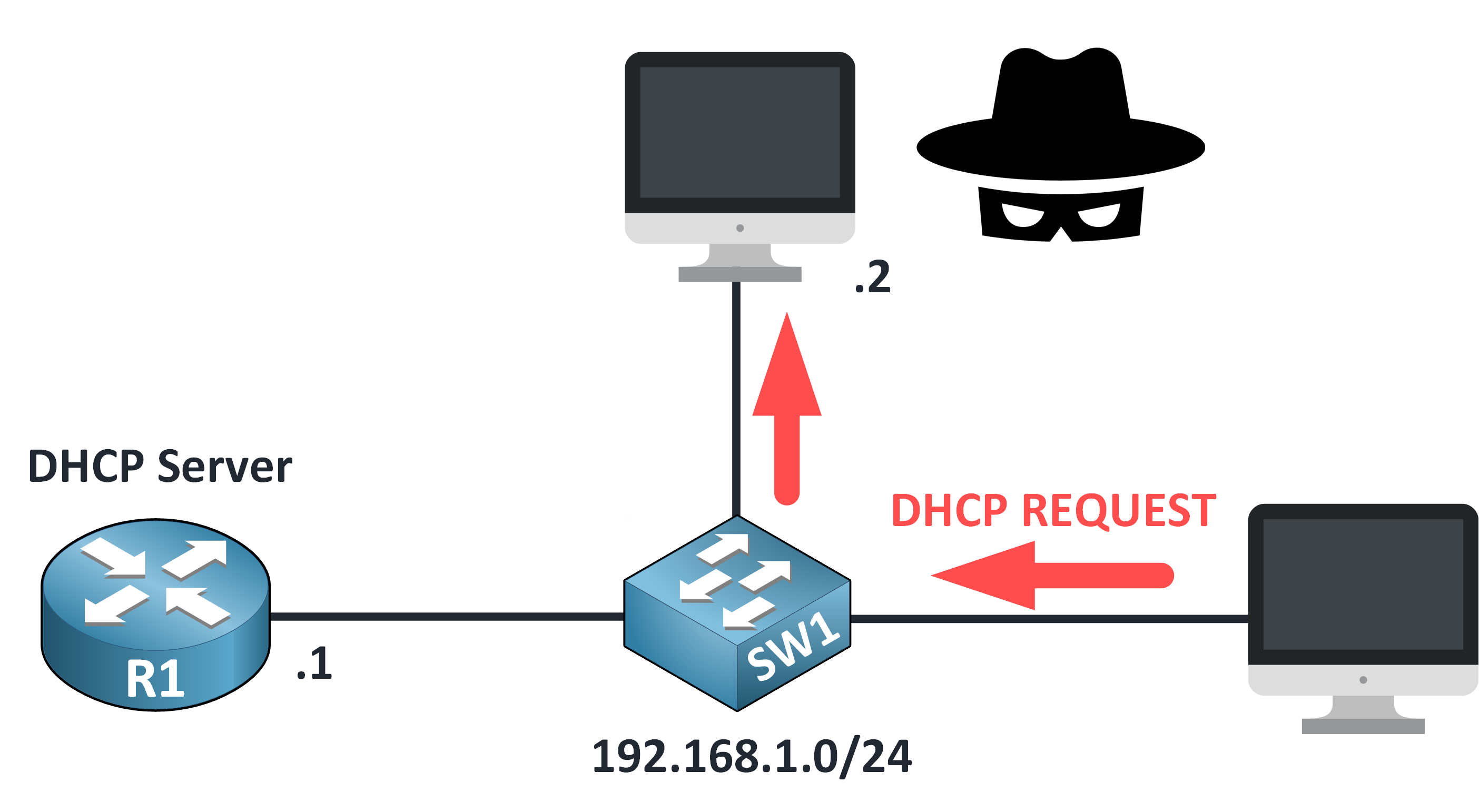
Figure 8 – DHCP Request Sent to Rogue Server
Unfortunately, the device it has no way of knowing that it just accepted settings from a malicious server.
At this point, the rogue server has successfully tricked your device with a malicious IP configuration.
Step 6 – Configuration Completed
The rogue server replies with a DHCP ACK, assigning:
An IP address
A subnet mask
A default gateway pointing to the attacker’s device
DNS server(possibly malicious too)
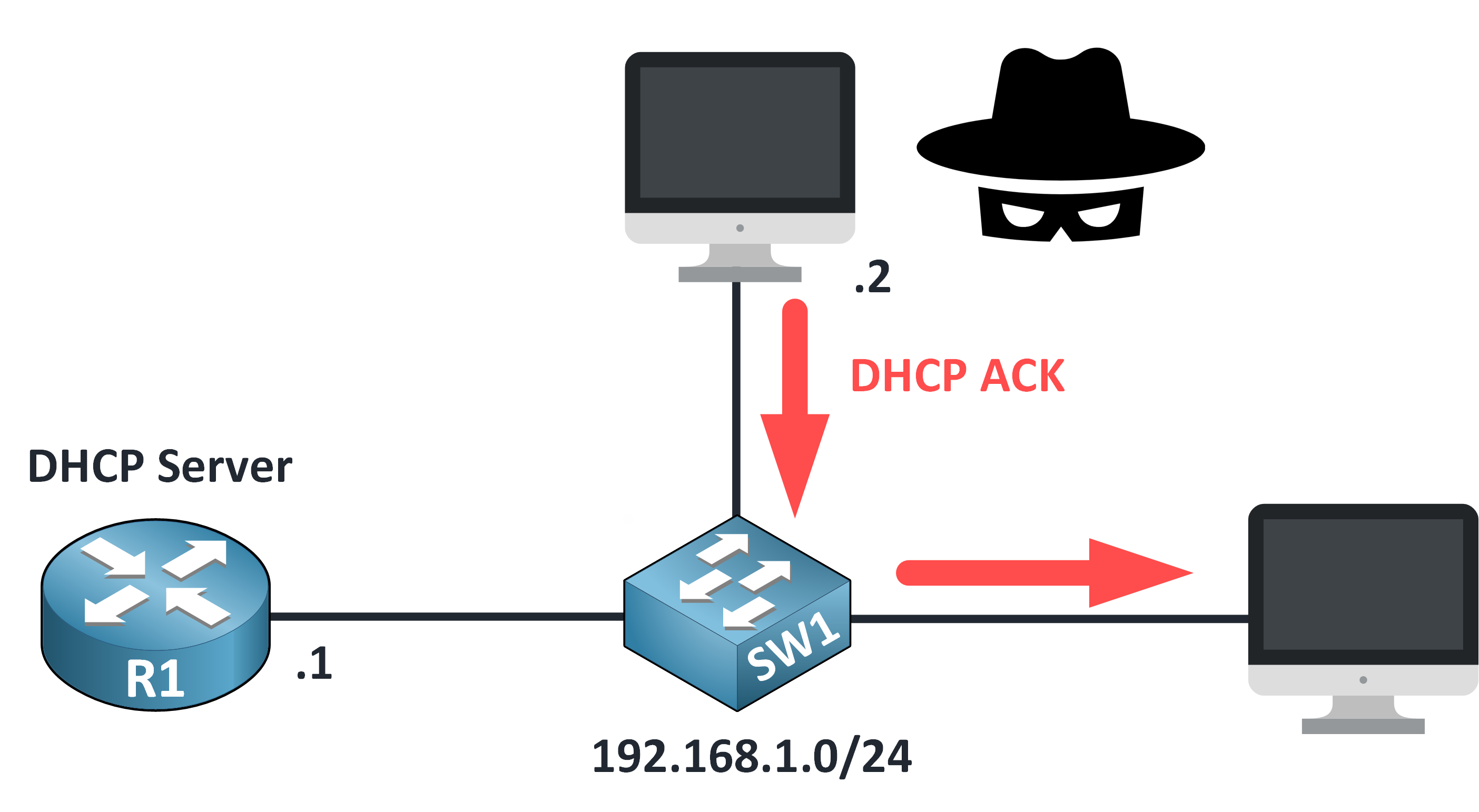
Figure 9 – Rogue Server Confirms Configuration with DHCP ACK
Step 7 - Man In The Middle Attack
From now on, all your device’s traffic is routed through the attacker.
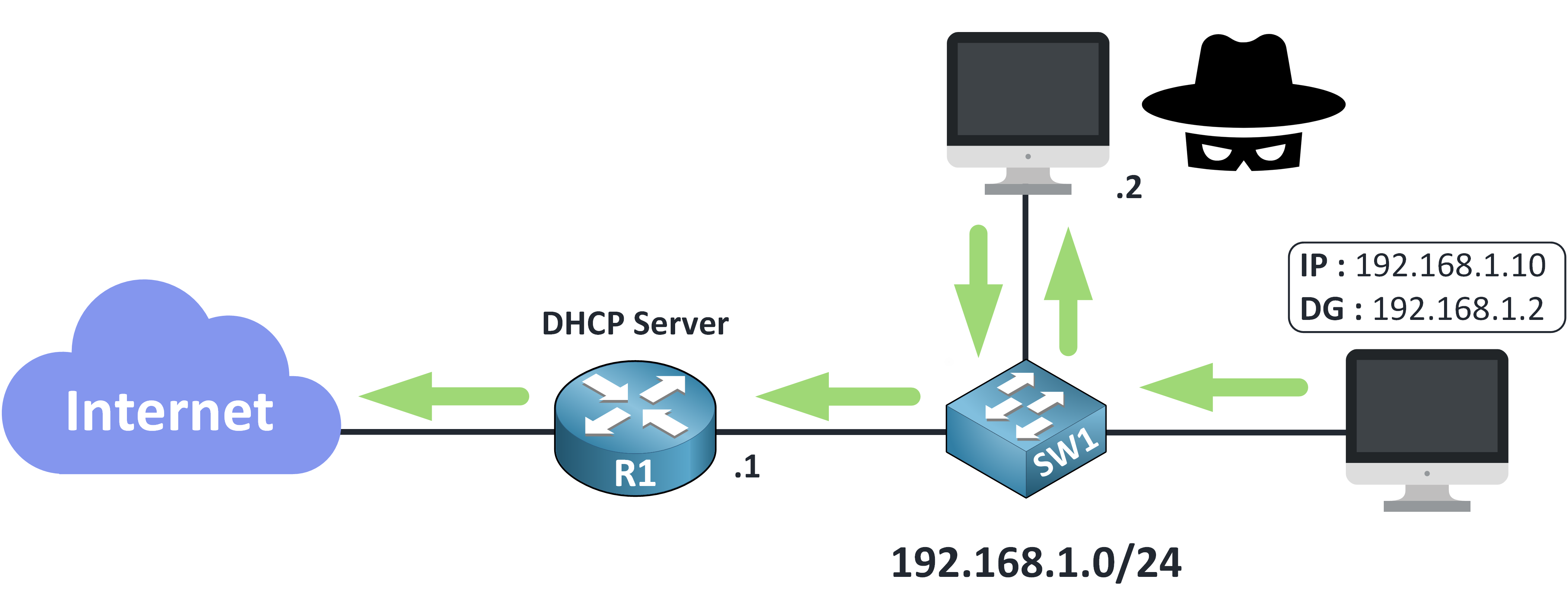
Figure 10 – All Traffic Routed Through the Attacker
Every packet sent by your device now passes through the rogue server before reaching its destination.
From here, the attacker can:
Intercept your data: They can capture sensitive information like passwords.
Manipulate your traffic: For example, redirecting you to fake websites that look legitimate.
This is a classic example of a Man-in-the-Middle attack demonstrates how DHCP can be abused to compromise a network.
DHCP Starvation Attack
Unlike a Man-in-the-Middle attack, the goal here isn't to intercept traffic, it's to exhaust all available IP addresses so that legitimate users can't connect to the network.
Flooding the Server
The attacker begins by sending hundreds or thousands of DHCP DISCOVER messages in a very short time.
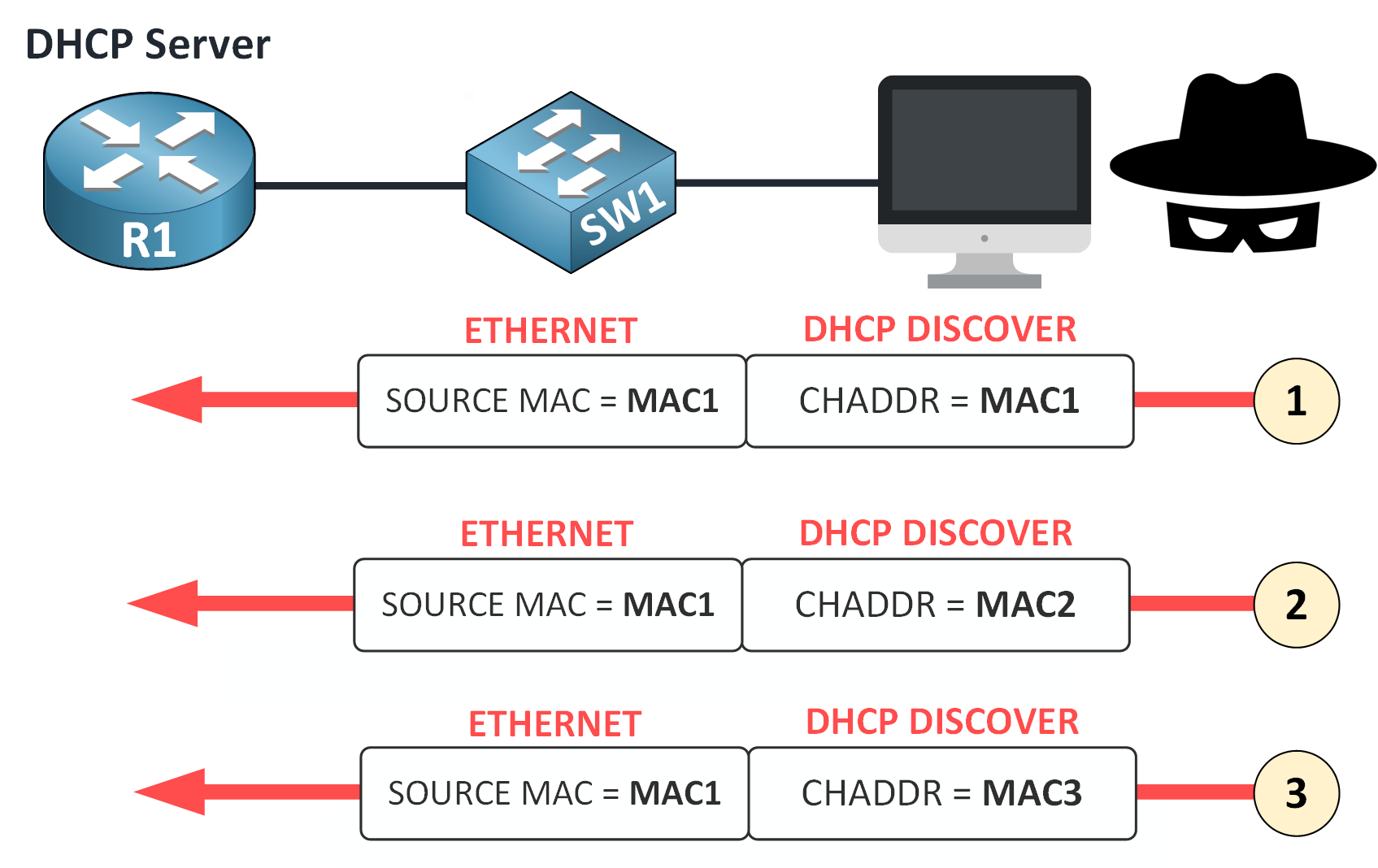
Figure 11 – DHCP Starvation via MAC Spoofing
Let’s break this down:
The attacker’s device uses a single physical MAC address (example MAC1).
In each DHCP DISCOVER message, it spoofs a different client MAC address in the
chaddrfield of the DHCP header.The DHCP server believes each message is from a unique client and assigns an IP address for each one.
Eventually, the server’s IP address pool is completely depleted.
The Result of the Attack
Once the DHCP pool is exhausted, any new legitimate device trying to join the network will be denied access.
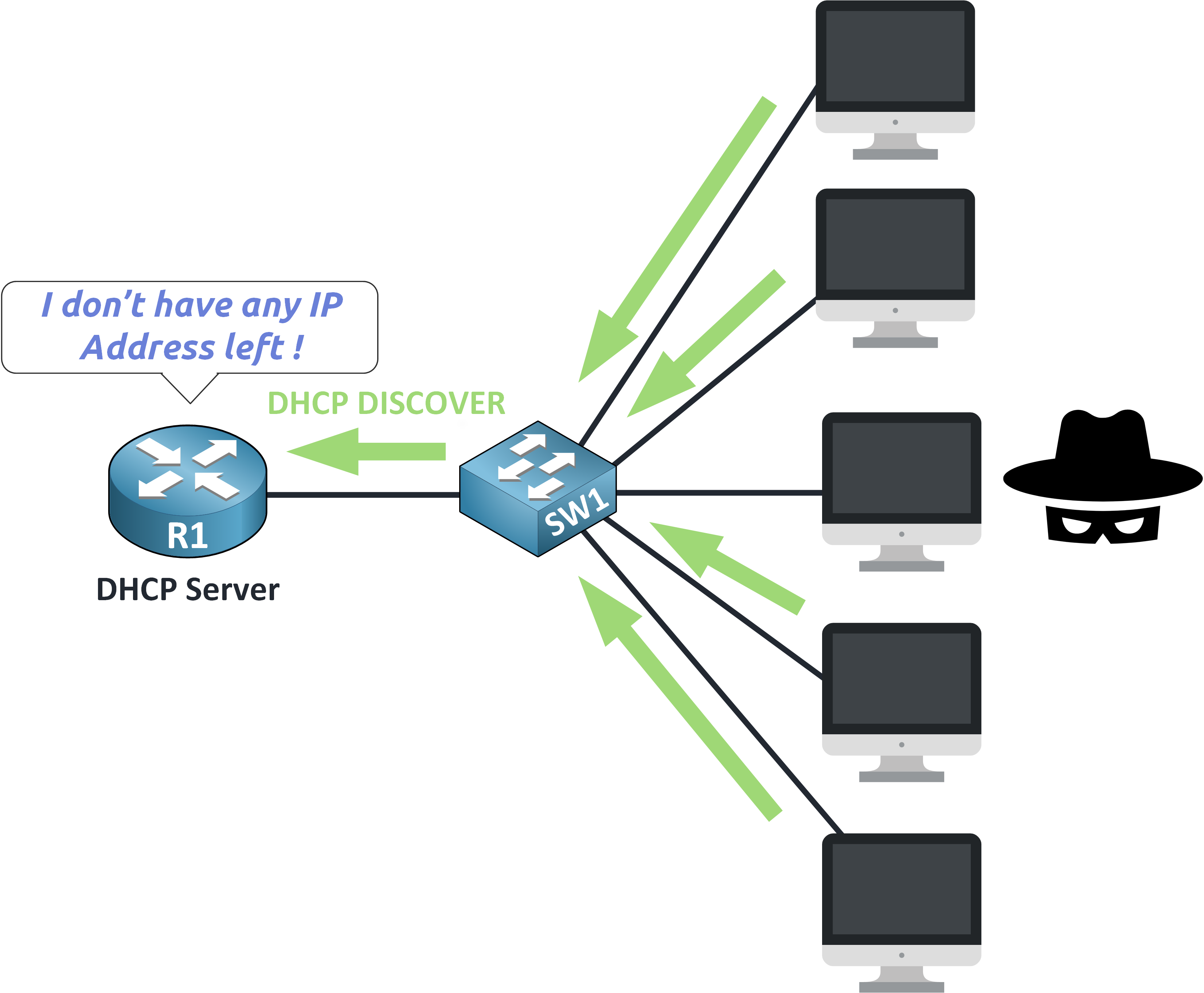
Figure 12 – Legitimate Clients Denied Access After Starvation
What happens now?
Legitimate clients send DHCP DISCOVER messages but receive no response.
They fail to obtain IP addresses, and can’t join the network.
Users experience connectivity loss, even though the network infrastructure is up.
Now that you’ve seen how DHCP can be abused, let’s move on to how DHCP Snooping prevents these attacks and protects your network.
3. DHCP Snooping Operation
DHCP Snooping acts like a firewall for DHCP traffic, it watches what comes in, checks if it’s trusted, and blocks anything suspicious.
Let’s break down how this protection works.
Trusted vs Untrusted Areas
To apply security rules effectively, the switch must separate the network into two areas:
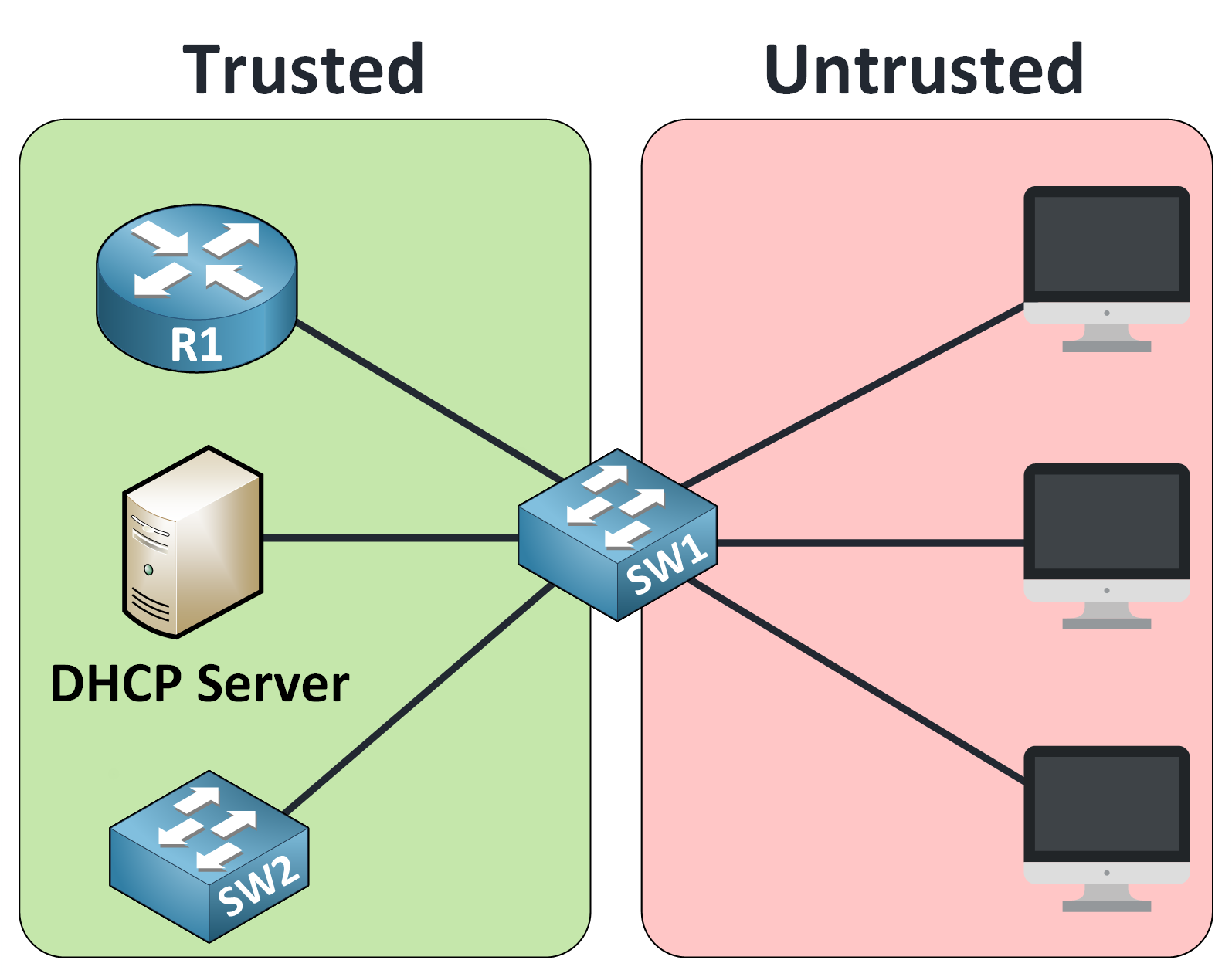
Figure 13 – Trusted vs Untrusted Areas
🟩 Trusted Area This includes interfaces that connect to known, secure devices like your DHCP server or router.
🟥 Untrusted Area
This covers ports used by end-user devices, where rogue DHCP servers could appear.
DHCP Message Filtering on Ports
Once ports are classified, the switch applies strict rules:
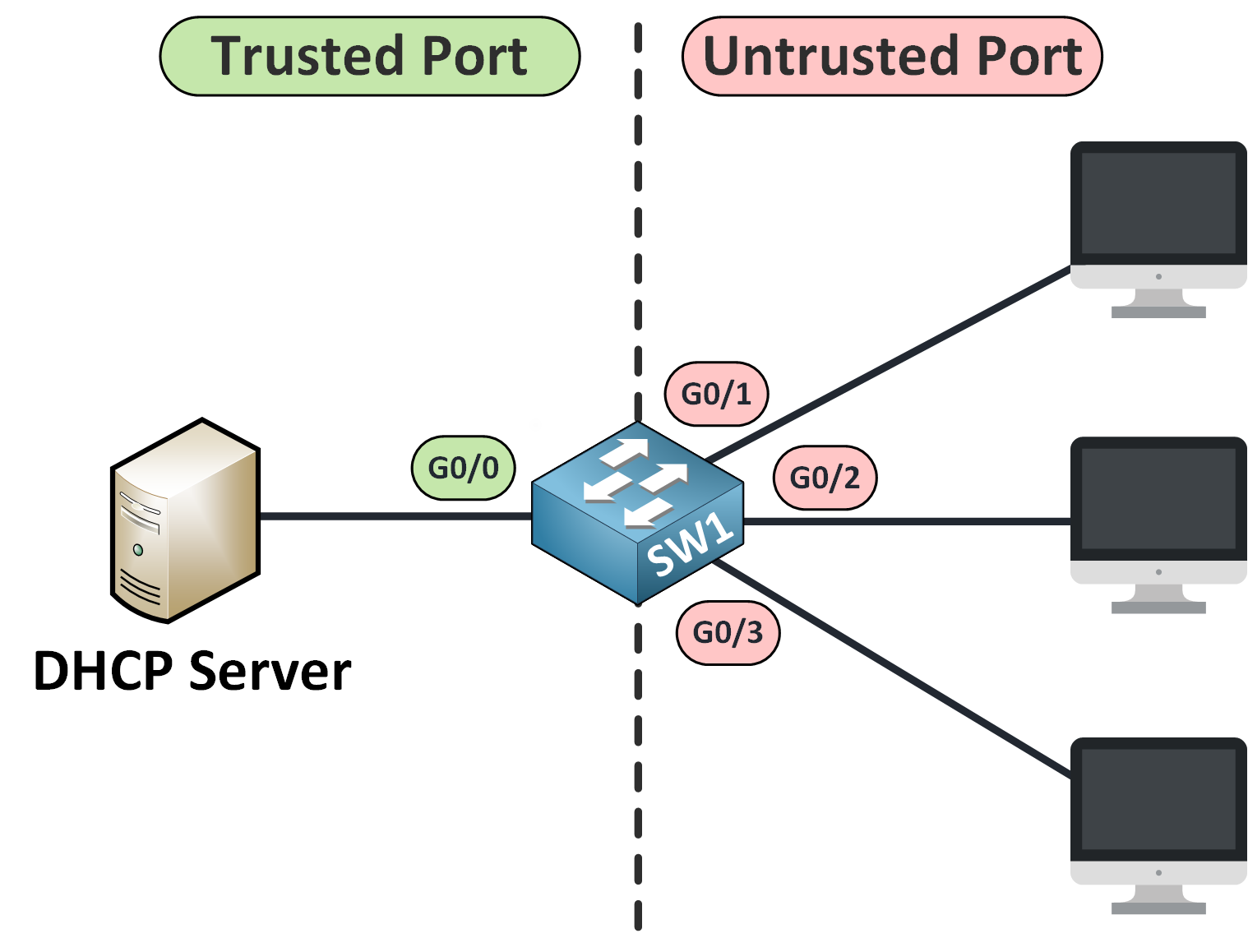
Figure 14 – DHCP Message Filtering on Trusted vs Untrusted Ports
✅ On Trusted Ports
All DHCP messages are allowed: DISCOVER, OFFER, REQUEST, ACK, etc.
These come from your legitimate DHCP server.
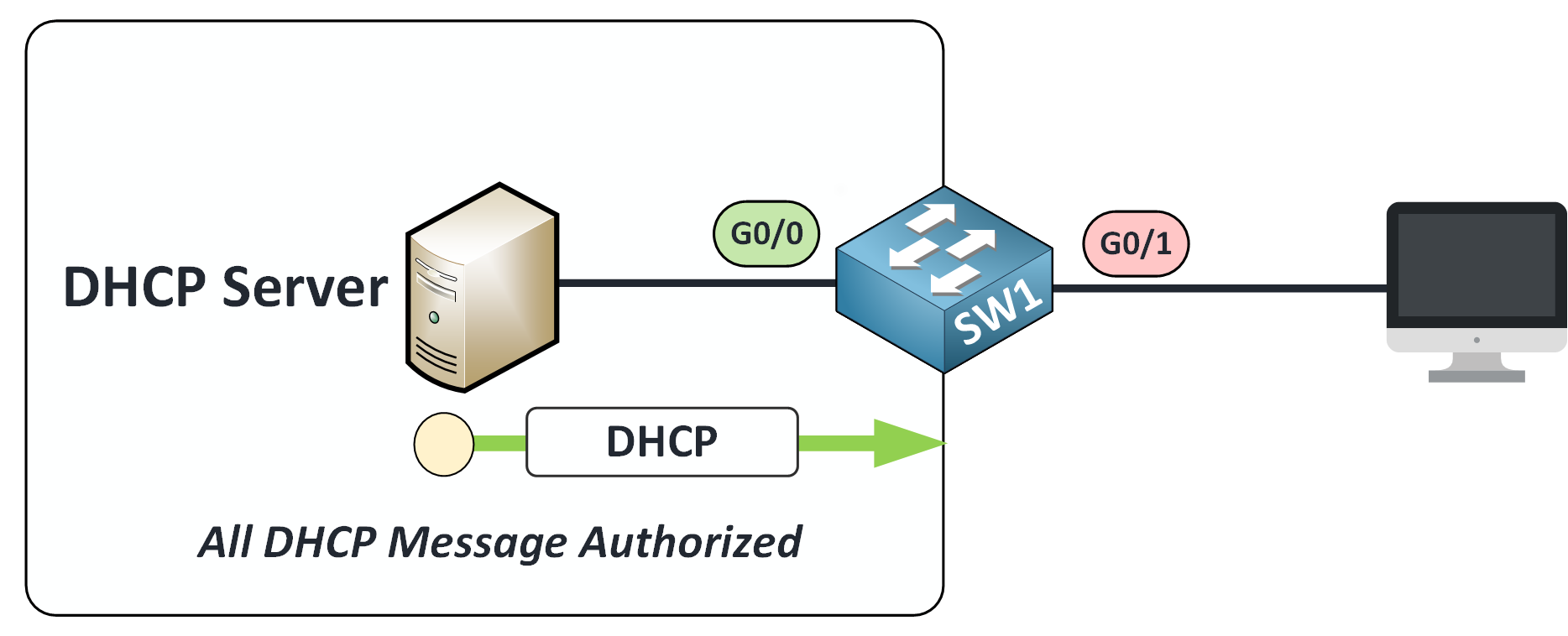
Figure 15 – DHCP Allowed on Trusted Ports
🚫 On Untrusted Ports
Only client messages (like DISCOVER or REQUEST) are allowed.
Server-type messages (OFFER, ACK, NAK) are blocked.
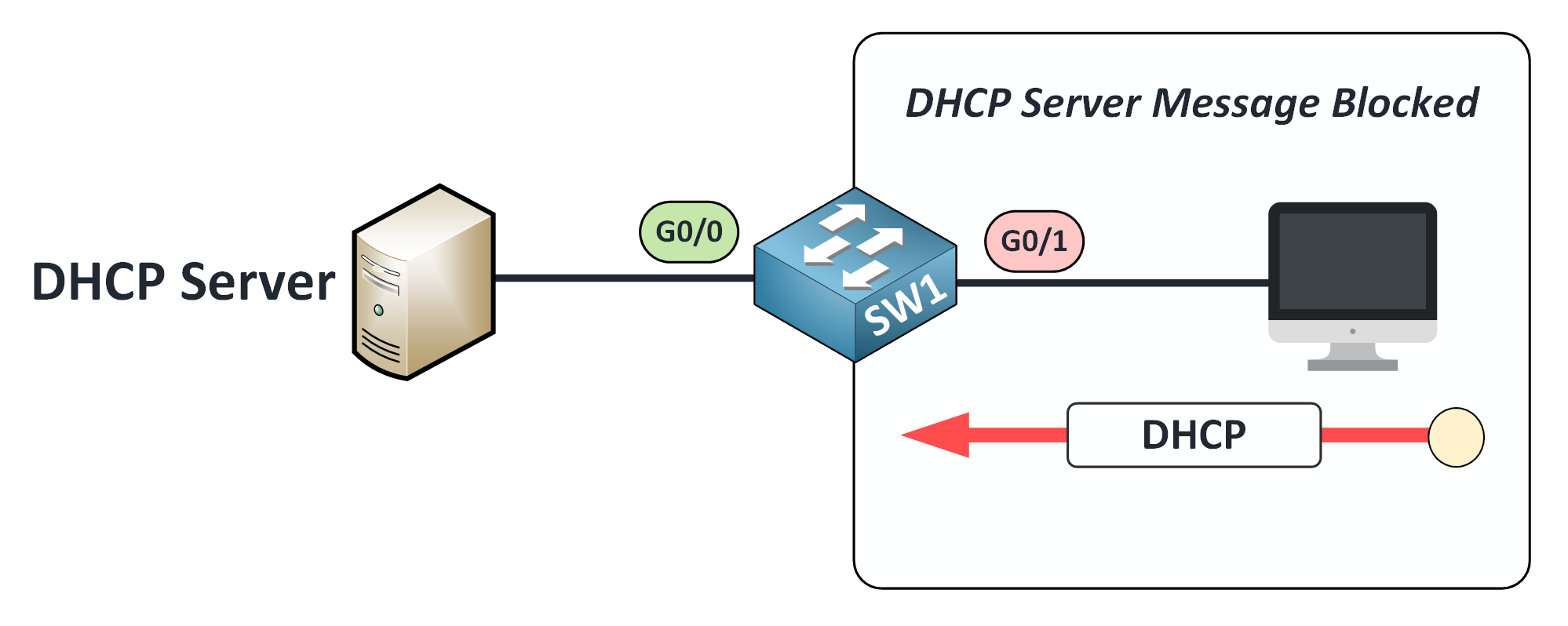
Figure 16 – DHCP Server Messages Blocked on Untrusted Ports
This blocks rogue DHCP servers from assigning fake IP settings.
DHCP Snooping Checks for Starvation Attacks
Now, what about DHCP Starvation?
DHCP Snooping inspects all DHCP DISCOVER messages arriving on untrusted ports.
Here’s the trick:
It compares the MAC address in the Ethernet frame with the CHADDR field in the DHCP header.
If they don’t match, that’s a sign of spoofing and the switch drops the packet.
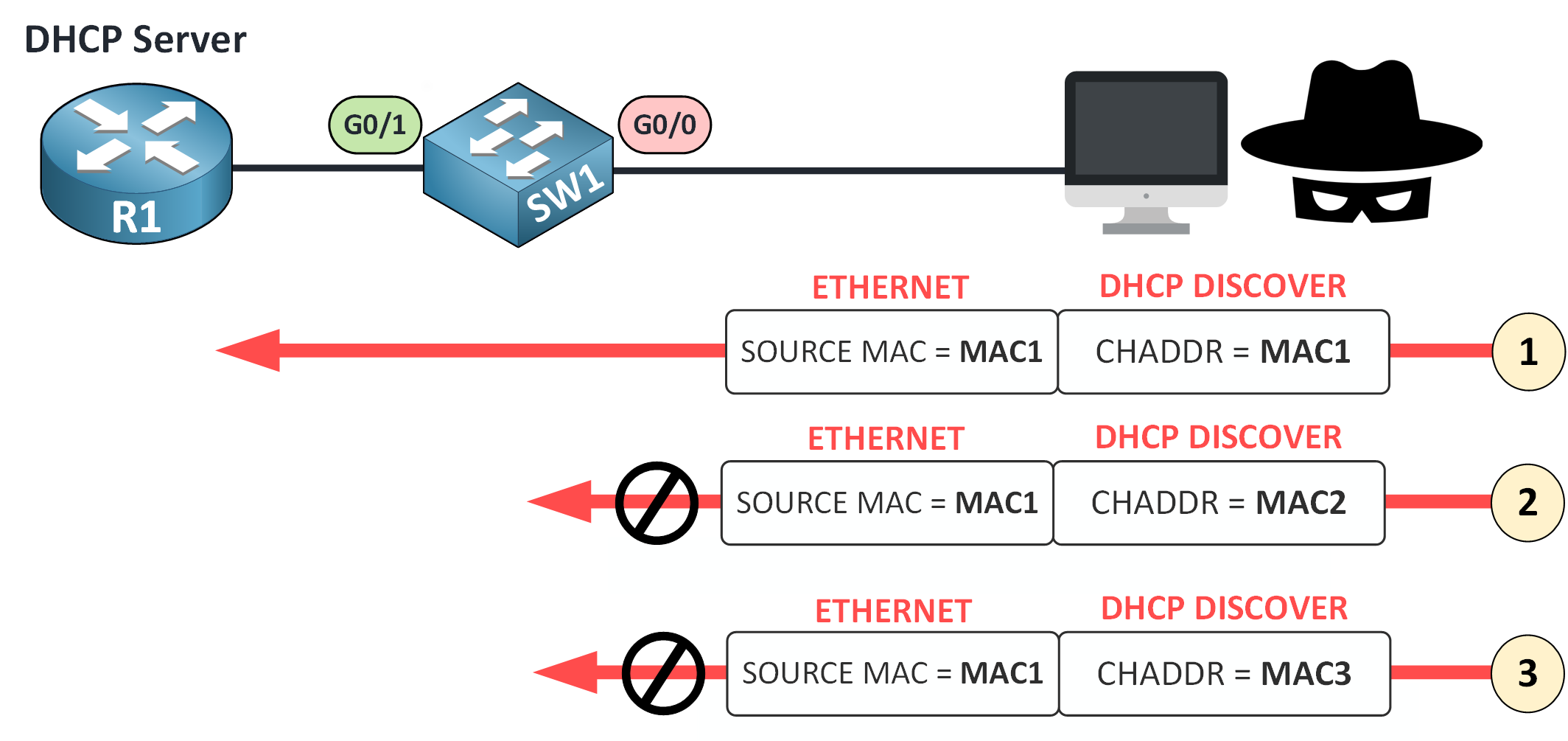
Figure 17 – DHCP Snooping Prevents Starvation with MAC Validation
This simple validation stops attackers from flooding the IP pool with fake clients.
DHCP Snooping Binding Table
As DHCP traffic is validated, the switch builds a binding table, a dynamic database of all legitimate DHCP clients.
Each entry contains:
MAC address
IP address
Port and VLAN
Lease time
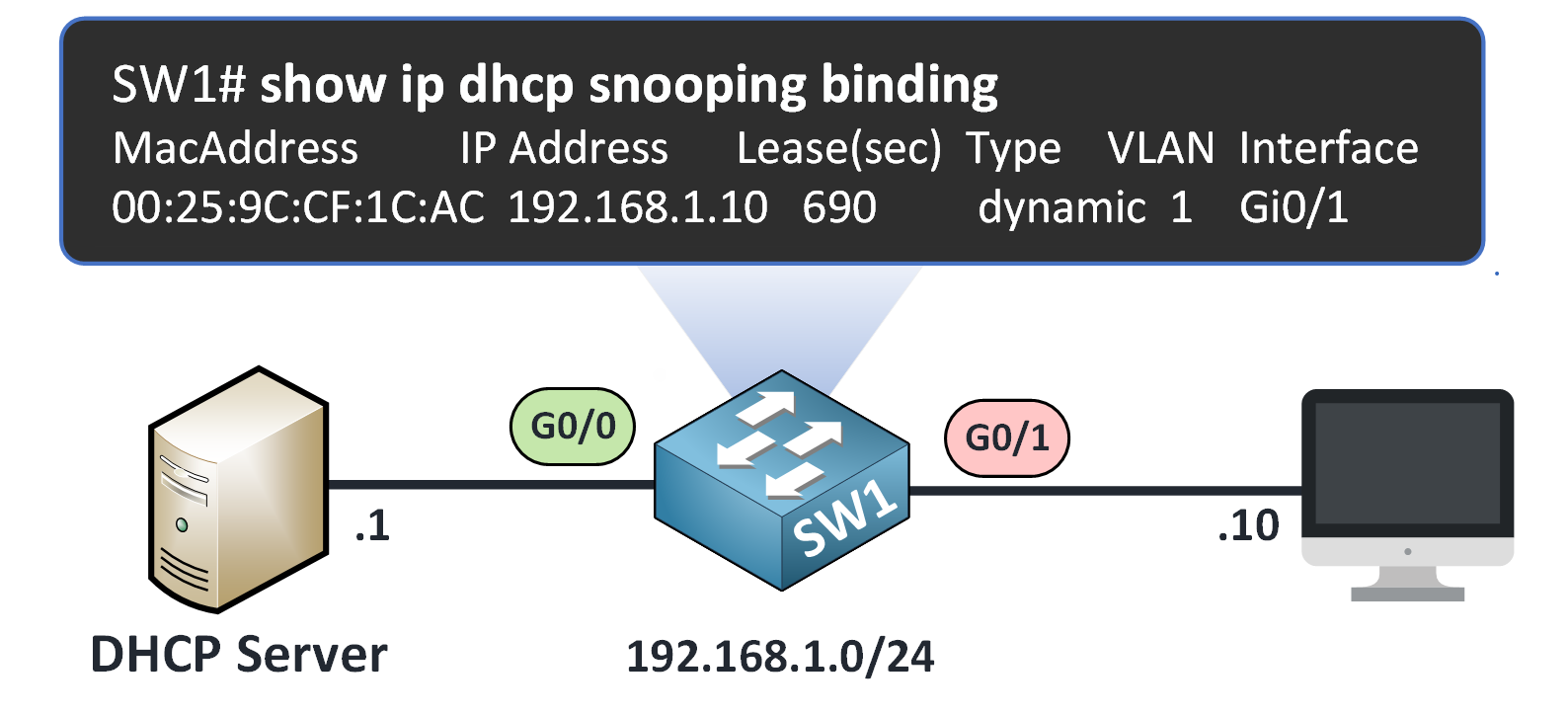
Figure 18 – DHCP Snooping Binding Table
This feature helps administrators verify active DHCP clients on the switch.
4. Conclusion
Let’s quickly recap:
DHCP vulnerabilities can lead to Man-in-the-Middle attacks and DHCP Starvation, both of which can severely impact your network’s integrity and availability.
DHCP Snooping mitigates these threats by:
Dividing the network into trusted and untrusted zones
Filtering unauthorized DHCP messages
Verifying DHCP message integrity
Dynamically tracking legitimate clients in a binding table
This protection is powerful but only if it’s properly configured.