Virtual Routing and Forwarding
Course Contents
1. Introduction to VRF
VRF (Virtual Routing and Forwarding) is a network virtualization technology that allows a router to have multiple independent routing tables.
Just like VLANs isolate traffic at Layer 2 by creating virtual switches, VRFs isolate routing domains at Layer 3 by creating virtual routers on a single physical device.
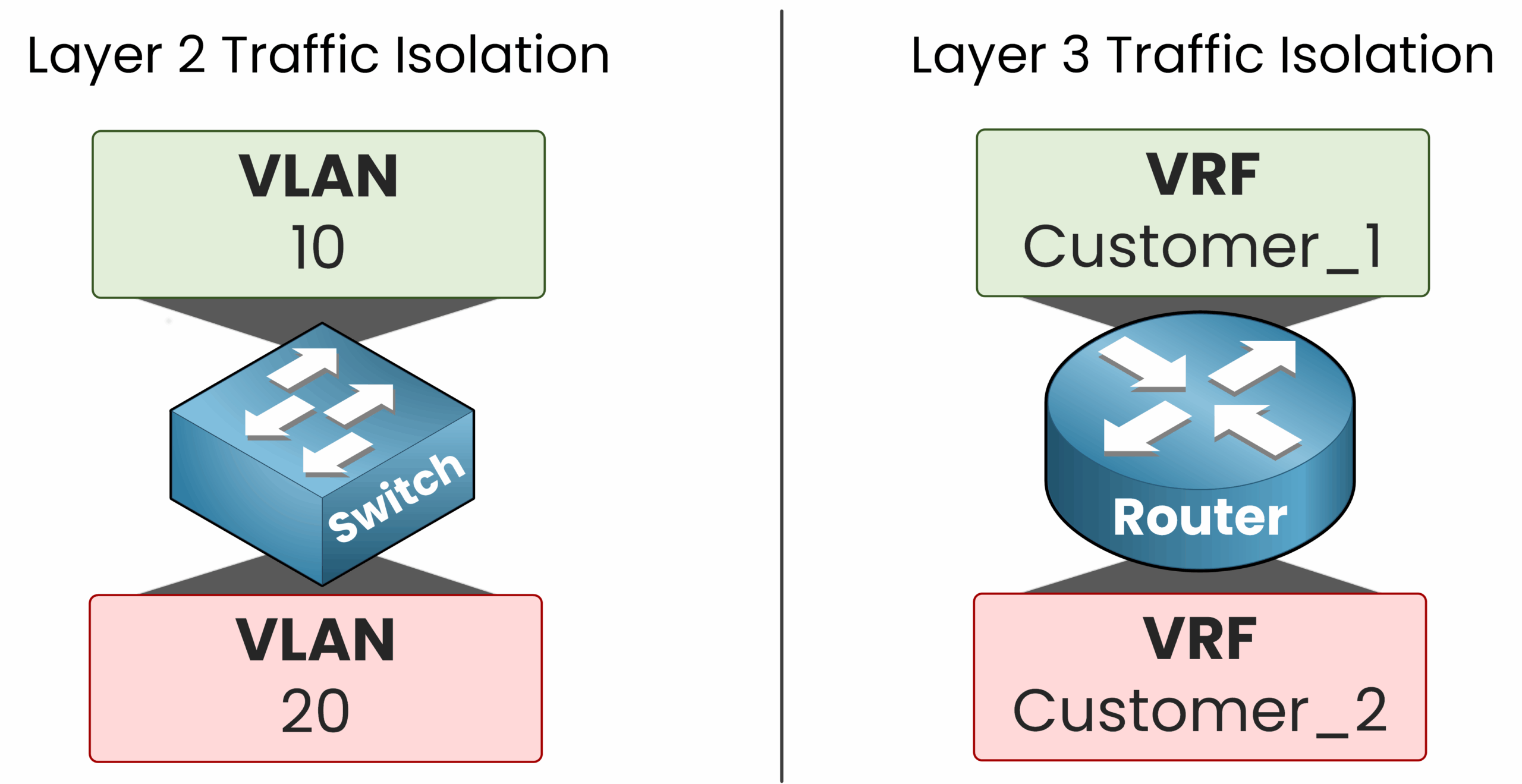
In this course, we’ll focus on VRF-Lite, a simplified version of VRF that does not use MP-BGP (Multiprotocol BGP) or MPLS (Multiprotocol Label Switching). This is the type of VRF you need to understand for the CCNA exam. To help you grasp its value, let’s walk through a real-world example.
2. Why a Single Routing Table Is a Problem
Imagine a Service Provider needs to connect two customers to the same ISP router.
As the diagram shows, both Customer 1 and Customer 2 need to access the internet through the ISP. But the network engineer is facing a key question:
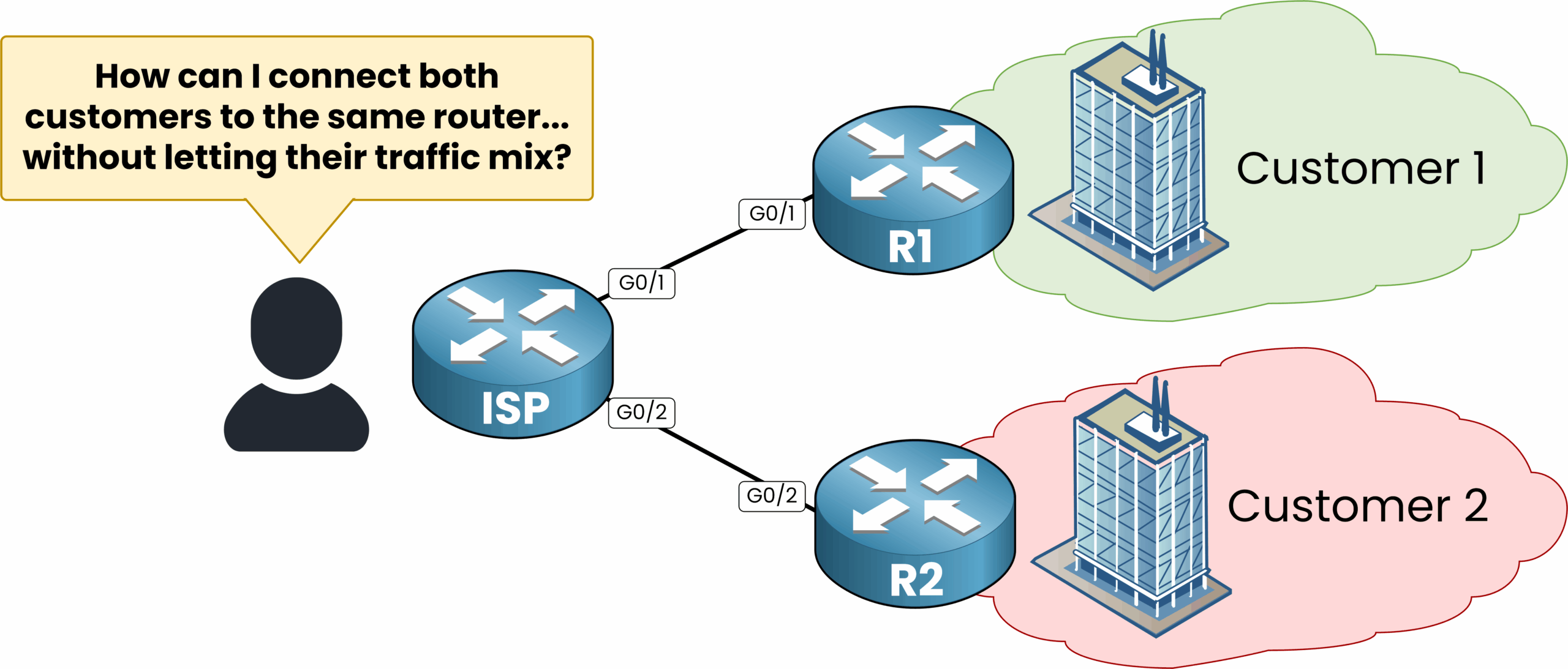
This is exactly the kind of question I want to guide you toward with this example to show you why VRFs are so valuable and how we can use them to our advantage.
By default, the ISP router uses a single global routing table.
As soon as both customers are connected to the Service Provider, the ISP router will learn the connected networks and will be inserted in the routing table.
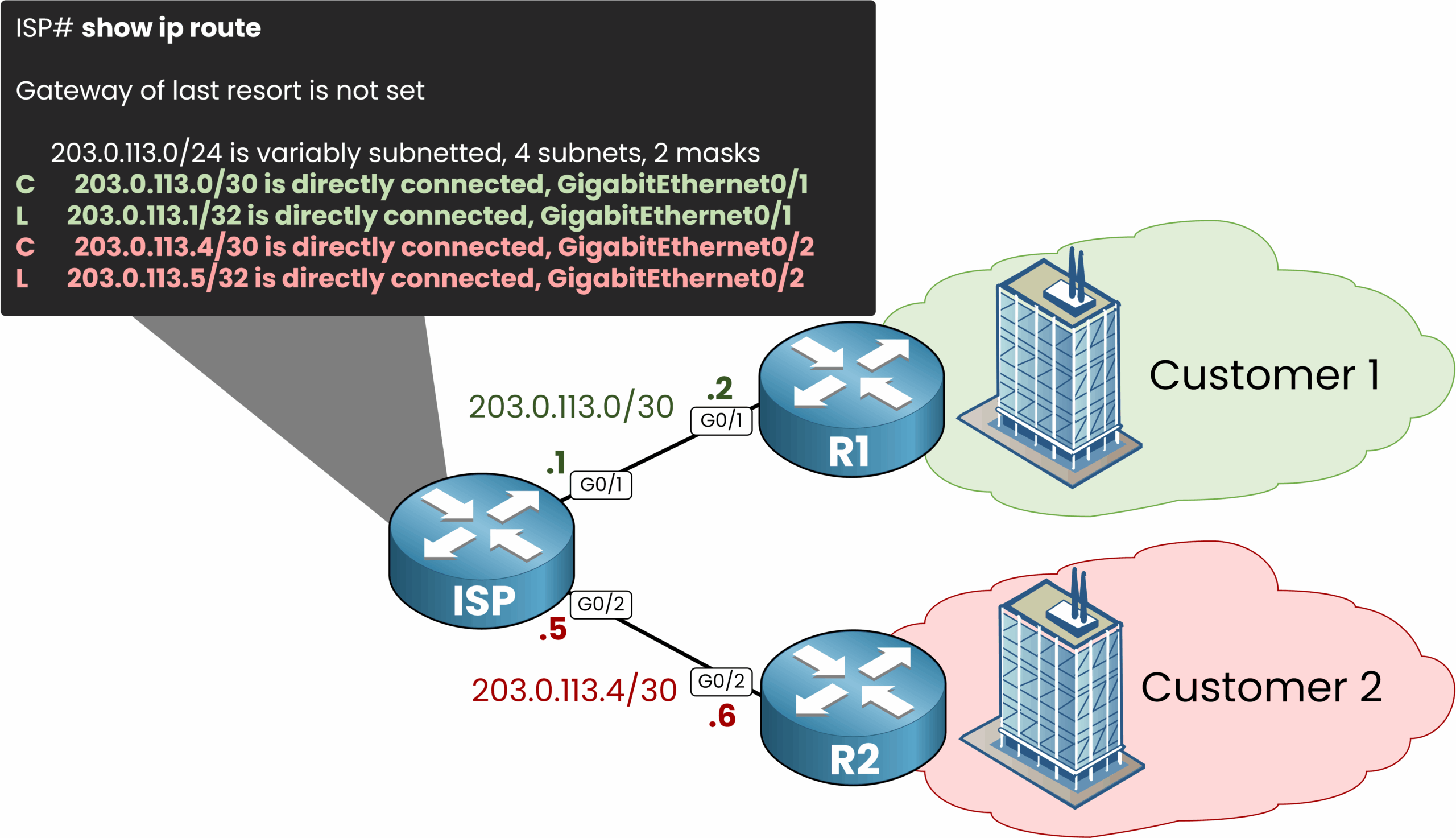
This leads to a serious risk of traffic leakage between customers, since the ISP router doesn’t distinguish between Customer 1 and Customer 2’s routes.
This means Customer 1 could potentially reach Customer 2’s network if we’re not careful, a serious security risk.
What we really need in this situation is a way to completely separate the routes used to reach Customer 1 from the routes used to reach Customer 2.
That way, each customer is fully isolated from the other. This is exactly what Virtual Routing and Forwarding (VRF) allows us to achieve.
3. How VRF Solves the Problem
With VRF, we can turn a single physical router into multiple virtual routers. In our example, we’ll create two virtual routing instances:
- One VRF named
CUSTOMER_1with its own routing table - One VRF named
CUSTOMER_2with its own routing table
Then, we assign the appropriate physical interfaces to each VRF.
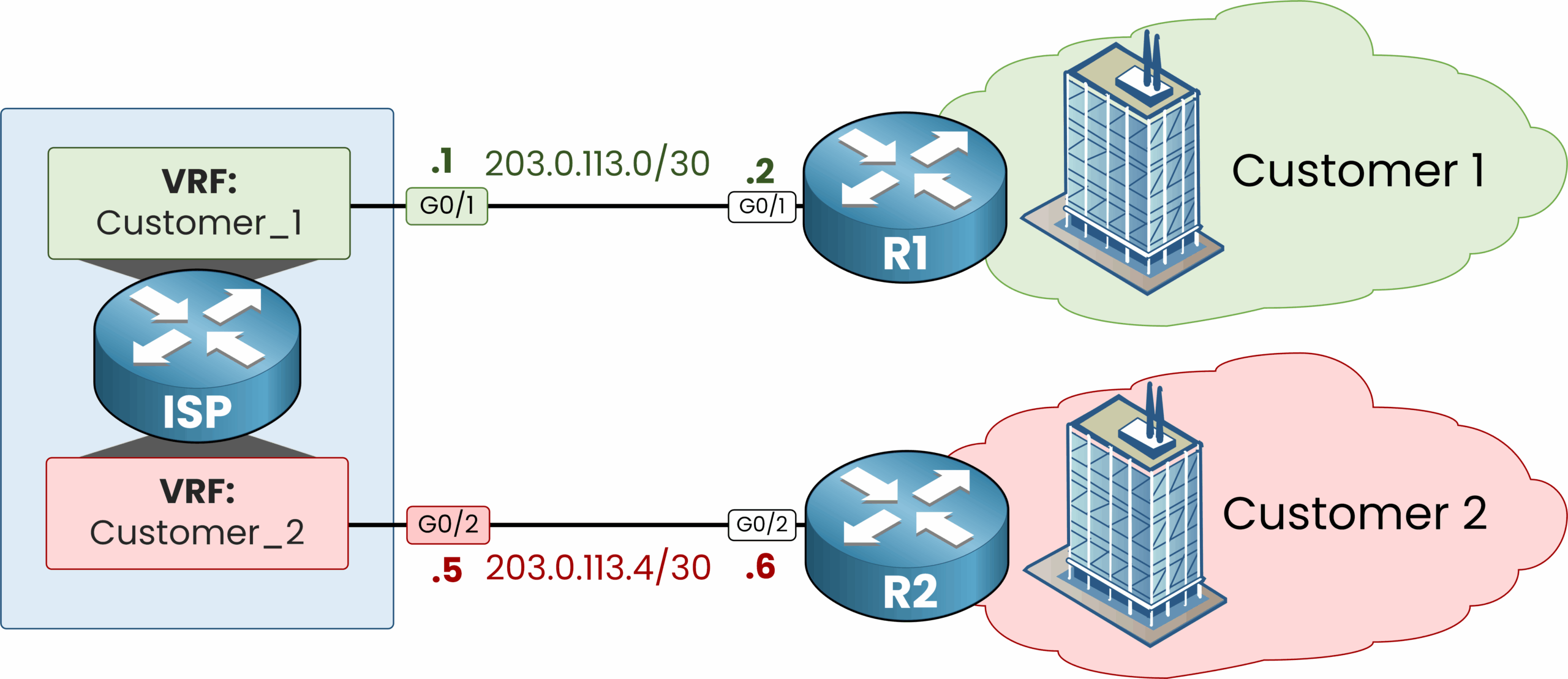
At this point, the ISP router hosts two independent routing environments:
- Each VRF has its own set of interfaces
- Each VRF has its own routing table
- And there is complete separation between the two
That’s all it takes. As shown above, each customer is now isolated within its own VRF.
This means Customer 1 and Customer 2 cannot see or reach each other, even though they’re using the same physical ISP router.
4. VRF Benefits
Virtual Routing and Forwarding comes with a lot of benefits that you should be aware especially for your CCNA study.
First, it’s the Independent Routing Tables.
Independent Routing Tables
Each VRF maintains its own routing table that is completely separated from others.
By default:
- Traffic from one VRF can’t reach another
- Routing entries and interfaces are fully isolated
We can look at the content of our 2 VRF by using the show ip route vrf vrf-name command:
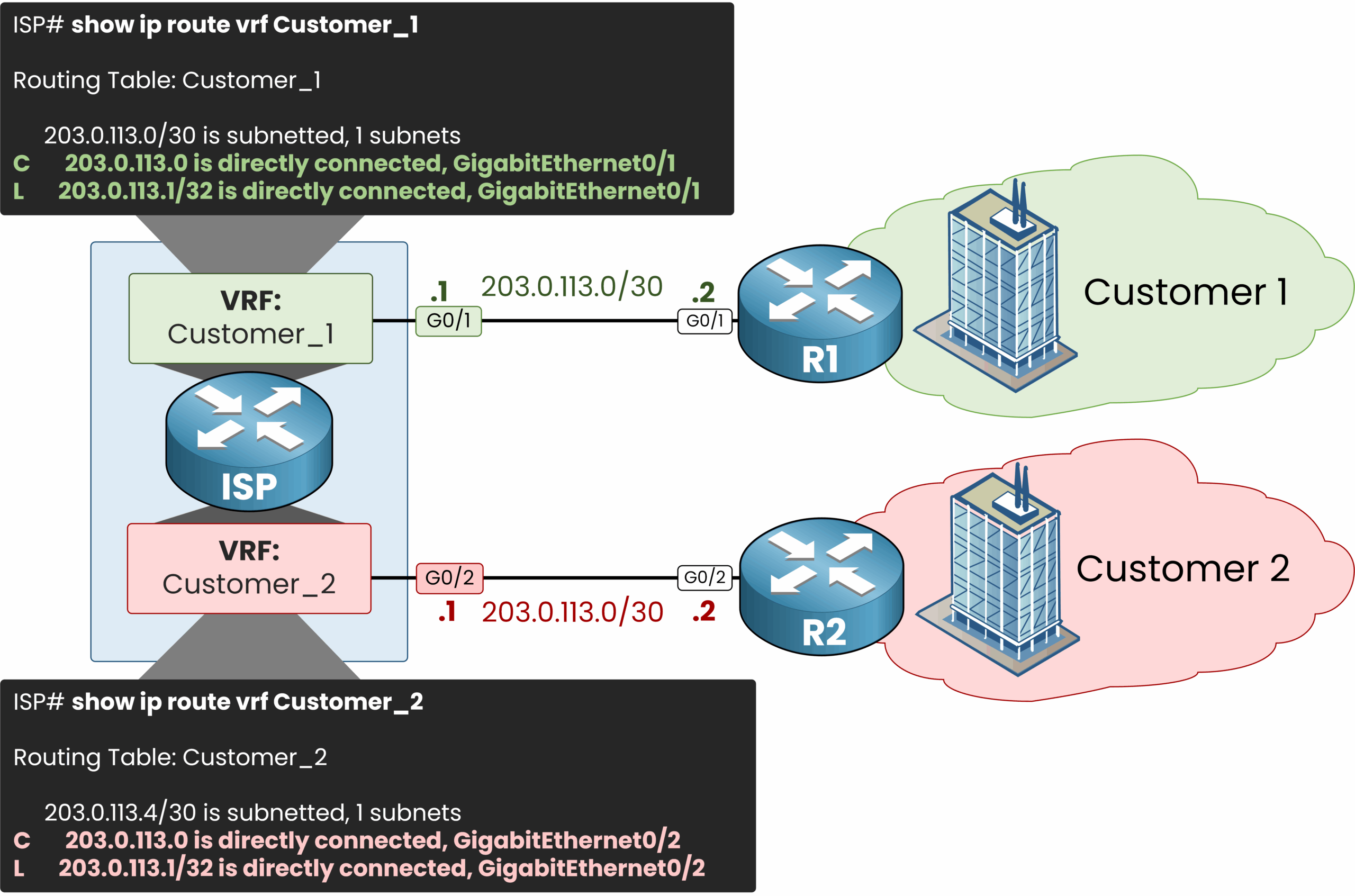
We can see that the VRF Customer_1 has the network 203.0.113.0/30 in its routing table. When we check the VRF Customer_2, we find the same subnet 203.0.113.0/30.
This illustrates one of the key benefits of VRF: the ability to reuse overlapping IP addresses without conflict.
Overlapping IP Addresses
One of the most useful benefits of VRF is that it allows IP address reuse across different customers without any conflict.
For example:
Customer_1uses the subnet203.0.113.0/30inside its VRFCustomer_2also uses203.0.113.0/30in its own VRF
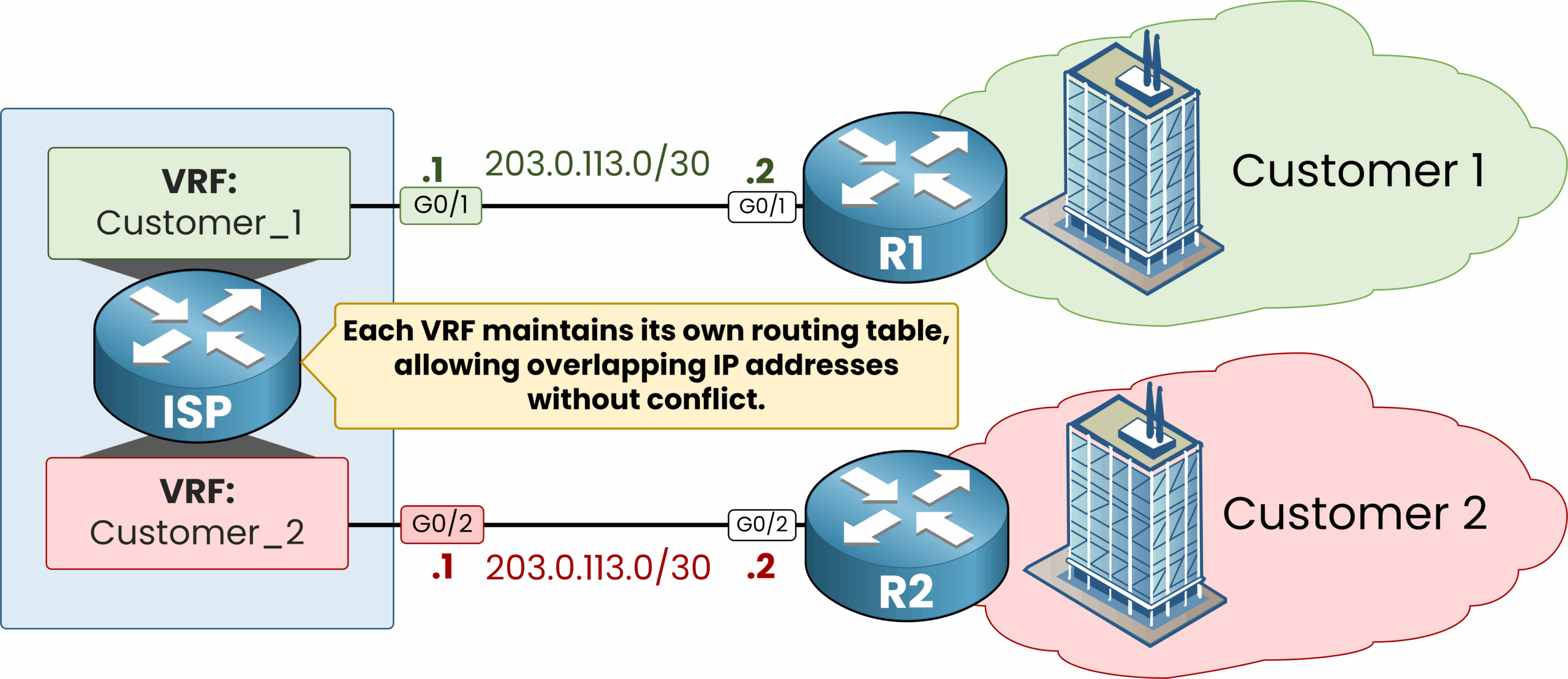
But how is that possible?
Because each VRF creates a completely isolated routing environment.
This means:
- Each VRF has its own routing table
- Each VRF has its own interfaces
- The router treats the same IP address differently depending on the VRF
So, even if both customers use the same IP subnet, the router knows which one to use because the traffic is bound to a specific VRF via the interface.
There’s no interference, and no confusion because from the router’s perspective, those IPs belong to two different virtual routers.
5. VRF Configuration on the ISP Router
After understanding the concept of overlapping IPs, let’s see how this works in a real configuration.
In the previous diagram (Figure 5), we saw a logical view of two customers using the same subnet without conflict. Now in Figure 6, we expand the topology to include remote customer routers (R3 and R4) and prepare the ISP router with two separate VRFs. This more complete topology will be used for the configuration examples that follow.
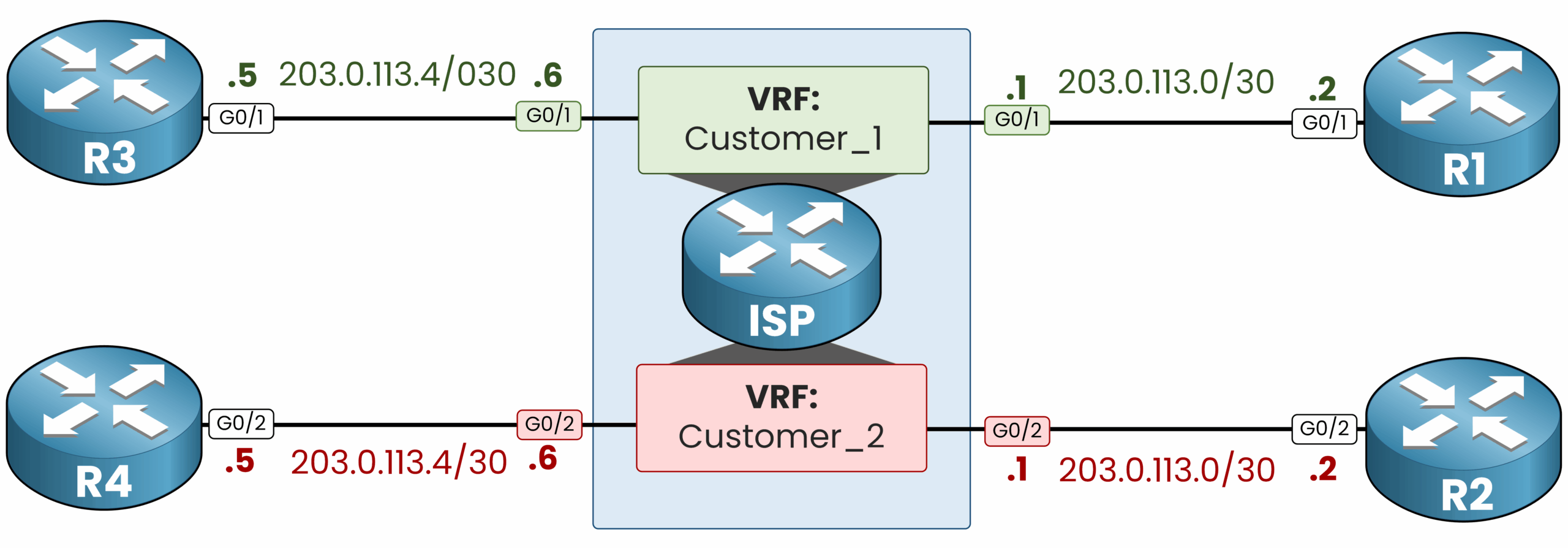
For your CCNA study, you don’t need to configure VRF Lite, nevertheless I think this can be a good point to view how it’s created in practice. The configuration is not really complicated.
The first step is to create our Virtual Routing and Forwarding table. Since we have 2 customers, we will create 2 VRFs.
STEP 1 – Create the VRFs
We begin by creating two virtual routing instances on the ISP router:
ISP(config)# ip vrf CUSTOMER_1 ISP(config)# ip vrf CUSTOMER_2
Each VRF acts like a separate logical router inside the same physical device.
STEP 2 – Assign Interfaces to Each VRF
We now assign the correct interfaces to each VRF and configure IP addresses.
Interfaces for CUSTOMER_1:
ISP(config)# interface g0/1 ISP(config-if)# ip vrf forwarding Customer_1 ISP(config-if)# ip address 203.0.113.1 255.255.255.252 ISP(config-if)# no shutdown ISP(config)# interface g1/0 ISP(config-if)# ip vrf forwarding Customer_1 ISP(config-if)# ip address 203.0.113.6 255.255.255.252 ISP(config-if)# no shutdown
Interfaces for CUSTOMER_2:
ISP(config)# interface g0/2
ISP(config-if)# ip vrf forwarding Customer_2}
ISP(config-if)# ip address 203.0.113.1 255.255.255.252
ISP(config-if)# no shutdown
ISP(config)# interface g2/0
ISP(config-if)# ip vrf forwarding Customer_2£
ISP(config-if)# ip address 203.0.113.6 255.255.255.252
ISP(config-if)# no shutdown
⚠️ Note: Make sure to always apply the
ip vrf forwarding vrf-namecommand before configuring the ip address on the interface. This command removes any existing IP address from the interface if the interface has already an IP configuration. Always configure the VRF first on the interface and then assign the IP address.
STEP 3 – Verify VRF Interface Assignment
By using the show ip vrf we can check VRFs and associated interfaces:
ISP# show ip vrf Name Default RD Interfaces Customer_1Gi0/1, Gi1/0 Customer_2 Gi0/2, Gi2/0
Here we can see the interface associated with each VRF.
STEP 4 – Check Routing Tables per VRF
Each VRF has a separate and isolated routing table.
We can check the content of each table using the command show ip route vrf vrf-name
ISP# show ip route vrf Customer_1
Routing Table: Customer_1
203.0.113.0/30 is subnetted, 1 subnets
C 203.0.113.0 is directly connected, GigabitEthernet0/1
L 203.0.113.1/32 is directly connected, GigabitEthernet0/1
C 203.0.113.4 is directly connected, GigabitEthernet1/0
L 203.0.113.6/32 is directly connected, GigabitEthernet1/0
ISP# show ip route vrf Customer_2
Routing Table: Customer_2
203.0.113.0/30 is subnetted, 1 subnets
C 203.0.113.0 is directly connected, GigabitEthernet0/2
L 203.0.113.1/32 is directly connected, GigabitEthernet0/2
C 203.0.113.4 is directly connected, GigabitEthernet2/0
L 203.0.113.6/32 is directly connected, GigabitEthernet2/0
As you can see, each VRF has its own routing table, with its own connected networks and interfaces.
Even though the subnets are identical, the router handles them as separate thanks to VRF.
6. Summary
VRF Lite is a powerful solution that allows a single physical router to behave like multiple virtual routers. This solves the challenge of route separation when multiple customers connect to the same ISP device.
- By default, a router uses a single global routing table, which introduces the risk of traffic leakage between customers. With VRF, each customer operates in a fully isolated routing environment. Every VRF has its own routing table and interfaces, and the router treats overlapping IP addresses as completely separate.
For example, both Customer 1 and Customer 2 can use the subnet 203.0.113.0/30 without conflict, because each subnet exists in its own VRF and is processed independently.
We also explored how to configure VRF Lite in practice. After creating the VRF instances, we assigned interfaces and configured IP addresses. Using commands like show ip vrf and show ip route vrf, we verified that each customer’s routing domain remains separated.
VRF Lite offers a simple and scalable way to isolate routing domains on the same device, an important concept to understand for the CCNA exam.
